Prerequisites
| Component | Description | Reference |
|---|---|---|
| GitOps Repo | solar-system-gitops-argo-cd in Gitea under dasher-org | |
| Argo CD App | solar-system-argo-app tracking the kubernetes directory | Argo CD Application |
| Jenkins Instance | Controller with credentials to push to Gitea | Jenkins Credentials |
1. Inspect the Manifest Repository
Open the Gitea reposolar-system-gitops-argo-cd and navigate to the kubernetes folder:

deployment.yml:
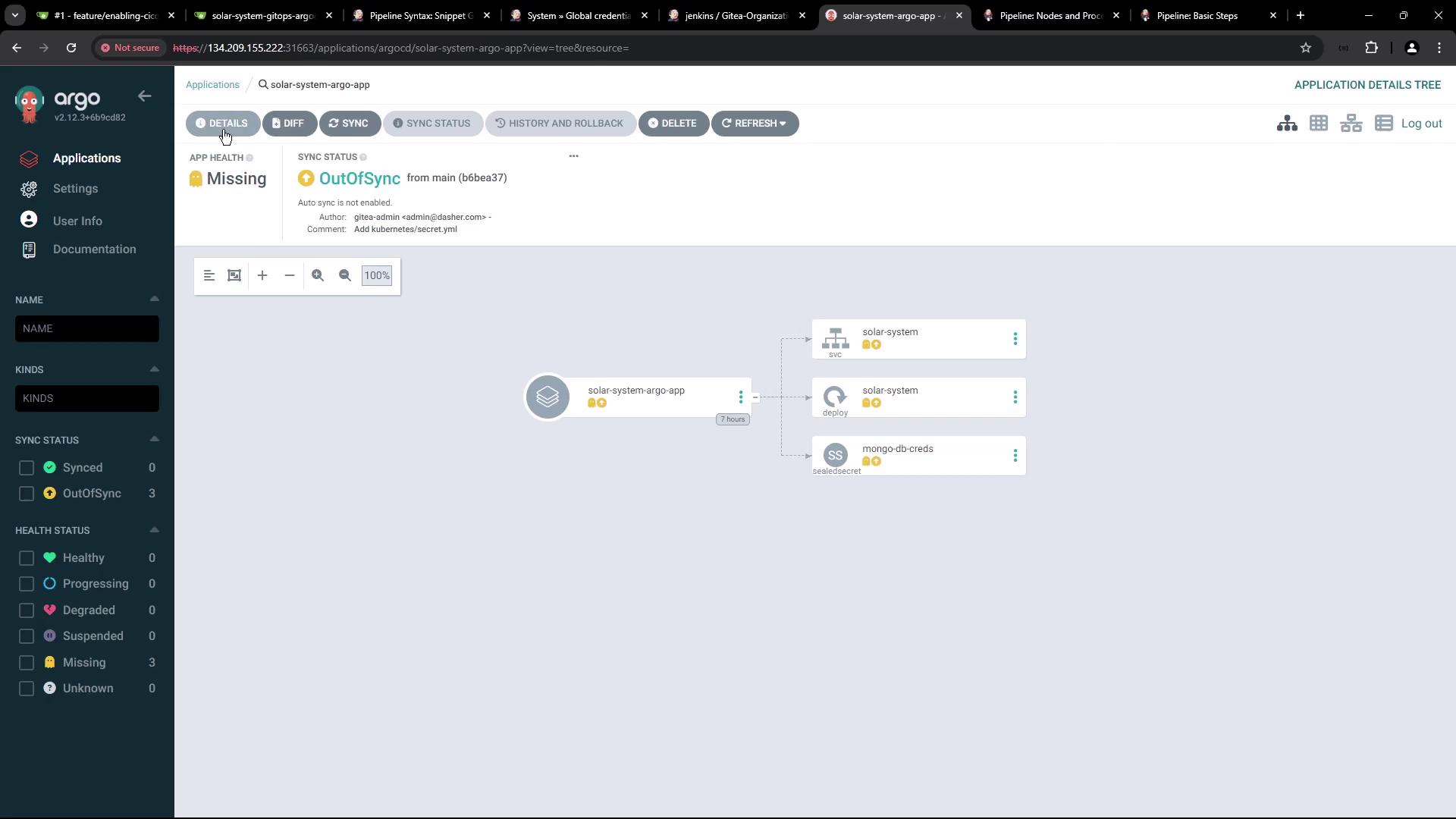
2. Check Argo CD Application Status
Argo CD will show the application as OutOfSync before resources are applied: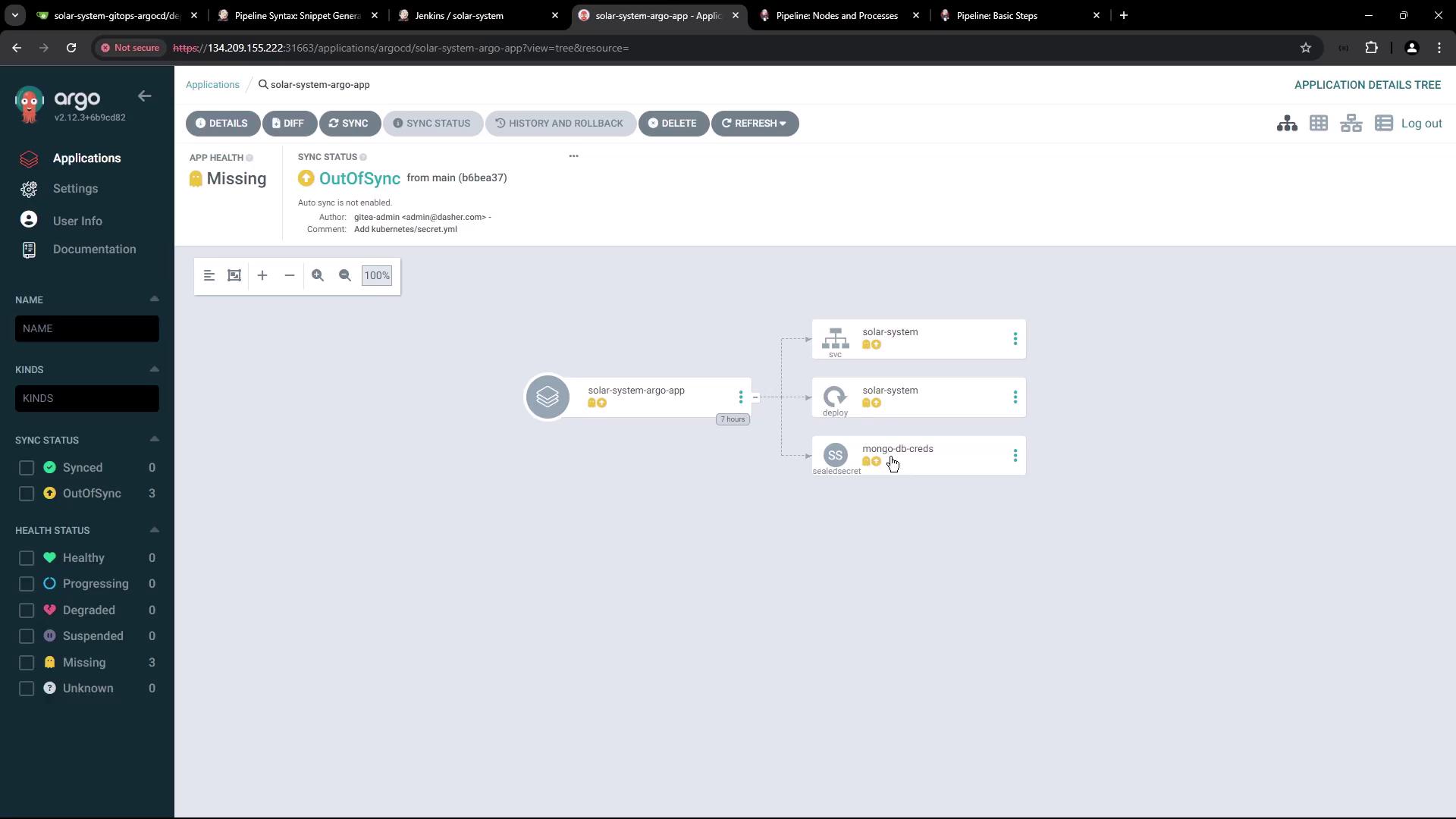
solar-system namespace:
3. Jenkins Pipeline: Add “K8S Update Image Tag” Stage
Add a new declarative stage to yourJenkinsfile to:
- Run only on pull request branches (
PR*). - Clone the GitOps repo.
- Update the Docker image tag in
deployment.yml. - Commit & push to
feature-$BUILD_ID.
Ensure the Jenkins agent has
git and sed installed for cloning and file editing.
4. Configure Gitea API Token
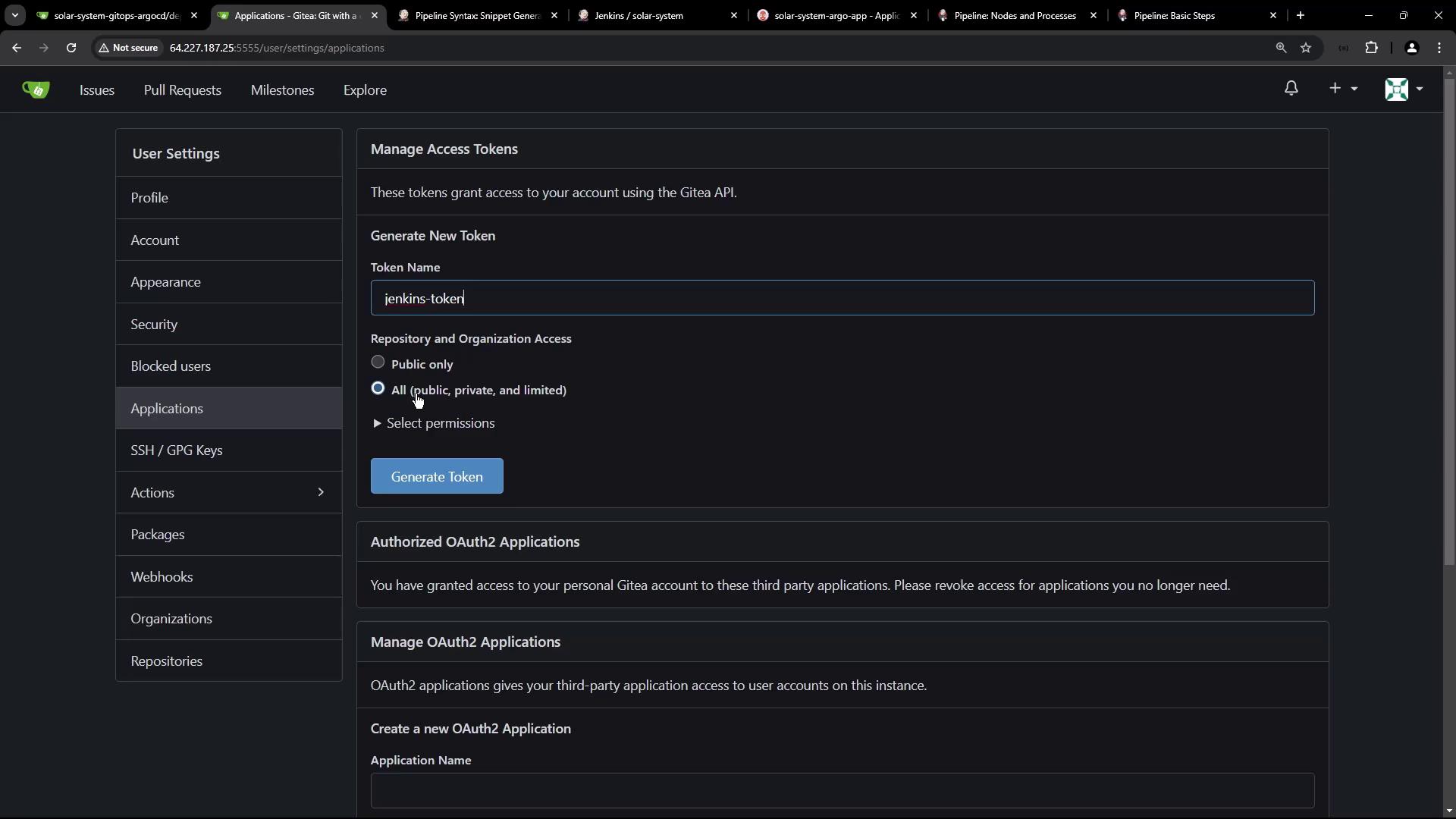
4.1 Generate Token in Gitea
In Gitea user settings, create a new access token namedjenkins-token with read/write scope:
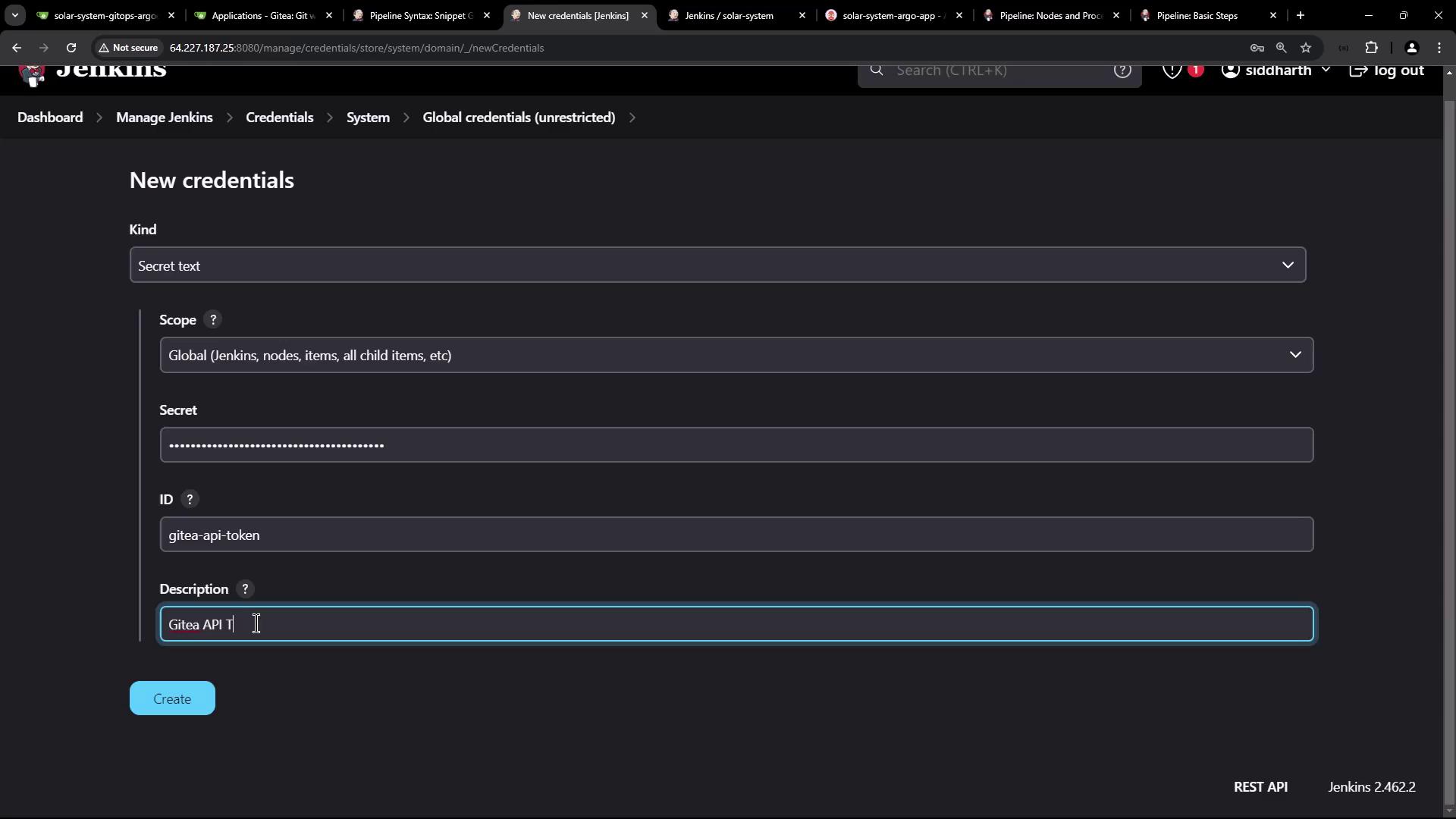
4.2 Add Token to Jenkins Credentials
Go to Credentials > System > Global credentials in Jenkins and add a Secret text credential with IDgitea-api-token:

Keep your API tokens secure. Do not hardcode secrets in your
Jenkinsfile.5. Webhook Trigger on Pull Requests
Configure a Gitea webhook to trigger Jenkins on pull request events: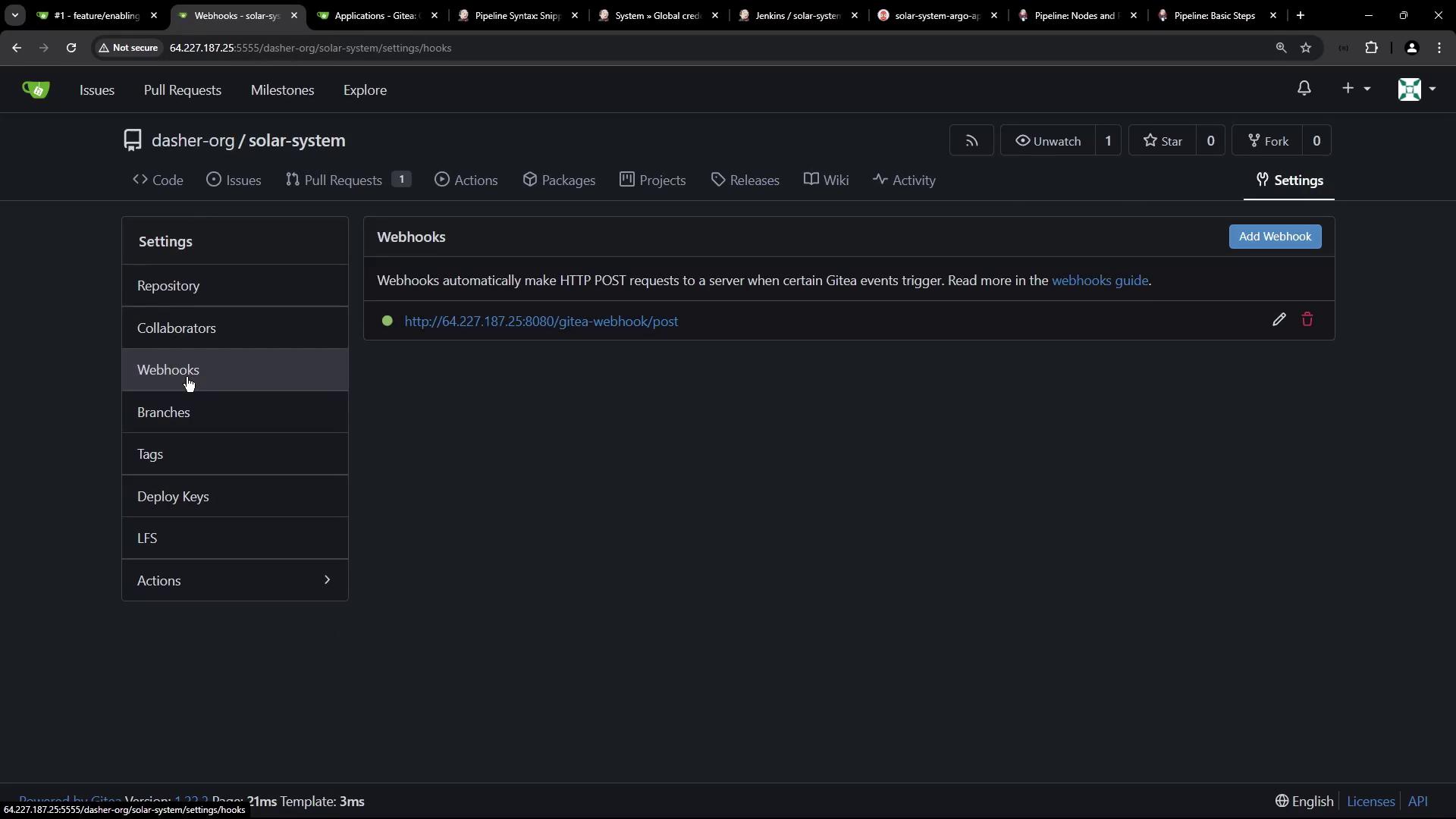
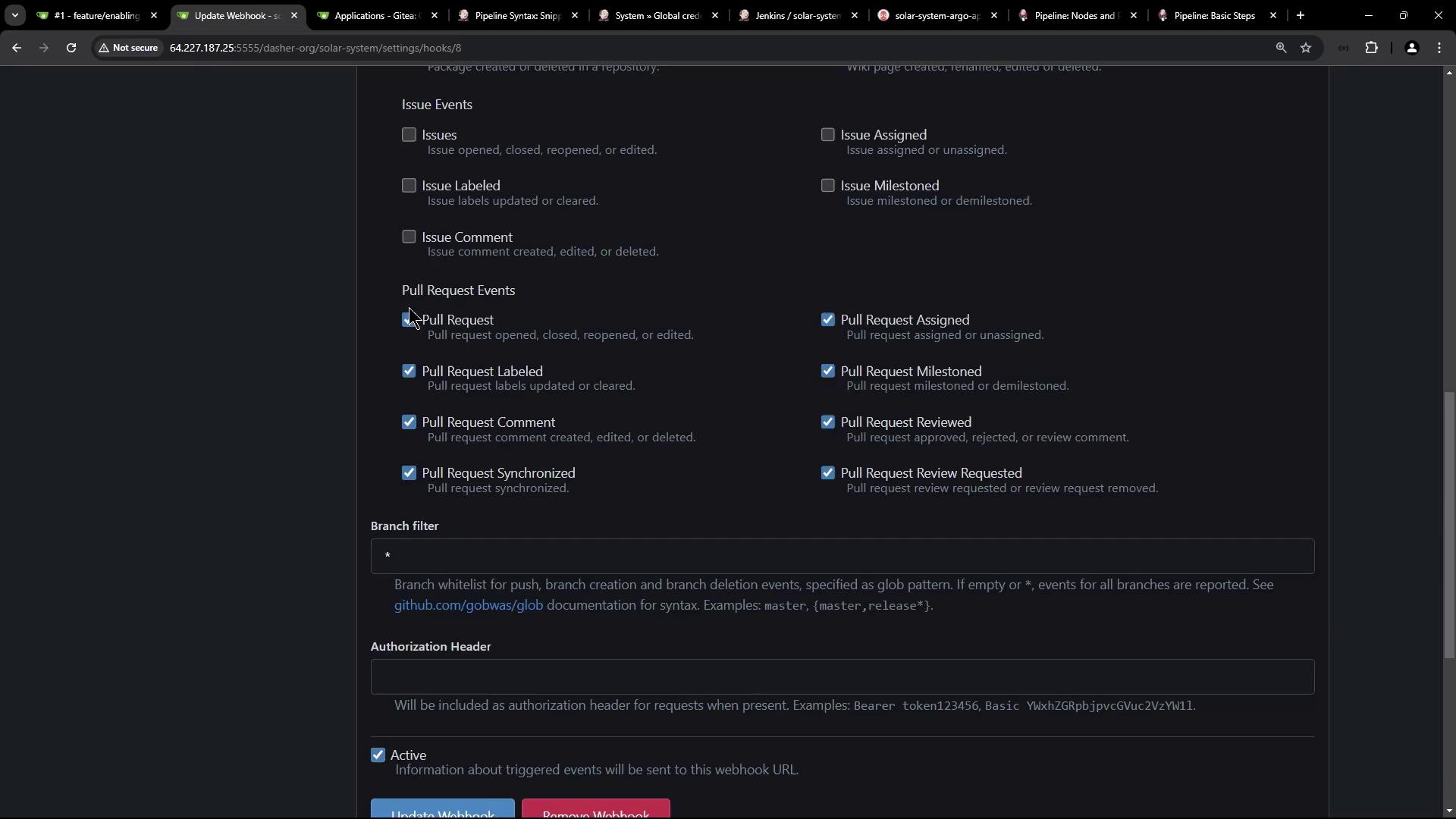
5.1 Create a Pull Request
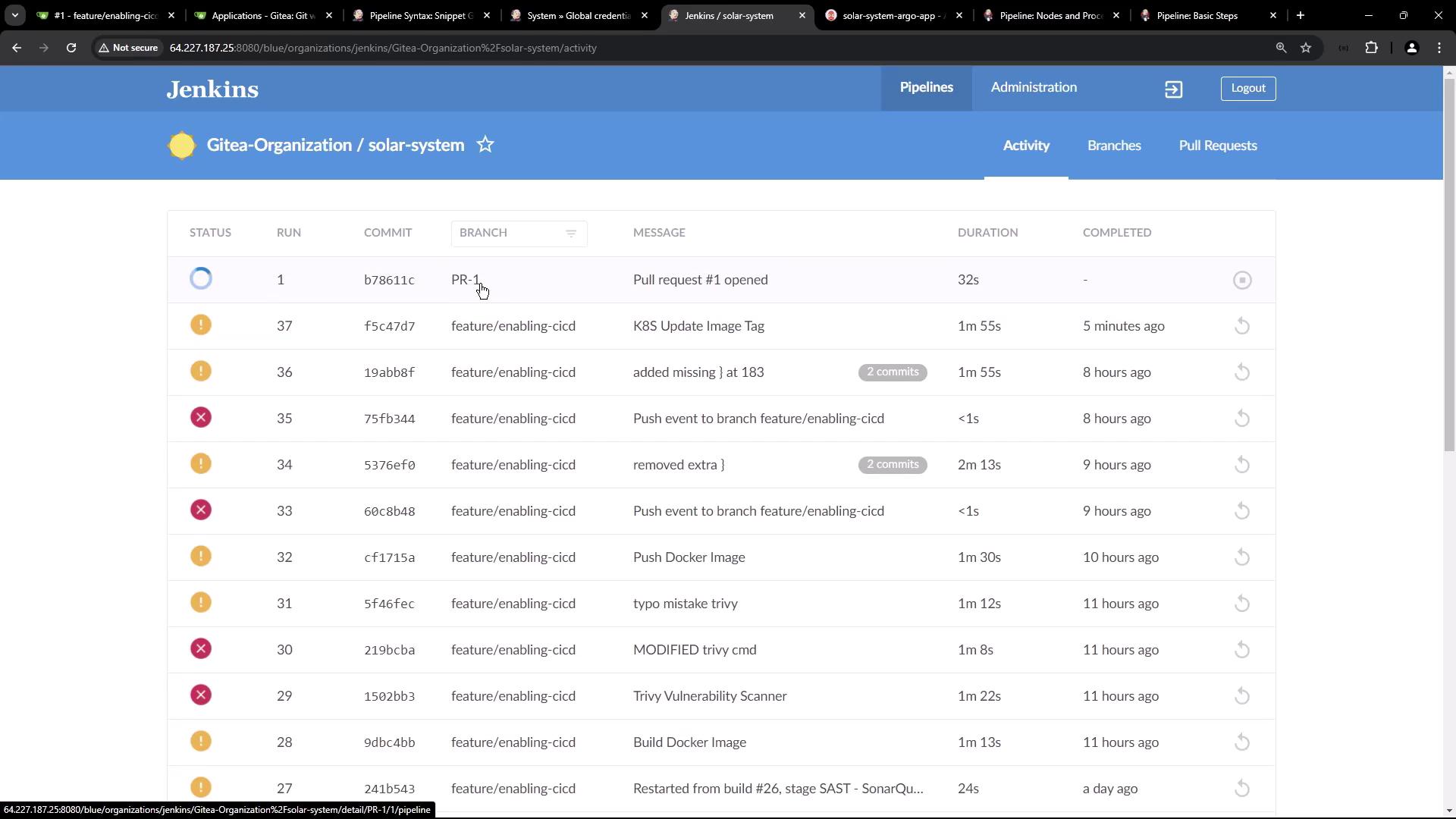
Open a new PR againstmain:

5.2 Observe Jenkins Pipeline Runs
Jenkins will build the PR branch and run the image update: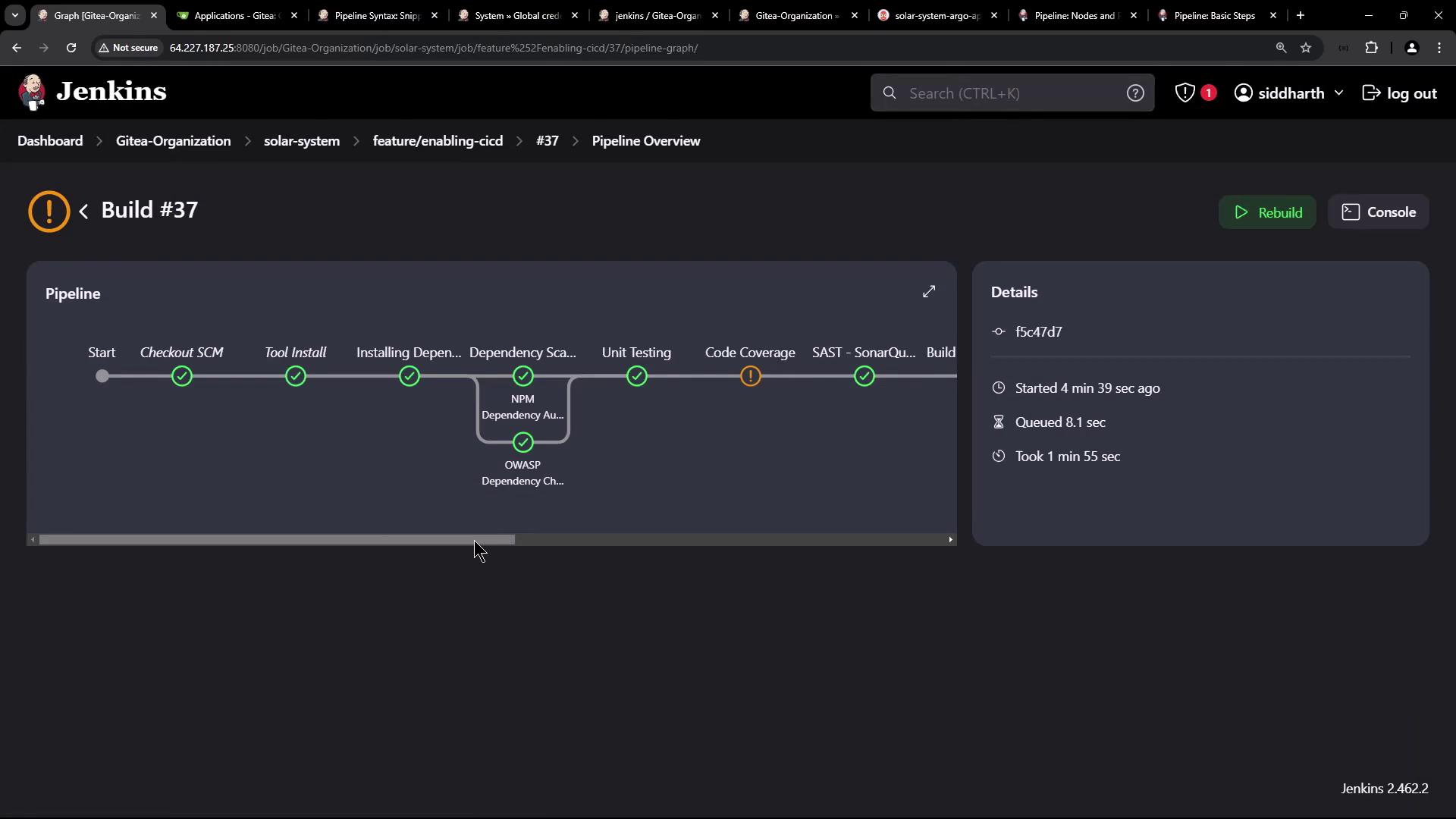
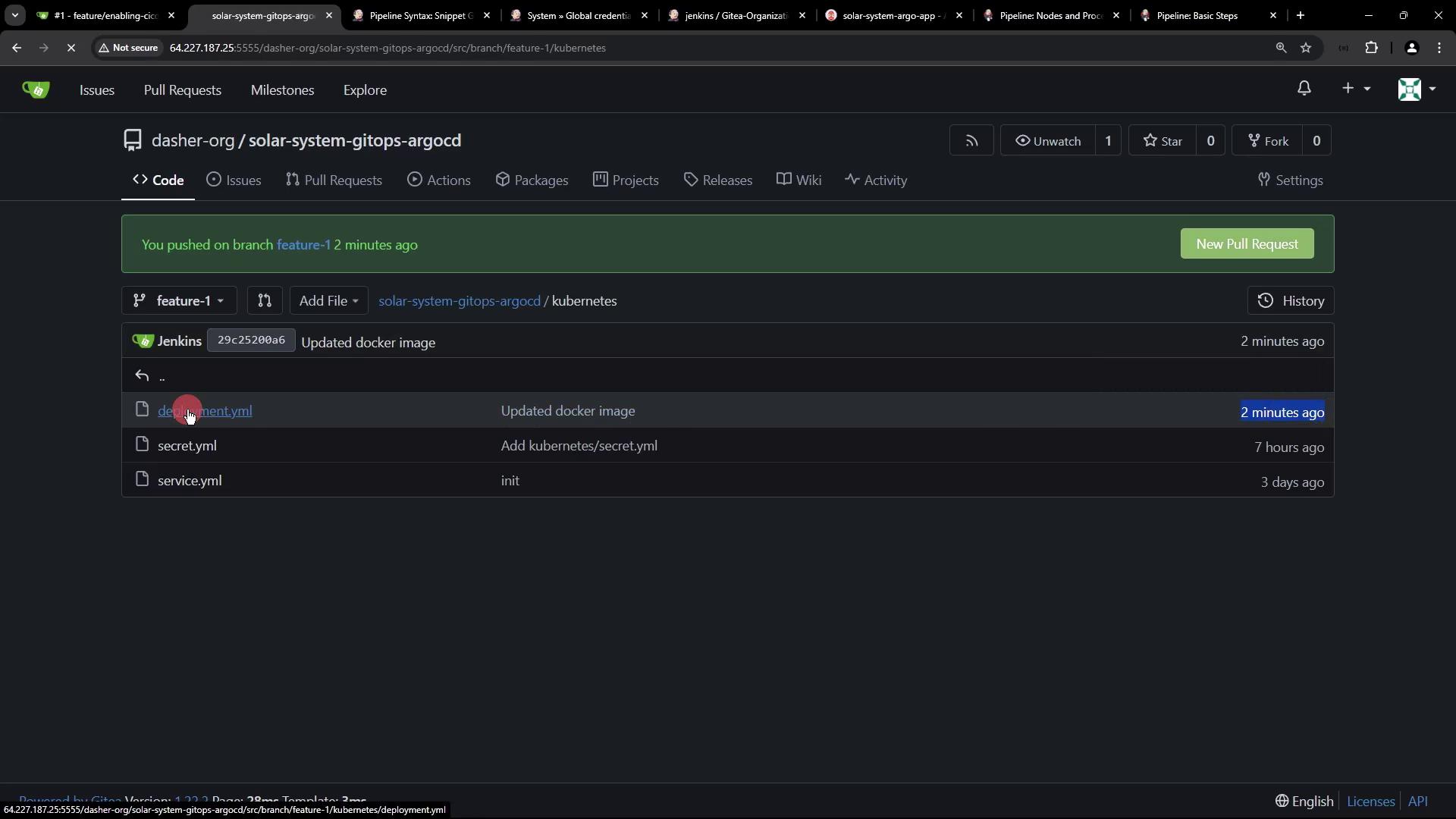
6. Confirm Image Tag Update
Check console logs:feature-1 branch in Gitea:
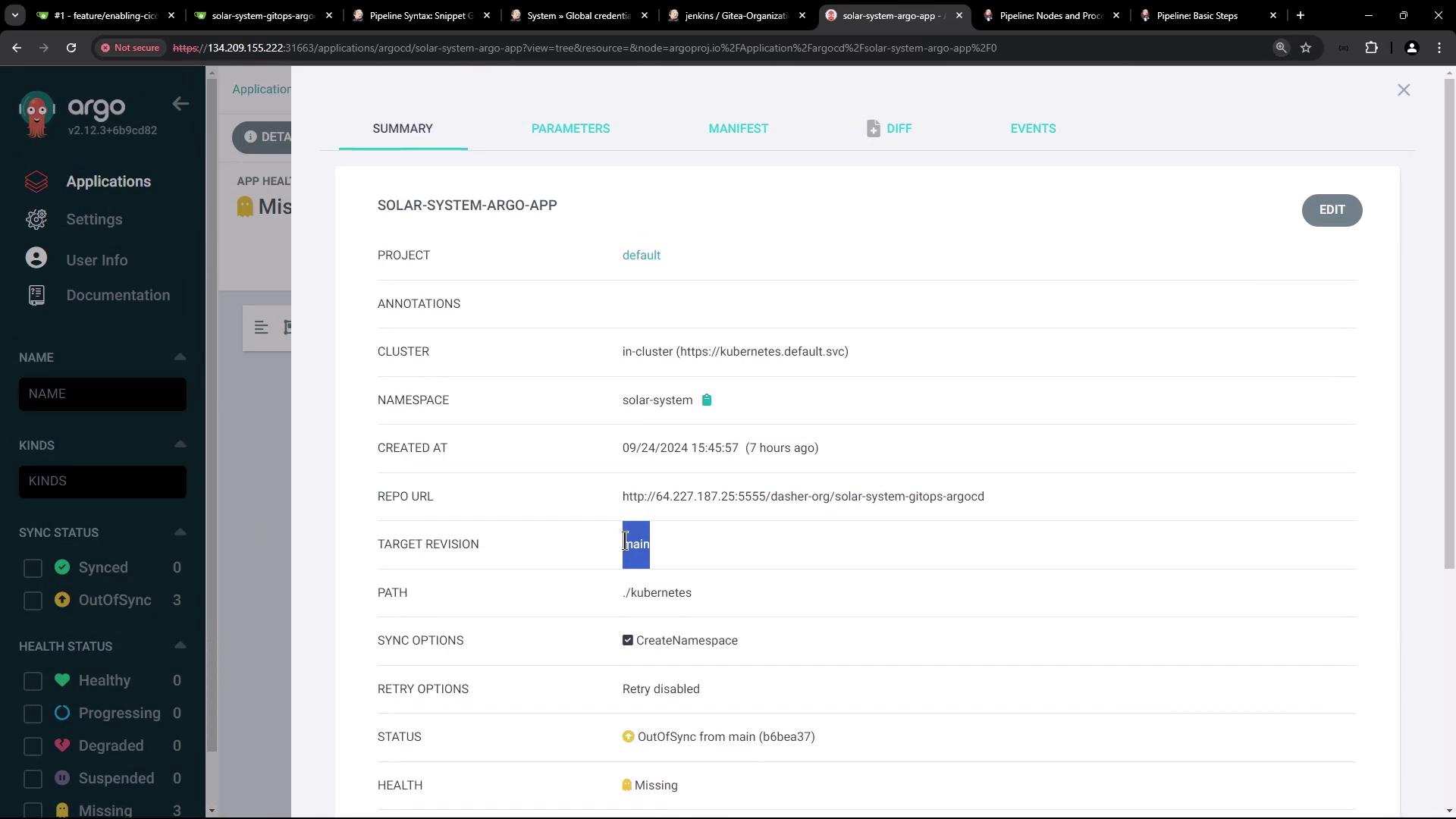
7. Sync with Argo CD
Since Argo CD tracksmain, it remains OutOfSync until you merge feature-1:
feature-1 into main so Argo CD can deploy the updated manifest.