Introduction to Security Design Conversations
Security design discussions often begin when a stakeholder makes a specific request. For example:- “Can we secure the data stored in AWS?”
- “Please ensure that Java on our systems is patched to a specific version.”
Matching Security Features to AWS Services
Let’s delve into some AWS examples to illustrate how security features align with services:Data Protection
For S3, enabling encryption is a key data protection measure. Additionally, versioning is another feature that safeguards data integrity.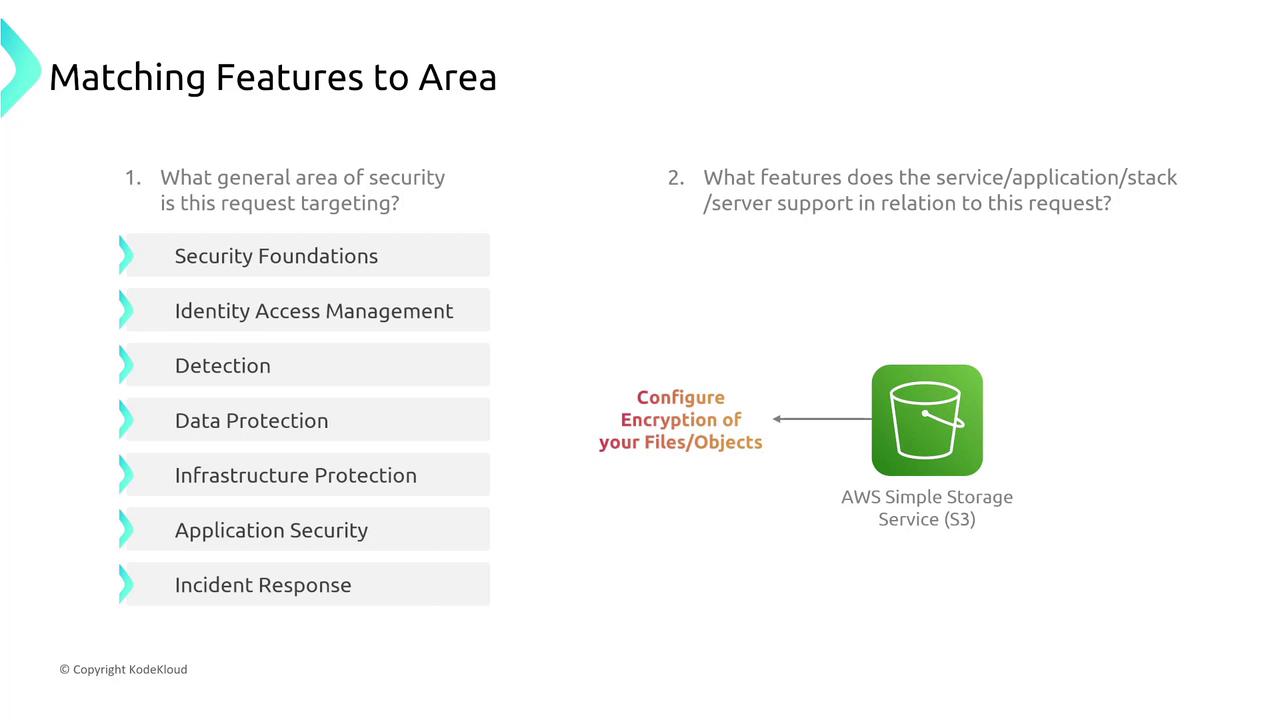
Detection
Activating detailed logging on an S3 bucket can be viewed as a detection mechanism—helping you monitor object access. Likewise, VPC flow logs serve as an event detection tool rather than solely preventing unauthorized access.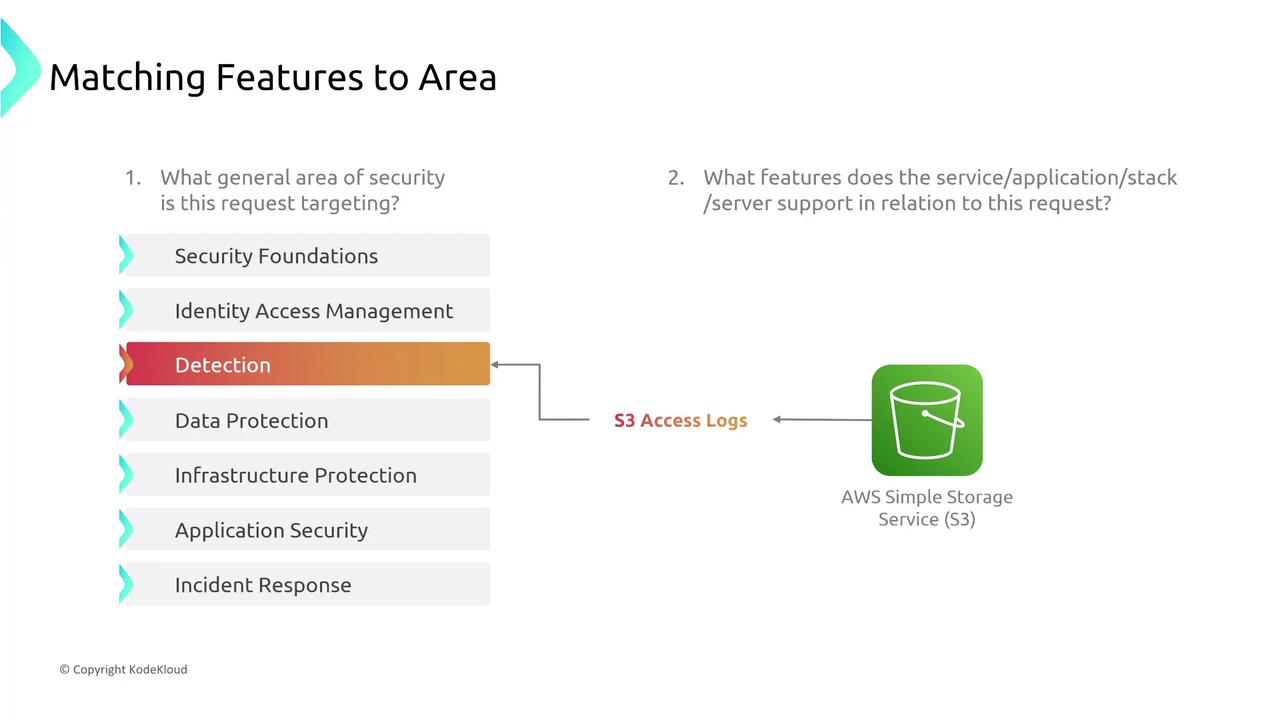
Identity and Access Management (IAM)
Adjustments to access control lists (ACLs) and enhanced logging for detailed access insights tie into IAM and broader application security. When preparing for the AWS certification exam, analyze the security request by identifying the target category: application layer, network infrastructure, or data security. The solution should maximize security while minimizing cost and operational overhead.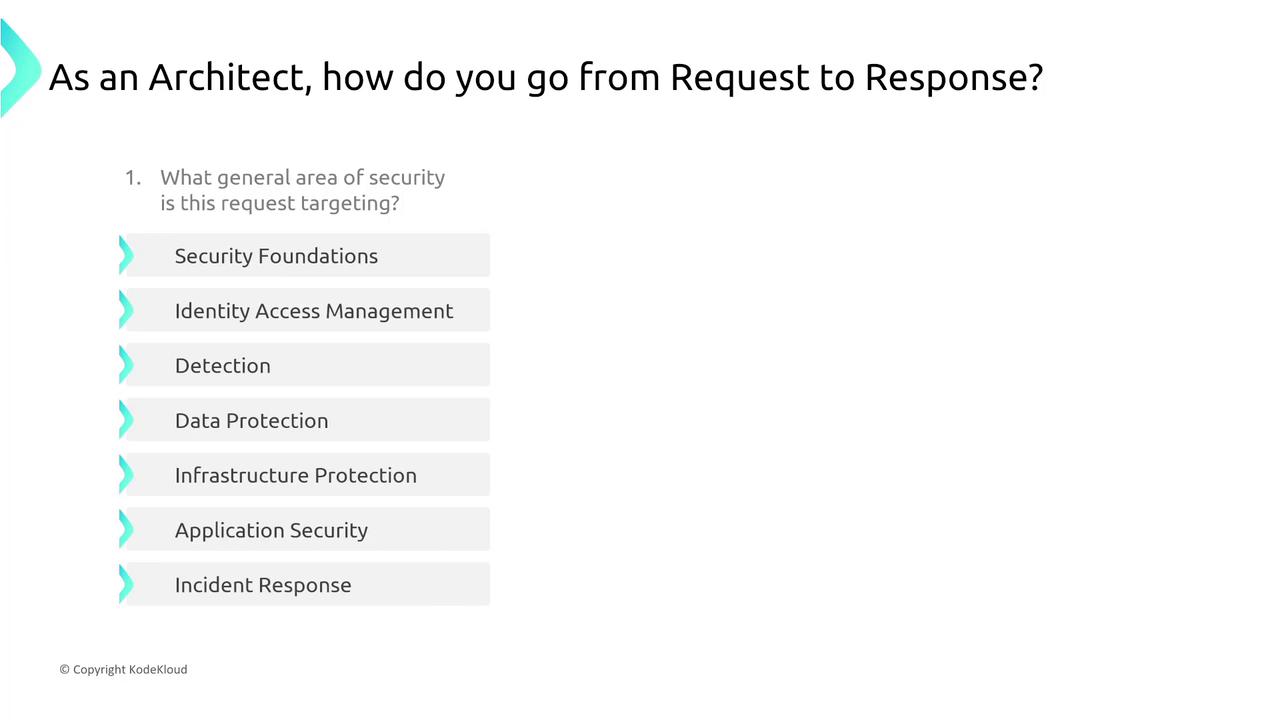
- Designing secure access to AWS resources.
- Designing secure workload and application environments.
- Determining appropriate data security controls.
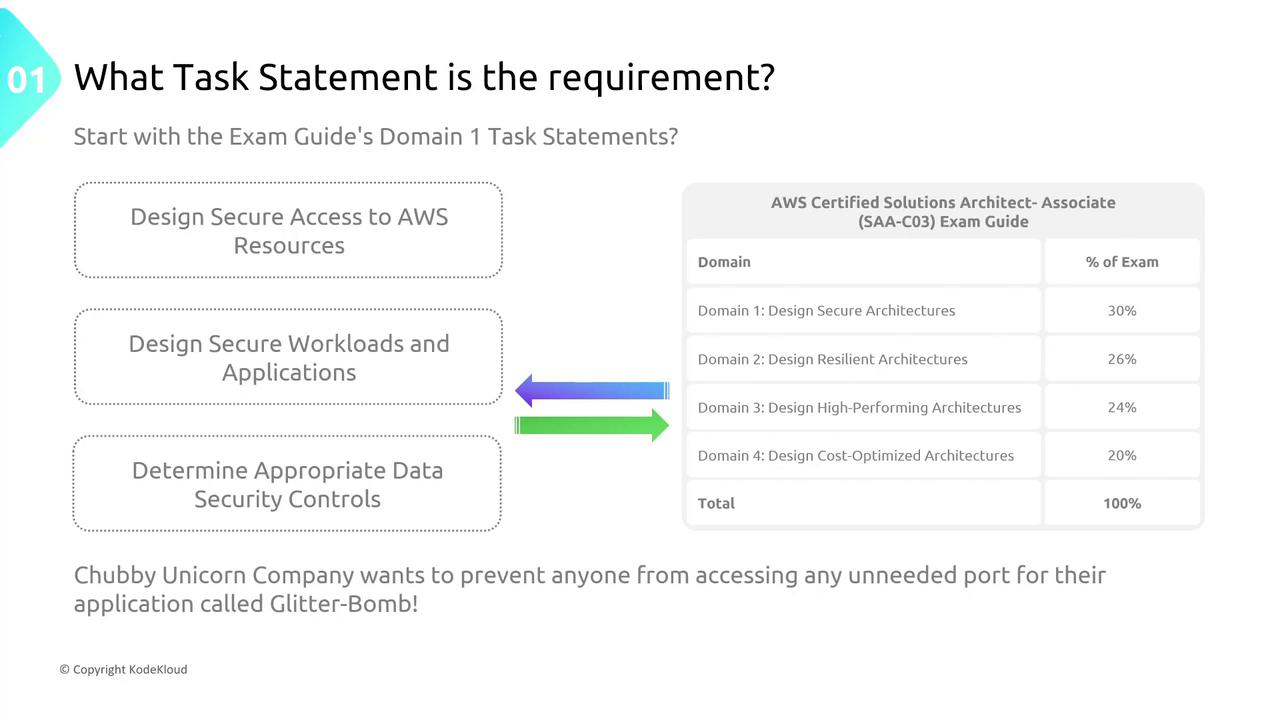
Deconstructing Complex Networking Diagrams
Understanding how to deconstruct intricate network security diagrams is an essential skill. Consider the following narrative inspired by Chubby Unicorn Company:1. Multiple Campuses in a Region
Imagine an AWS account as a collection of campuses (regions). Think of AWS regions and accounts as numerous office locations, each segmented by groups—like different floors in a building representing public and private subnets.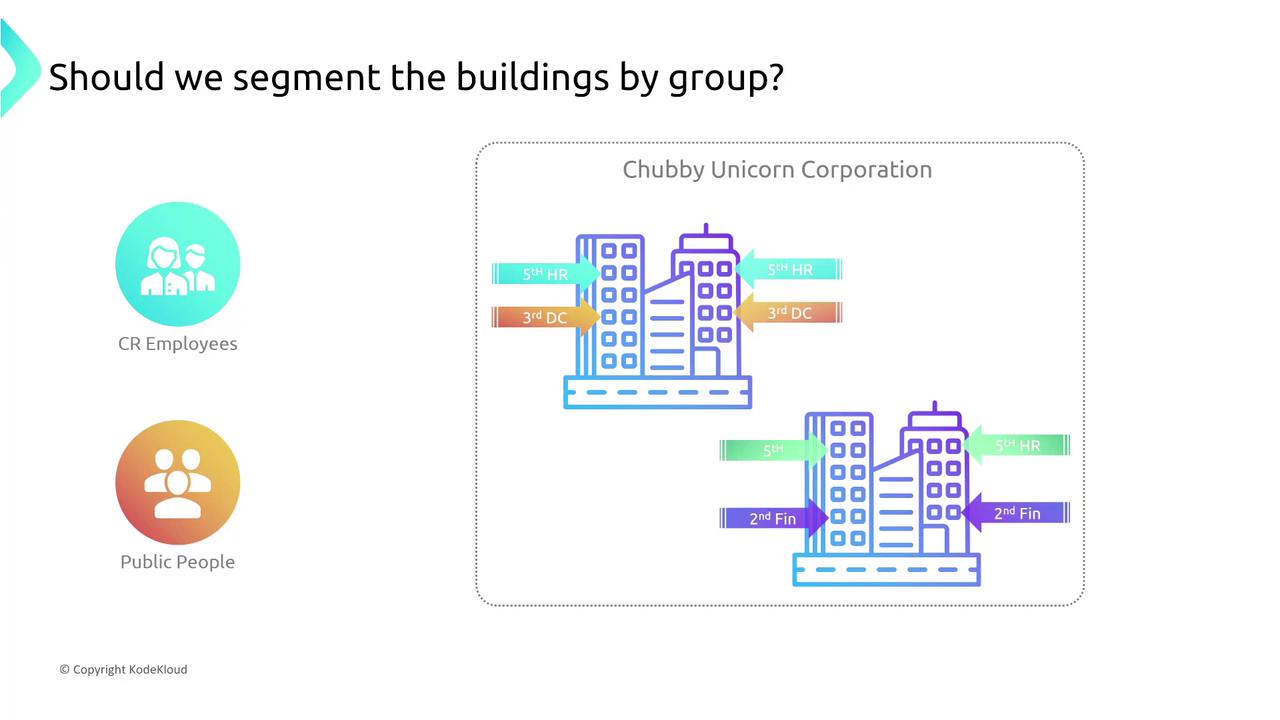
2. Segmentation Within a Building
Within a VPC:- The first floor (public subnet) is accessible via an Internet Gateway.
- Upper floors (private subnets) host sensitive operations.
- Public subnets managed by route tables and protected by Network ACLs (NACLs).
- Private subnets that rely on NAT Gateways for outbound communications.
- Instance-level firewalls enforced by security groups.
3. Routing and Address Resolution
An Internet Gateway allows external traffic to reach public subnets. Route tables then “direct traffic” much like a receptionist, ensuring that data reaches the appropriate destination. Private subnets typically route via NAT Gateways to maintain secure outbound connections.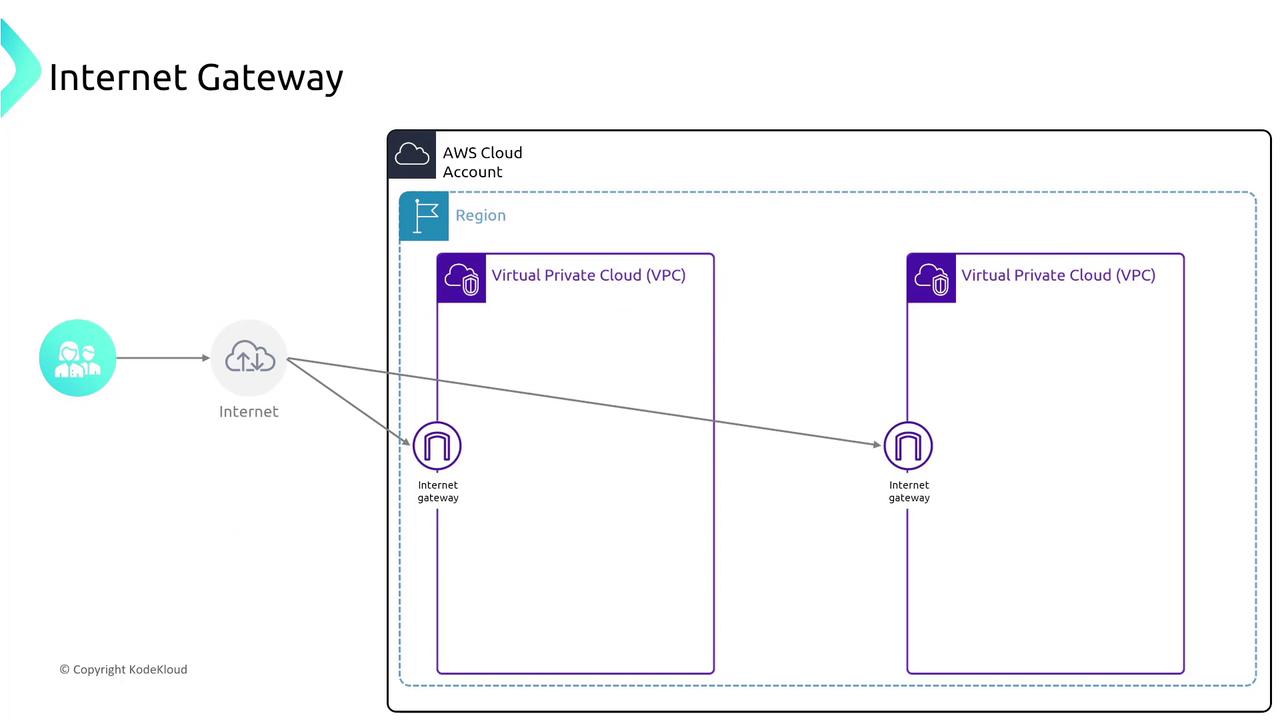
4. Availability Zones and Redundancy
Availability Zones (AZs) can be thought of as separate buildings that are geographically isolated yet interconnected by routing tables. This design maximizes redundancy and security by ensuring isolated and secure traffic flows across distinct locations.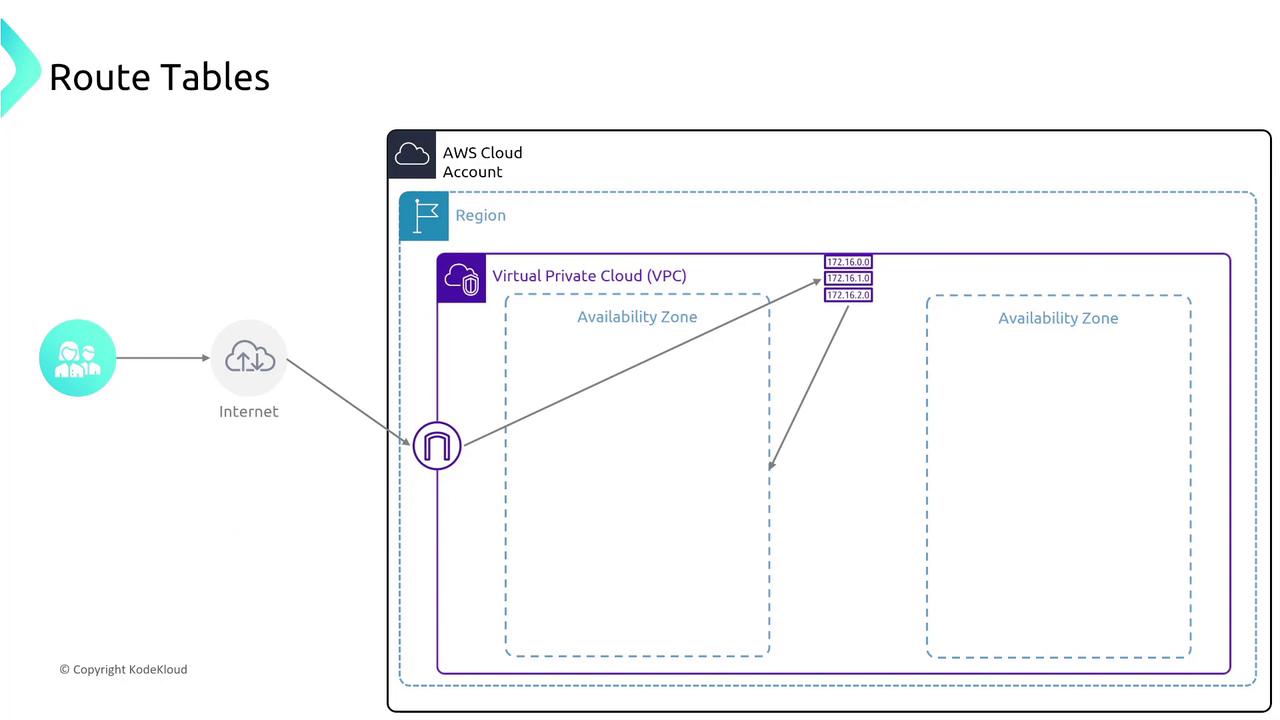
5. Additional Security Measures
To further secure your AWS infrastructure, consider the following:- VPC Endpoints provide private connections to AWS services (such as S3), obviating the need for public internet routes.
- Load Balancers distribute network traffic across multiple instances or subnets to ensure both performance and security.
- For IPv6 traffic, an egress-only Internet Gateway functions similarly to a NAT Gateway by allowing only outbound connections.
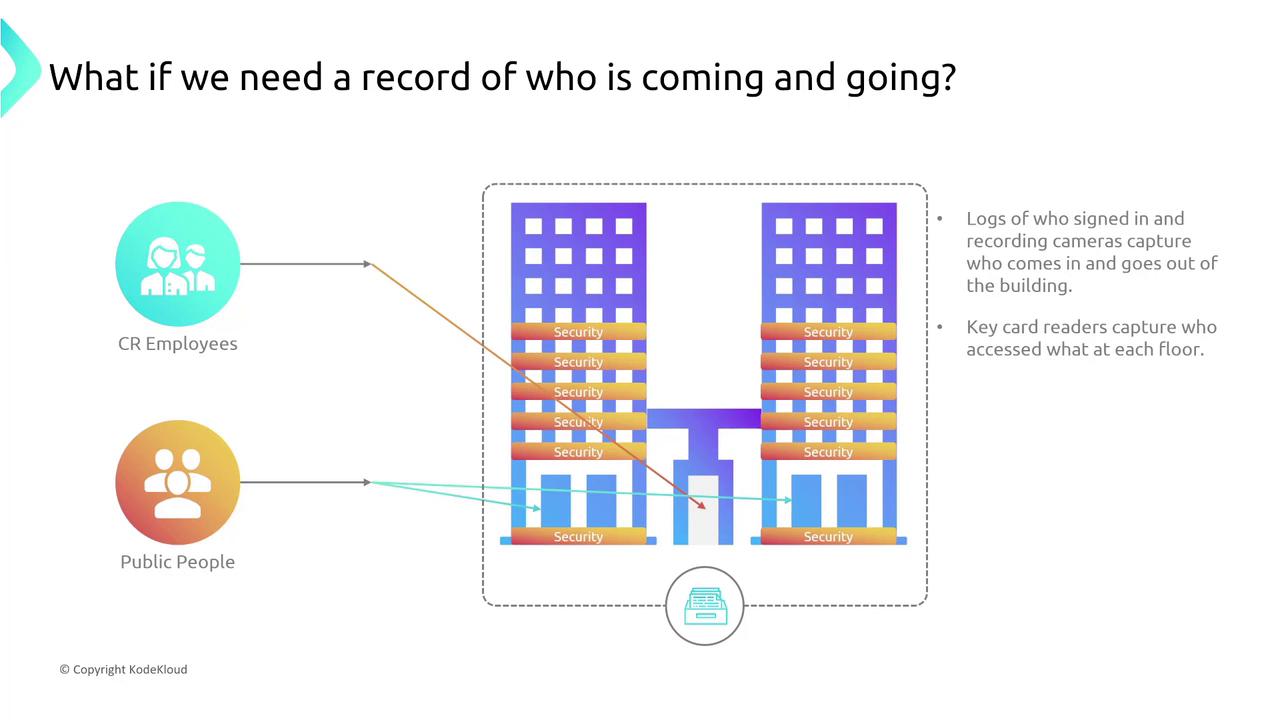
Simplifying Complexity for Secure Design
To summarize your approach:- Understand the security request (e.g., secure data, enforce patch compliance, restrict network access).
- Identify the AWS features and services that address the request.
- Deconstruct complex diagrams by analyzing each component individually (VPC, subnets, NACLs, security groups, gateways, and route tables).
- Design solutions that strike an optimal balance between robust security, cost-effectiveness, and operational simplicity.
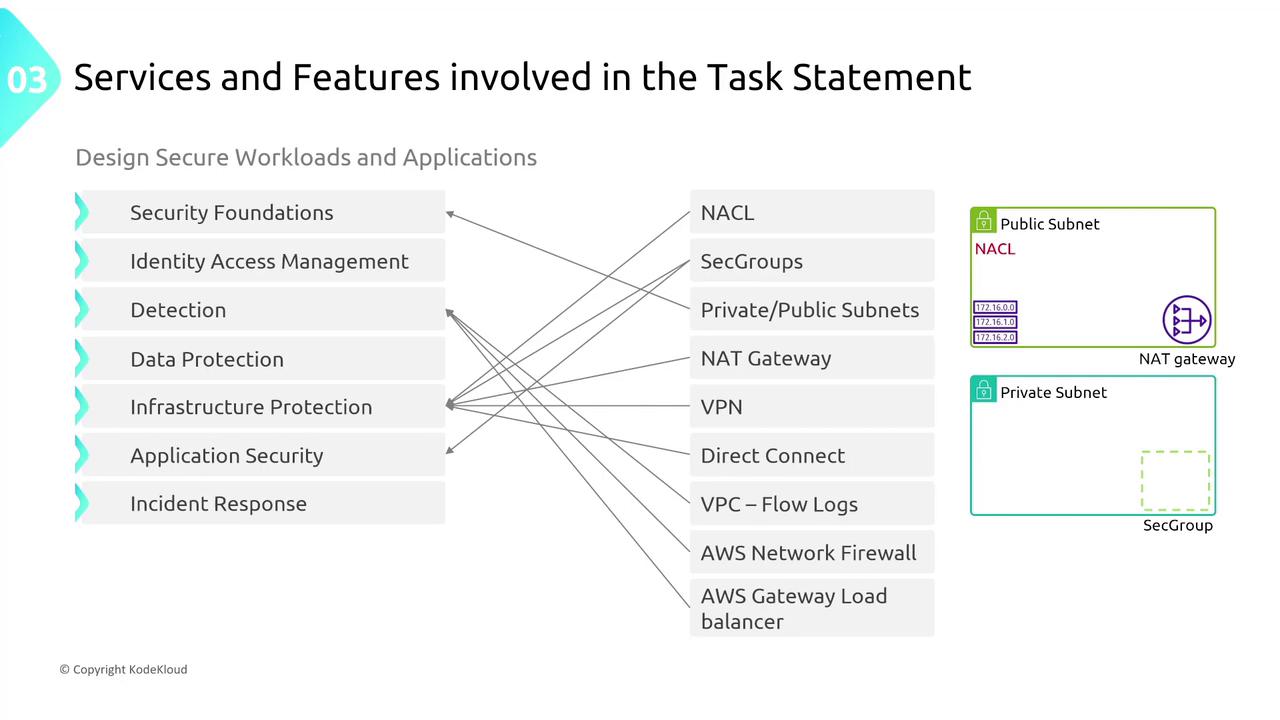
Keep in mind that while these examples pertain to exam scenarios, staying current with AWS documentation is crucial in real-world applications.