The Power of Access Control
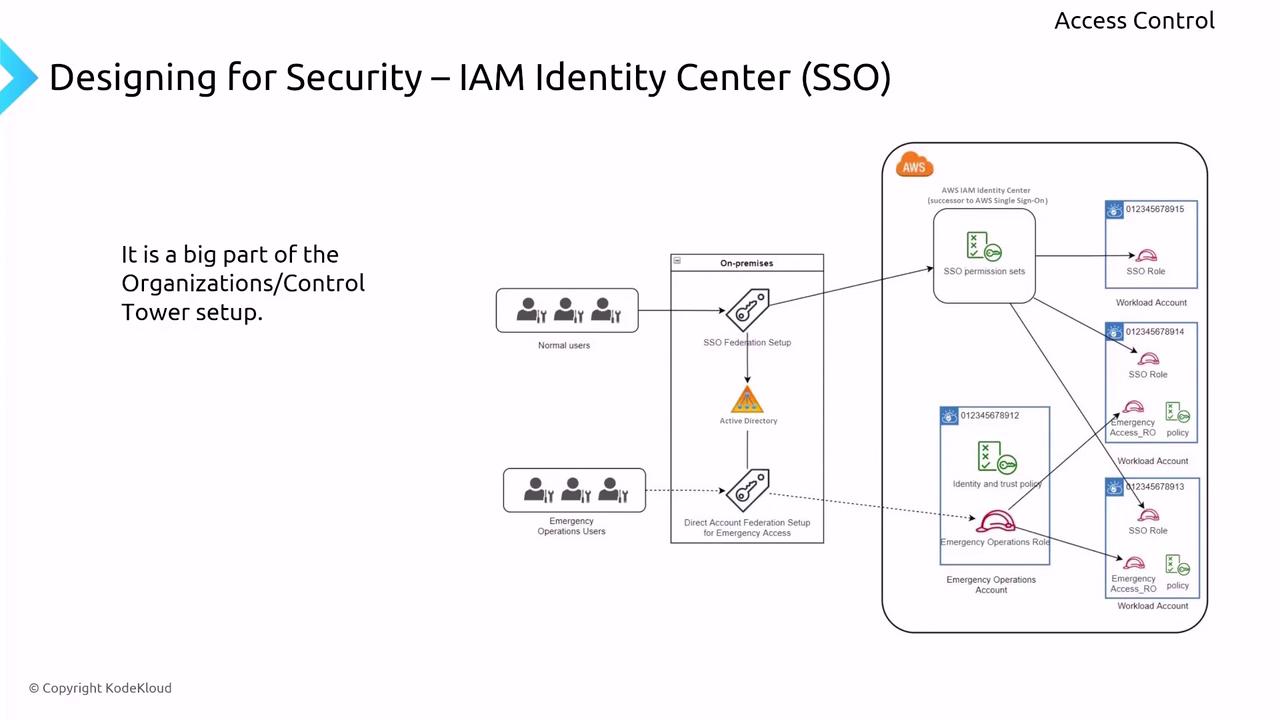
Access control is a cornerstone of cloud security. In AWS, Identity and Access Management (IAM) is your first line of defense. While IAM provides secure defaults and industry standard practices, there are additional measures that can further harden your environment.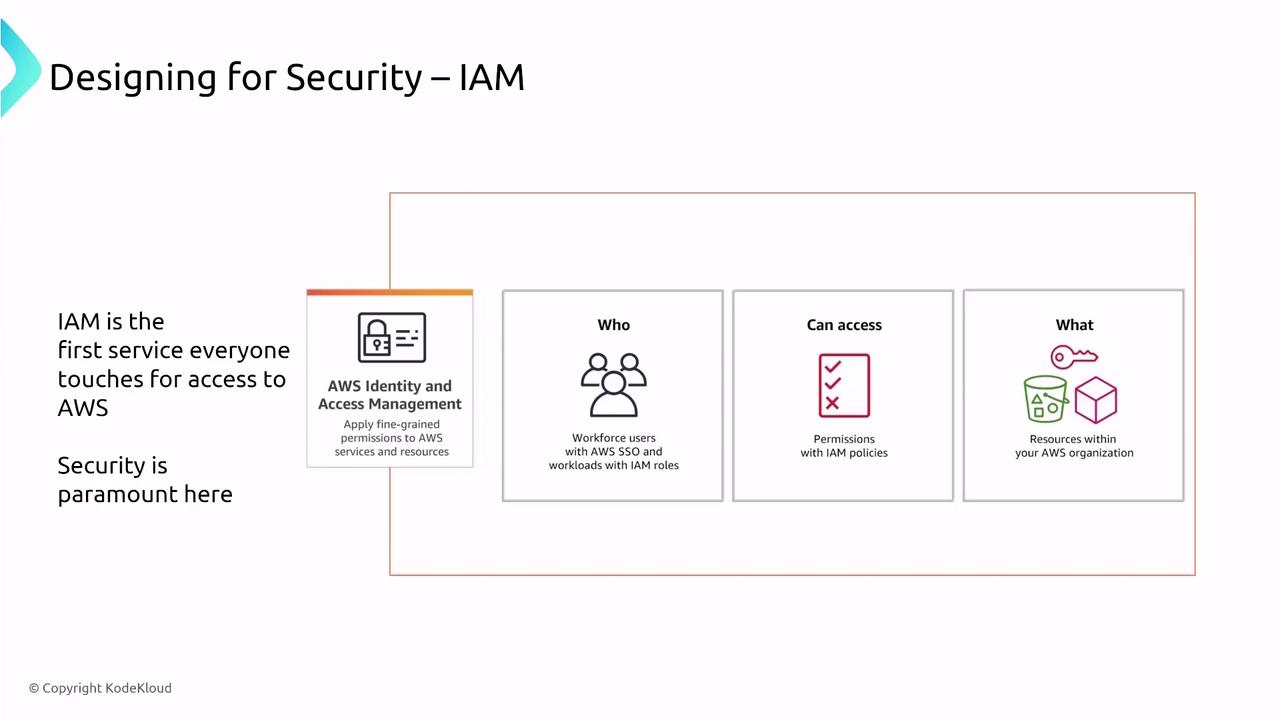
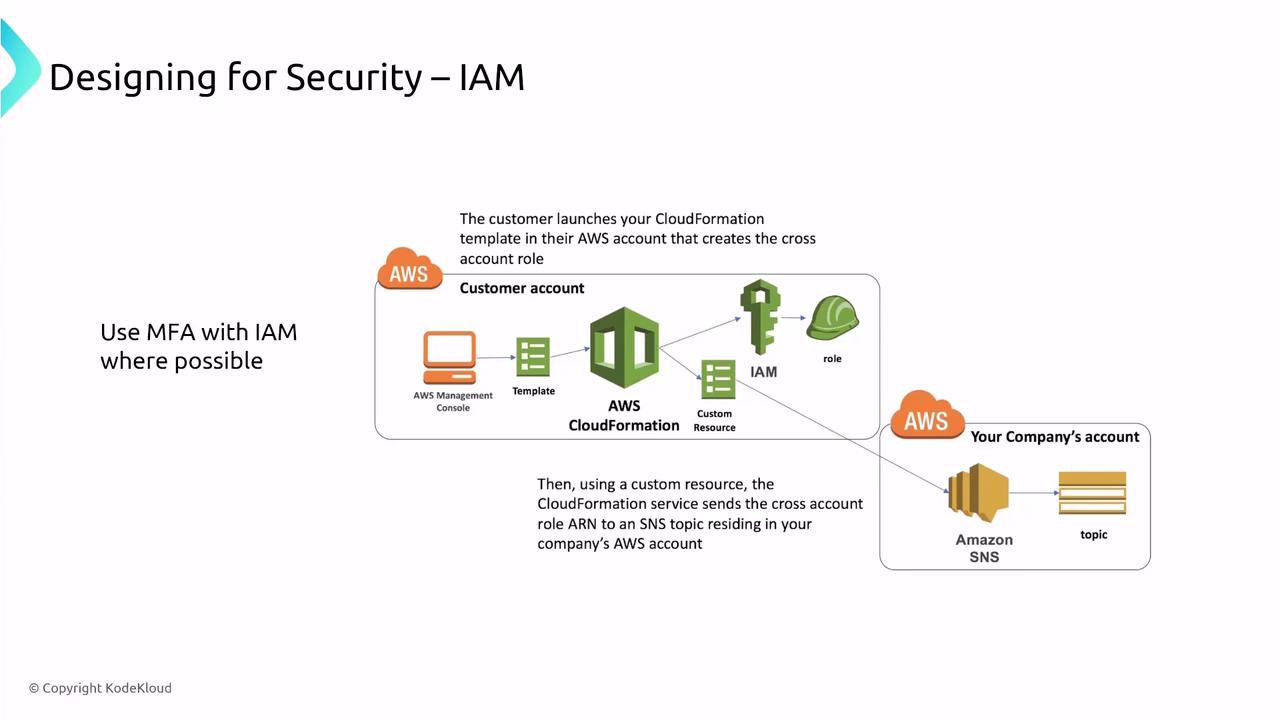
- Enable multi-factor authentication (MFA) to add an extra layer of protection.
- Apply the principle of least privilege by assigning roles that grant only the essential permissions.
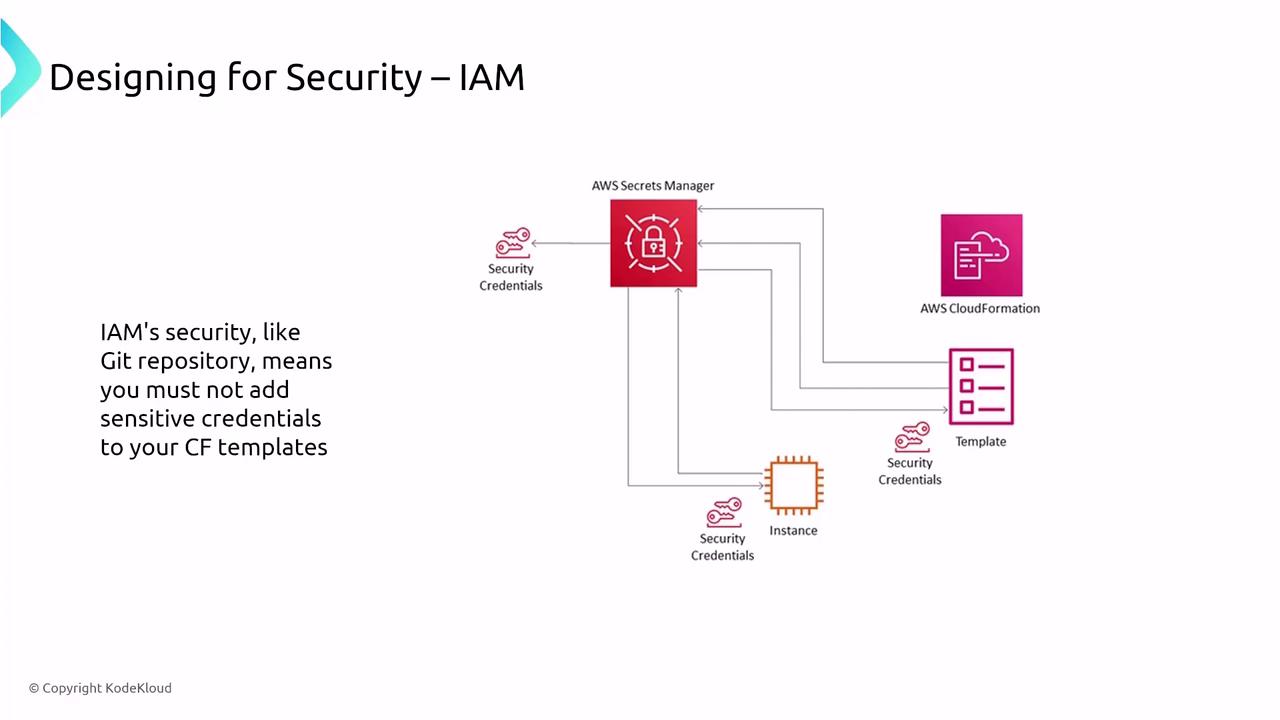
Avoid embedding sensitive credentials like secret keys directly in CloudFormation templates or in Git repositories. Use AWS Secrets Manager or AWS Systems Manager Parameter Store to securely manage and store sensitive data.
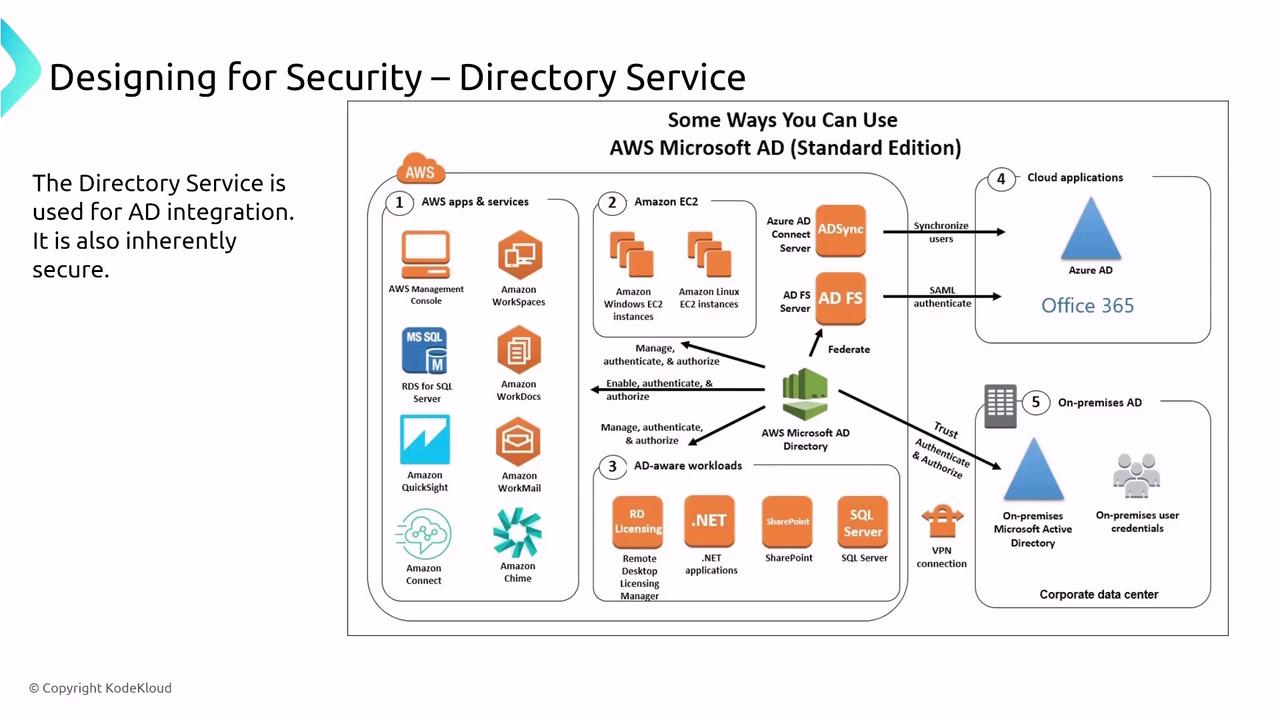
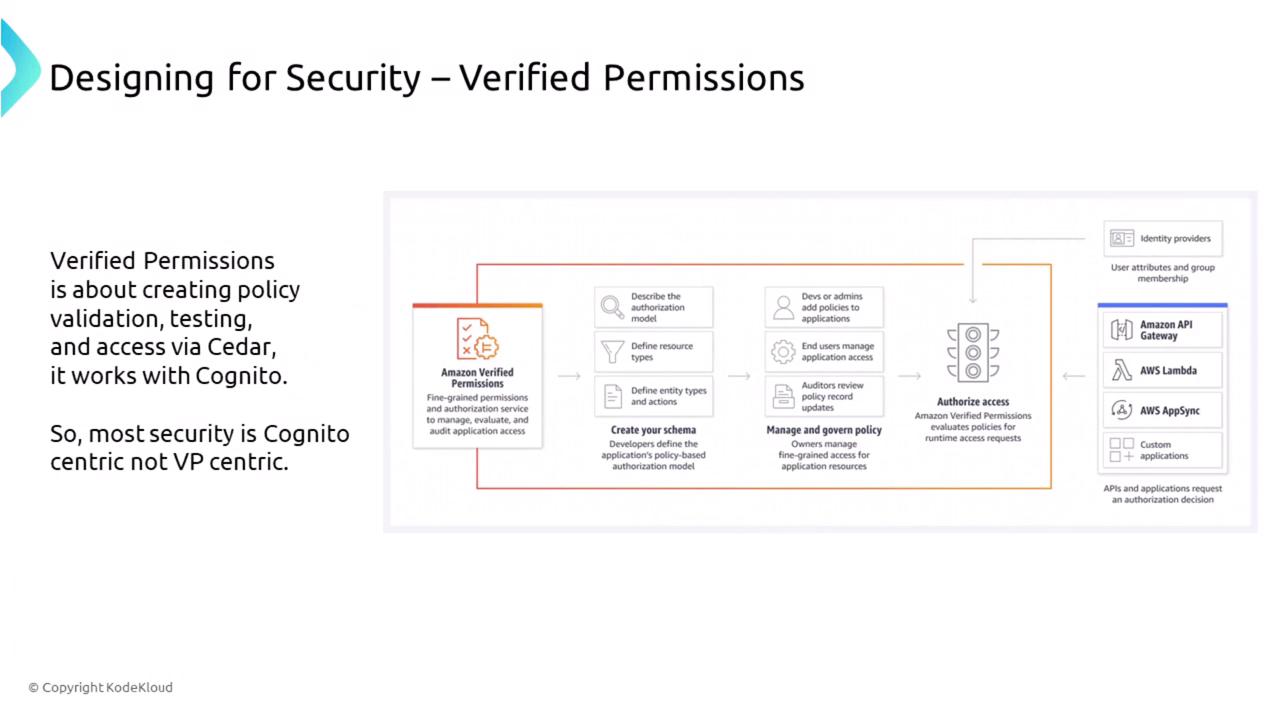
Auditing Services
Auditing is essential for tracking changes and monitoring configurations across your AWS environment. Key services include CloudTrail, CloudWatch, and AWS Config.AWS CloudTrail
CloudTrail logs API call activities and is capable of exporting these logs to Amazon S3—a process that should always be paired with encryption via AWS Key Management Service (KMS). Additionally, CloudTrail Lake and Security Lake enhance log analysis and query capabilities.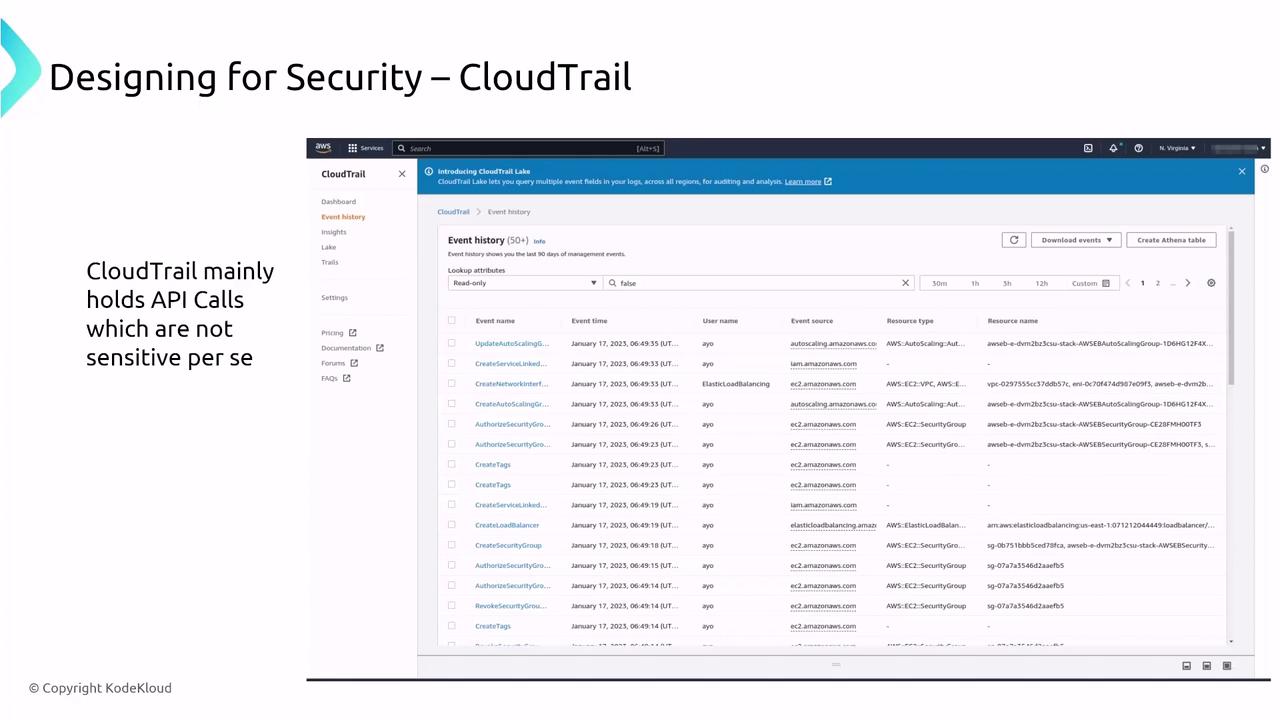
AWS Config
AWS Config continuously captures changes within your environment and encrypts data both at rest and in transit by default. Although the control options are limited, you can customize rules and notifications to ensure continual compliance with your security policies.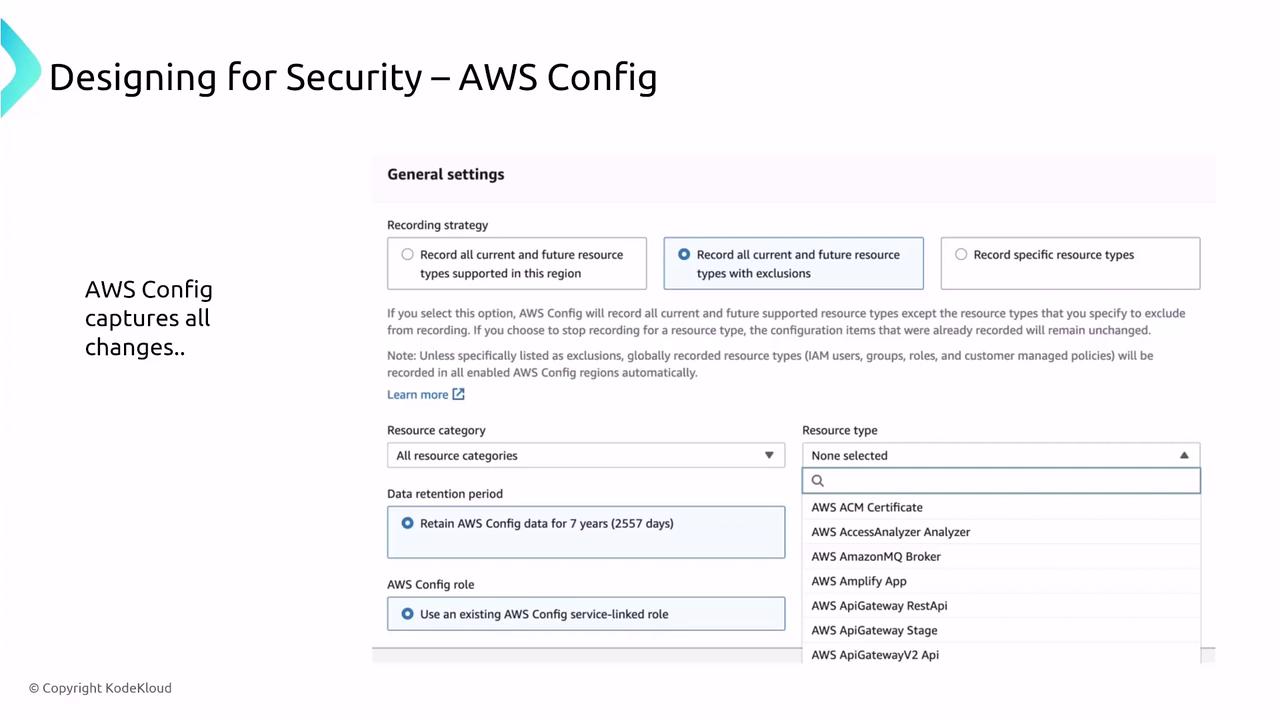
AWS Artifact
AWS Artifact provides on-demand access to AWS compliance reports and certification documents, including ISO 27001 and PCI DSS reports. While Artifact does not directly influence security controls, it is vital for auditing and maintaining compliance standards.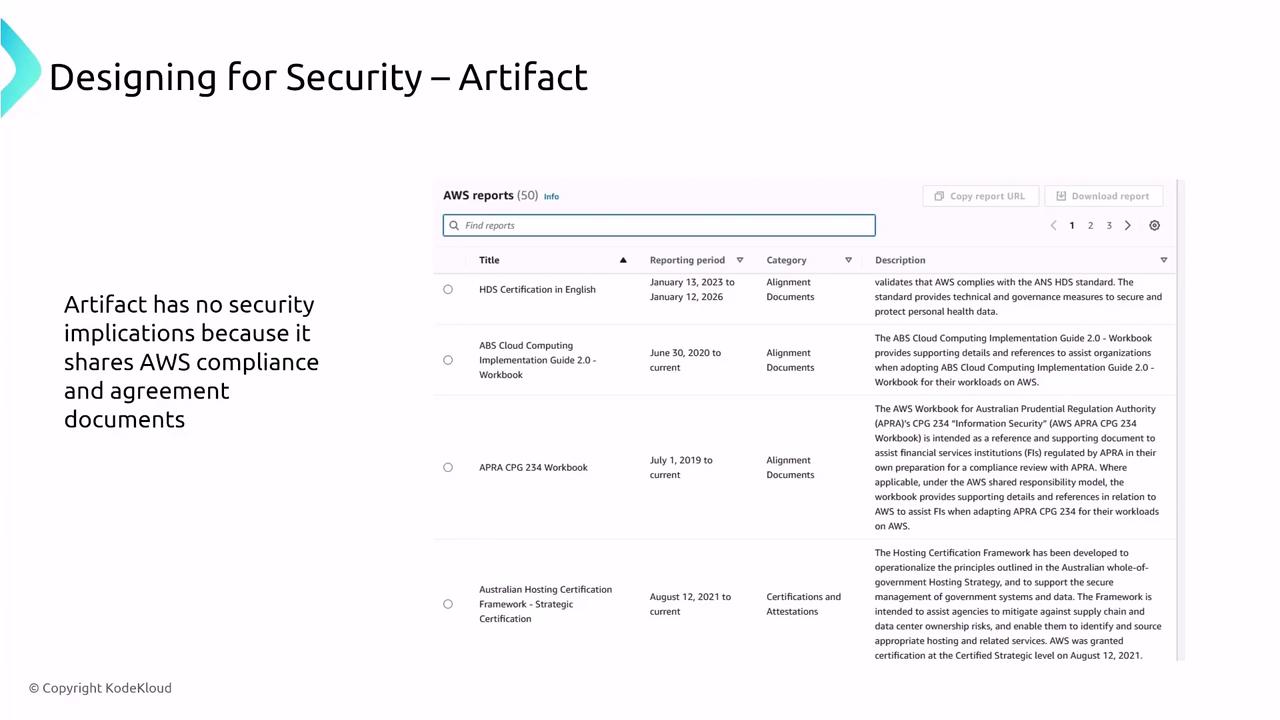
The Power of Detection
Detection tools help identify threats and vulnerabilities before they can be exploited. AWS offers several detection-focused services that provide continuous monitoring and insightful analytics.AWS GuardDuty
GuardDuty employs machine learning and threat intelligence to analyze DNS logs, VPC flow logs, and CloudTrail events. It detects anomalies and potential threats, automatically forwarding findings to AWS Security Hub for centralized management.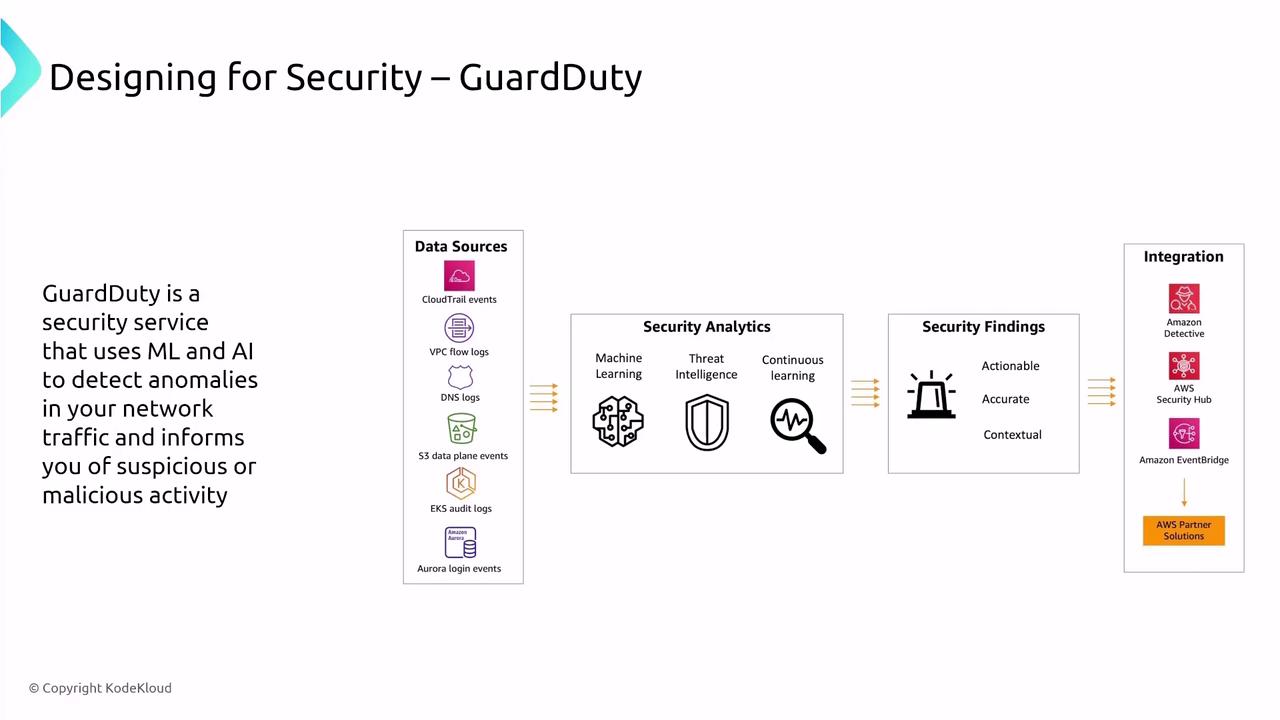
AWS Inspector
AWS Inspector is a vulnerability assessment service that scans EC2 instances, containers, and Lambda functions for known vulnerabilities. It automatically conducts scans and reports findings, making it a valuable service for regular security assessments.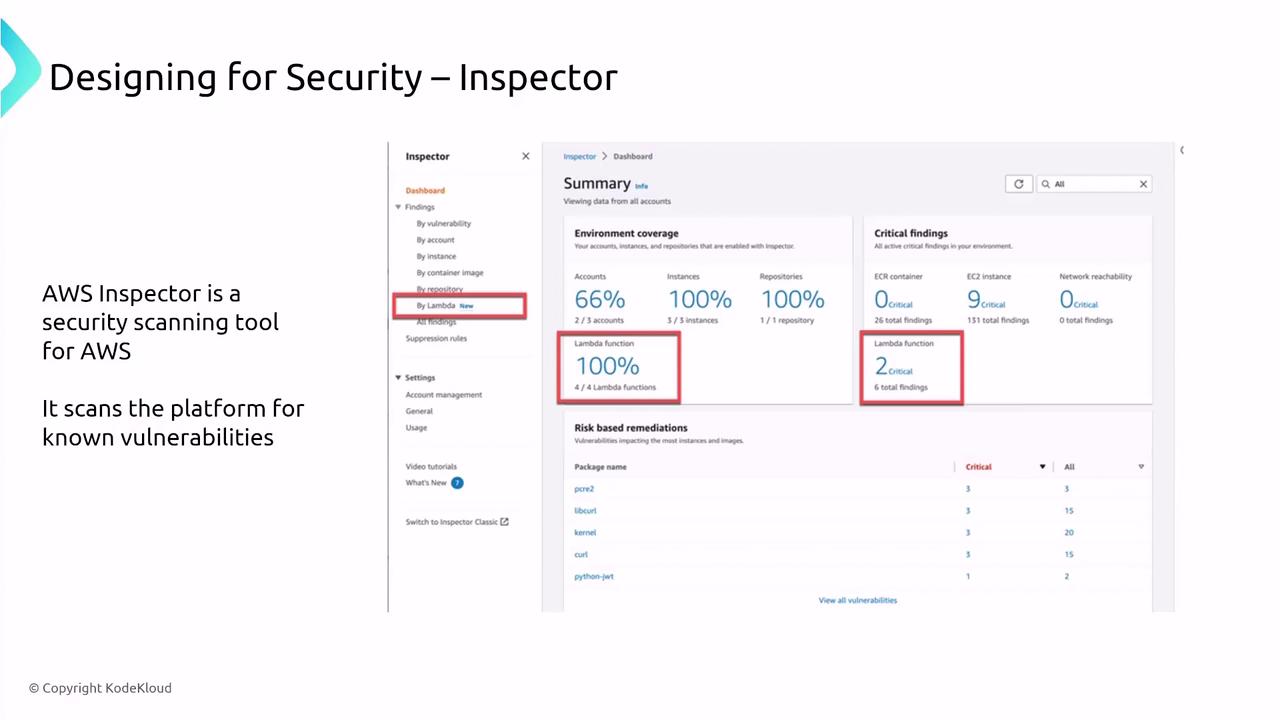
Amazon Macie
Amazon Macie specializes in detecting and classifying sensitive data within S3 buckets, such as personally identifiable information (PII). As Macie continuously monitors S3 buckets, additional security configurations are typically not required.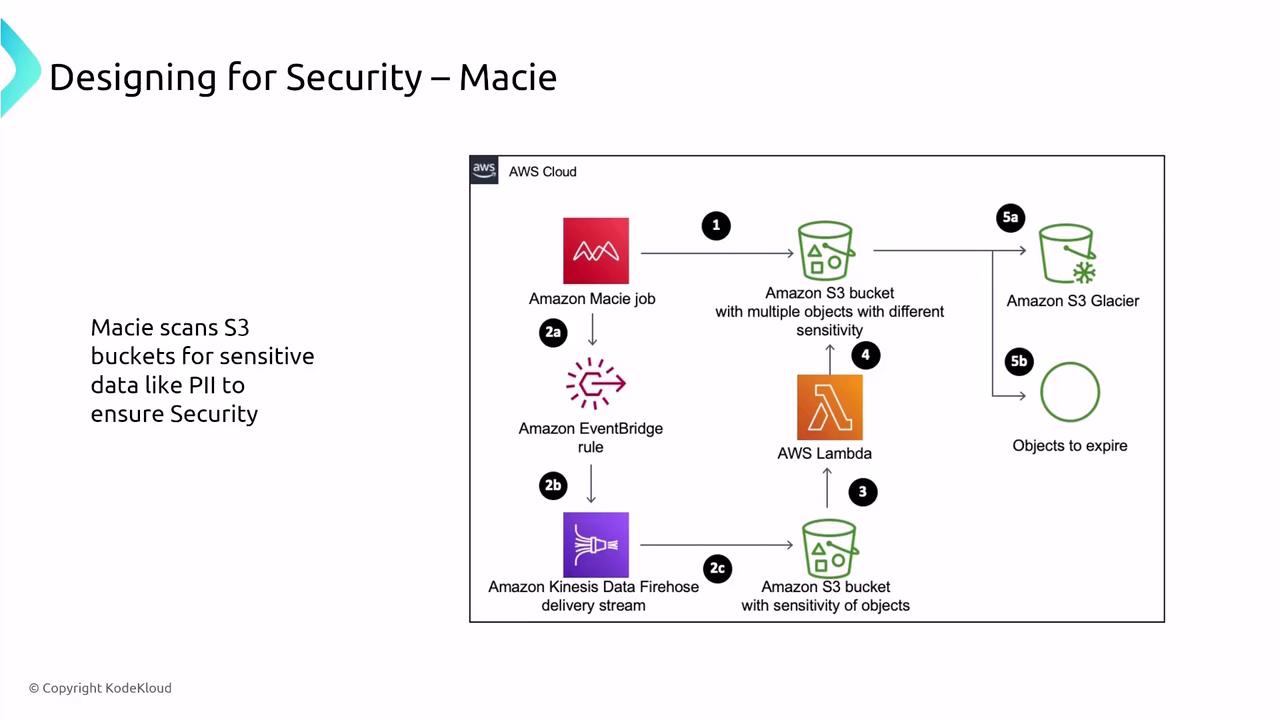
AWS Security Hub
AWS Security Hub centralizes and aggregates security findings from multiple AWS services like GuardDuty, Inspector, and Macie. While the service itself is inherently secure, ensure that IAM access restrictions to the Security Hub dashboard are properly configured.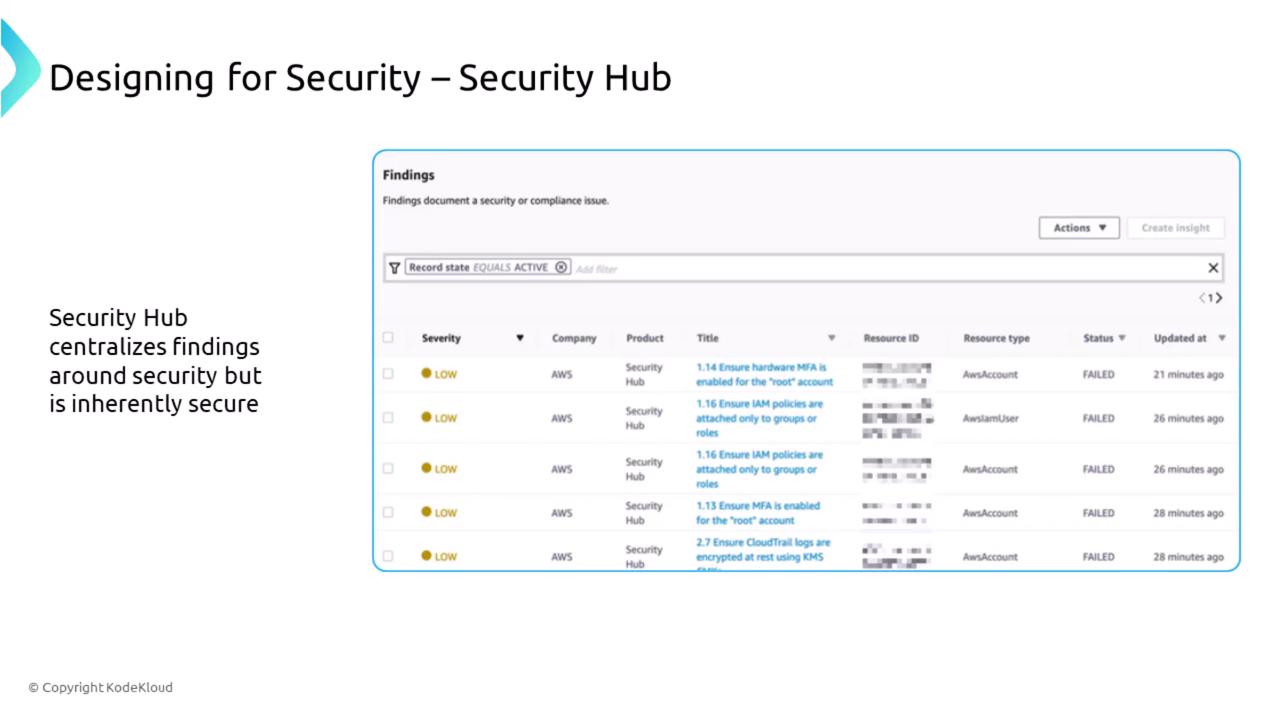
The Power of Encryption
Data encryption is vital in protecting information both at rest and in transit. AWS provides robust encryption solutions to safeguard your data.AWS Key Management Service (KMS) and CloudHSM
AWS Key Management Service (KMS) and CloudHSM are foundational for data encryption in AWS. KMS is a multi-tenant service that integrates seamlessly with many AWS services, while CloudHSM offers a dedicated single-tenant hardware security module for organizations with stringent security requirements. Both solutions support key rotation and fine-tuned access control via IAM policies.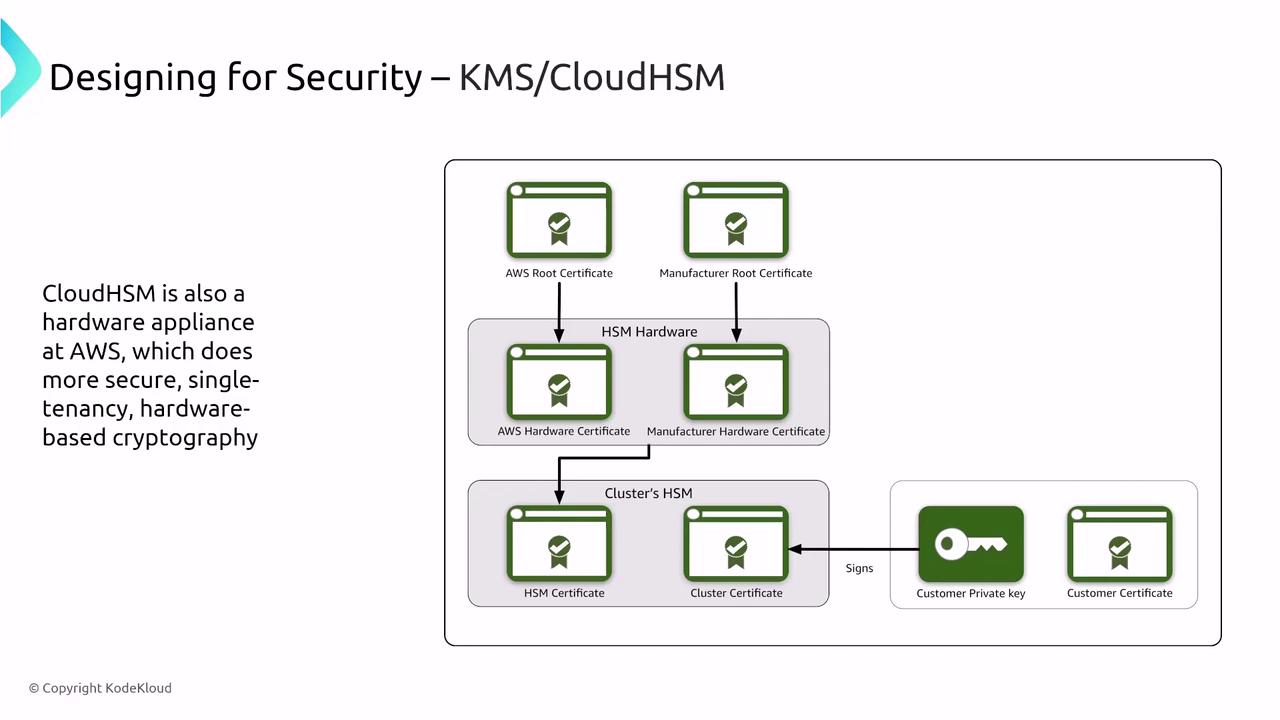
This lesson provided an in-depth overview of enhancing security across various AWS services—from strengthening access control using IAM and Cognito, auditing environment changes with CloudTrail and AWS Config, detecting potential threats with GuardDuty and Inspector, to securing data via KMS and CloudHSM. Each service offers a range of built-in security features along with advanced options to further harden your AWS environment. Keep these principles in mind as you design and implement secure architectures in AWS. Happy architecting!