Auto-Scaling and Its Security Implications
Auto-scaling is a prominent feature in the AWS environment, particularly for EC2. Although its primary purpose is dynamic resource management rather than security, understanding its interplay with AWS security services is crucial. For example, when considering which IAM entity supplies the permissions needed for EC2 auto-scaling, the answer is service-linked roles. These built-in roles grant the necessary privileges to launch instances without adding extra security layers.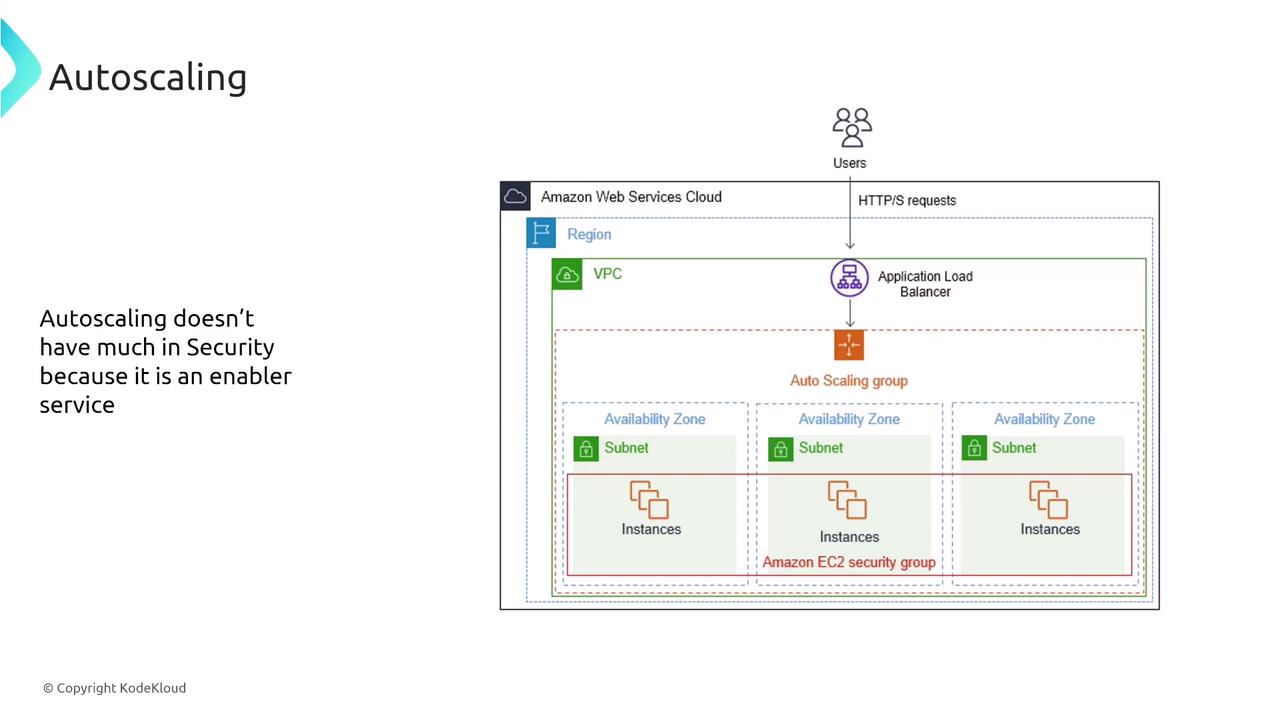
Elastic Load Balancers and Their Security Features
Elastic Load Balancers (ELBs) are available in three types. Each type offers distinct security functionalities to protect and manage traffic. Below, we review the key characteristics of Application Load Balancers (ALB) and Network Load Balancers (NLB).Application Load Balancers (ALB)
Operating at Layer 7 of the OSI model, ALBs provide application-level security features. Key benefits include:- Security Groups: Applied to control inbound and outbound traffic.
- Authentication Support: Integration with Amazon Cognito to authenticate incoming requests.
- SSL Termination: Uses SSL certificates sourced from AWS Certificate Manager with automated renewal.
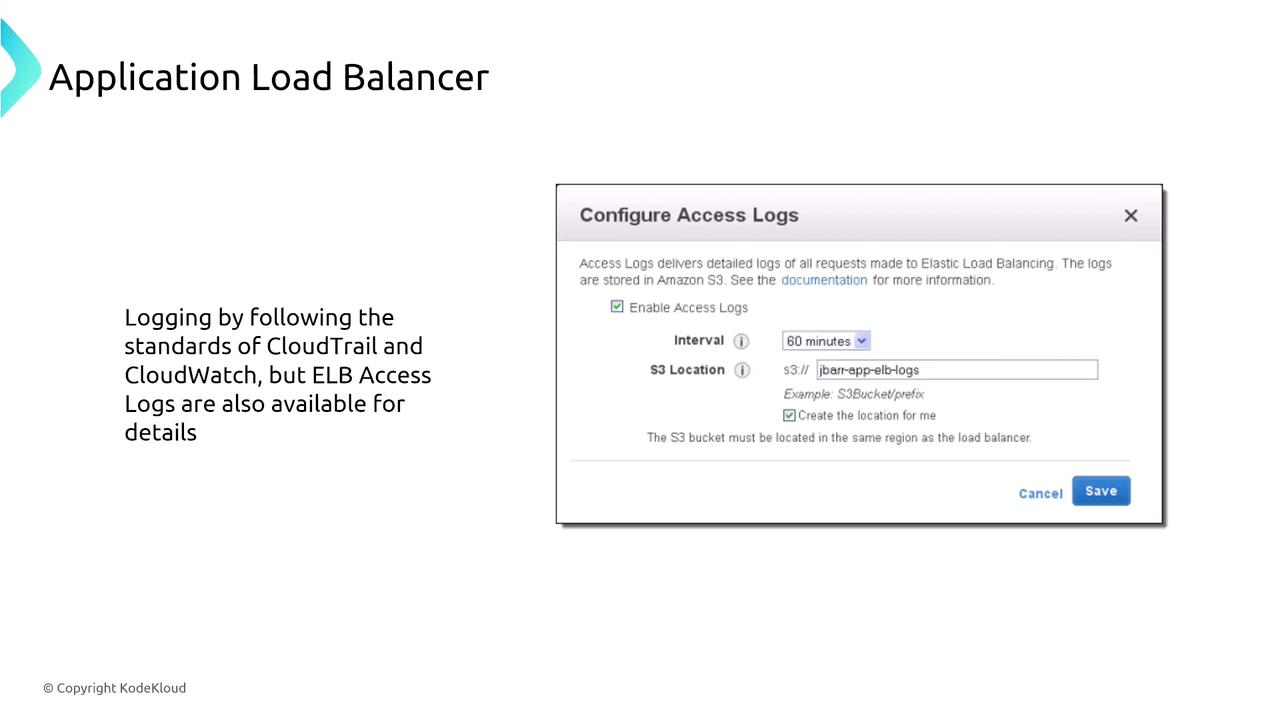
- Logging: Supports access logs (sent to an S3 bucket), API call logs via CloudTrail, and operational metrics through CloudWatch.

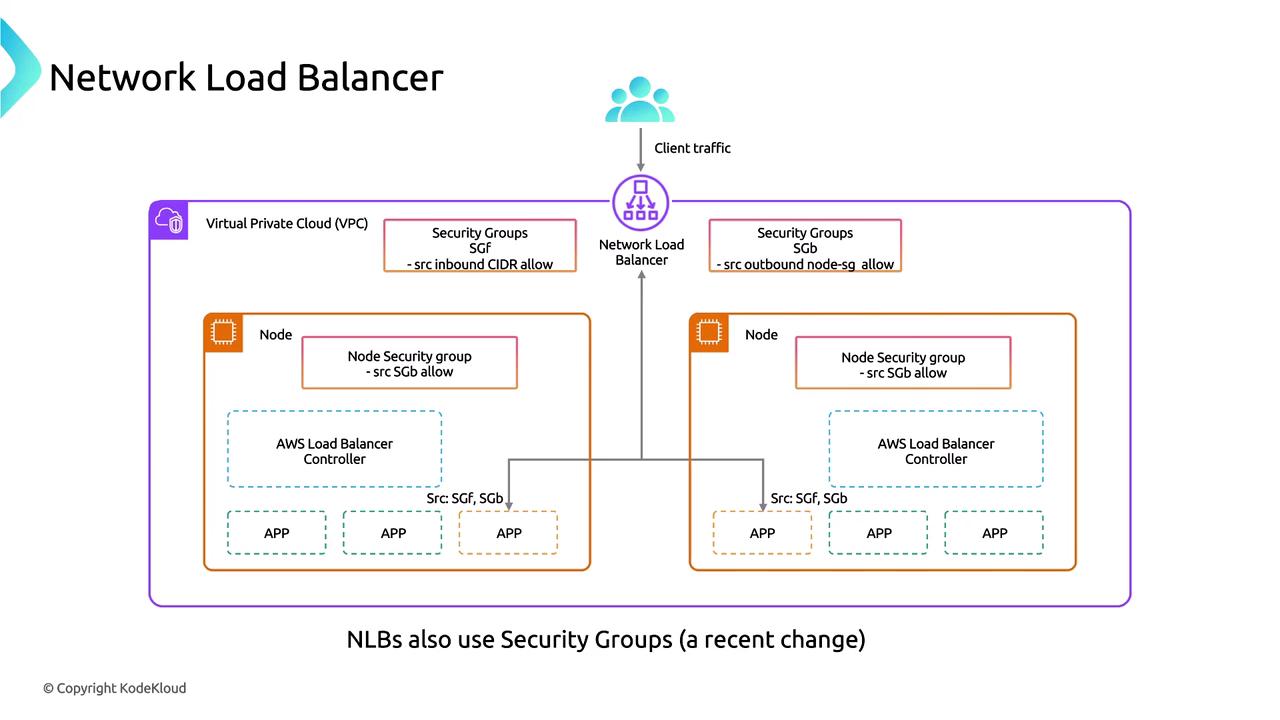
Network Load Balancers (NLB)
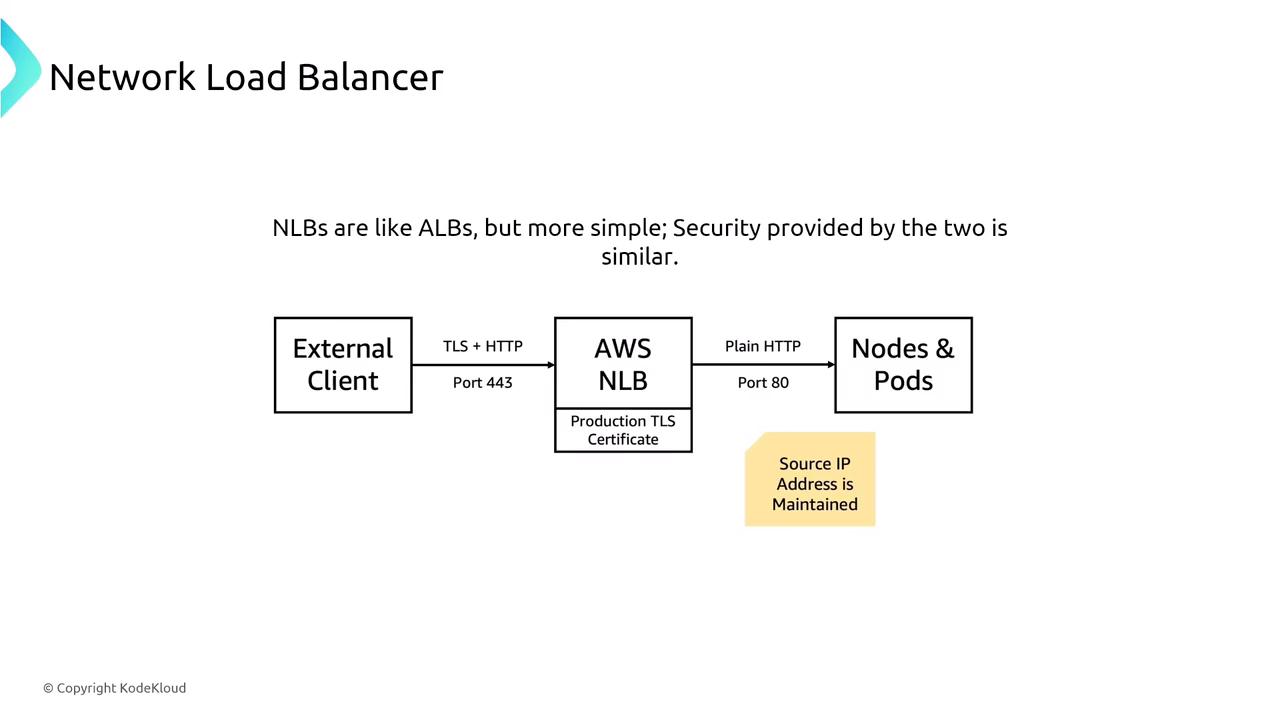
Operating at Layer 4, NLBs are optimized for handling TCP and TLS traffic. Their key features include:- TLS Support: Provides TLS termination ensuring in-transit encryption.
- Security Groups: Now supports security groups for controlling traffic, in addition to subnet-level NACLs.
- Access Logging: Available for TLS listeners, similar to ALB.


Gateway Load Balancer (GLB)
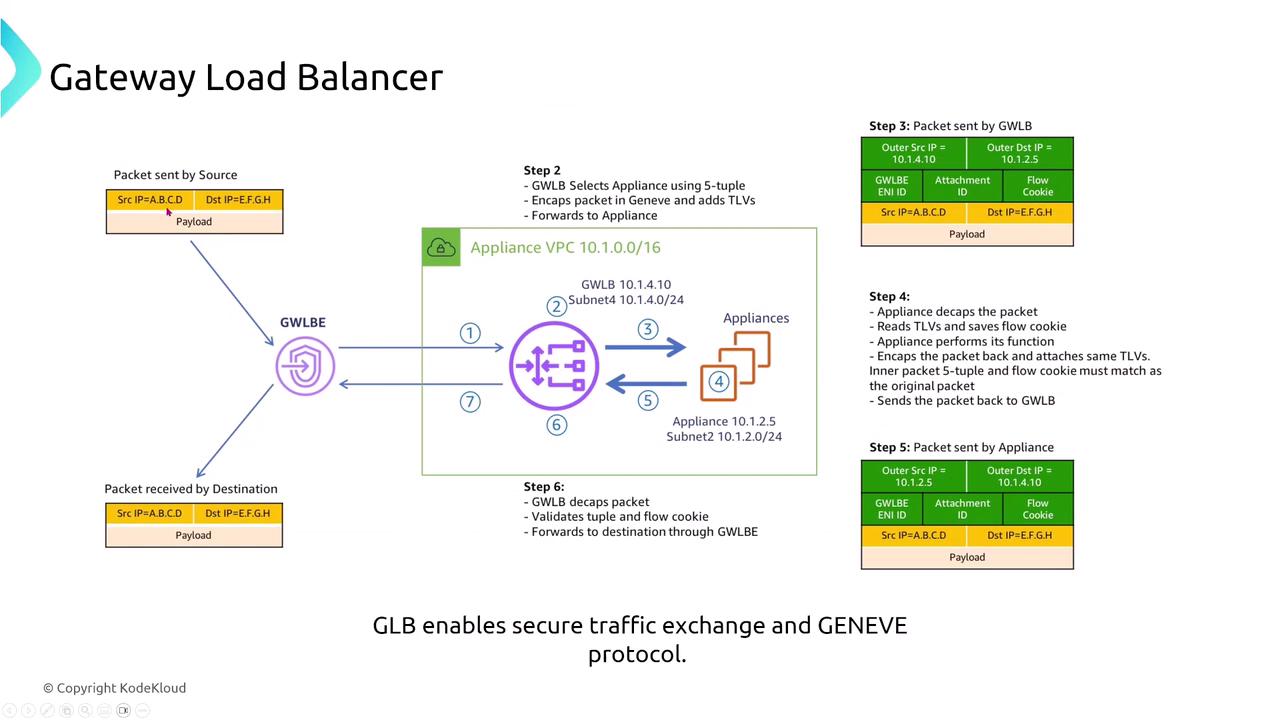
The Gateway Load Balancer (GLB) functions as a security appliance, intercepting all incoming traffic at its endpoint. It forwards traffic to one or more virtual appliances (up to 1,500), allowing these appliances to analyze and decide whether to permit or block the traffic. This mechanism is particularly useful when secure, private connectivity across VPCs is required. Key features include:- Endpoint Security: Although GLBs lack direct security groups, endpoint access can be managed through routing tables and sometimes endpoint-attached security groups.
- Multi-account Restrictions: You can limit which AWS accounts are authorized to create endpoints by configuring the GLB to allow only specific principals.
- Geneve Protocol: The GLB leverages the Geneve protocol (Generic Network Virtualization Encapsulation) to intercept and encapsulate traffic, adding metadata for network virtualization and specialized appliance functions.
- Monitoring: Integration with CloudWatch and support for VPC flow logs enables comprehensive monitoring of traffic.


For detailed monitoring of traffic on specific network interfaces, enable VPC flow logs. This provides low-level network data compared to CloudTrail, which logs only API calls.
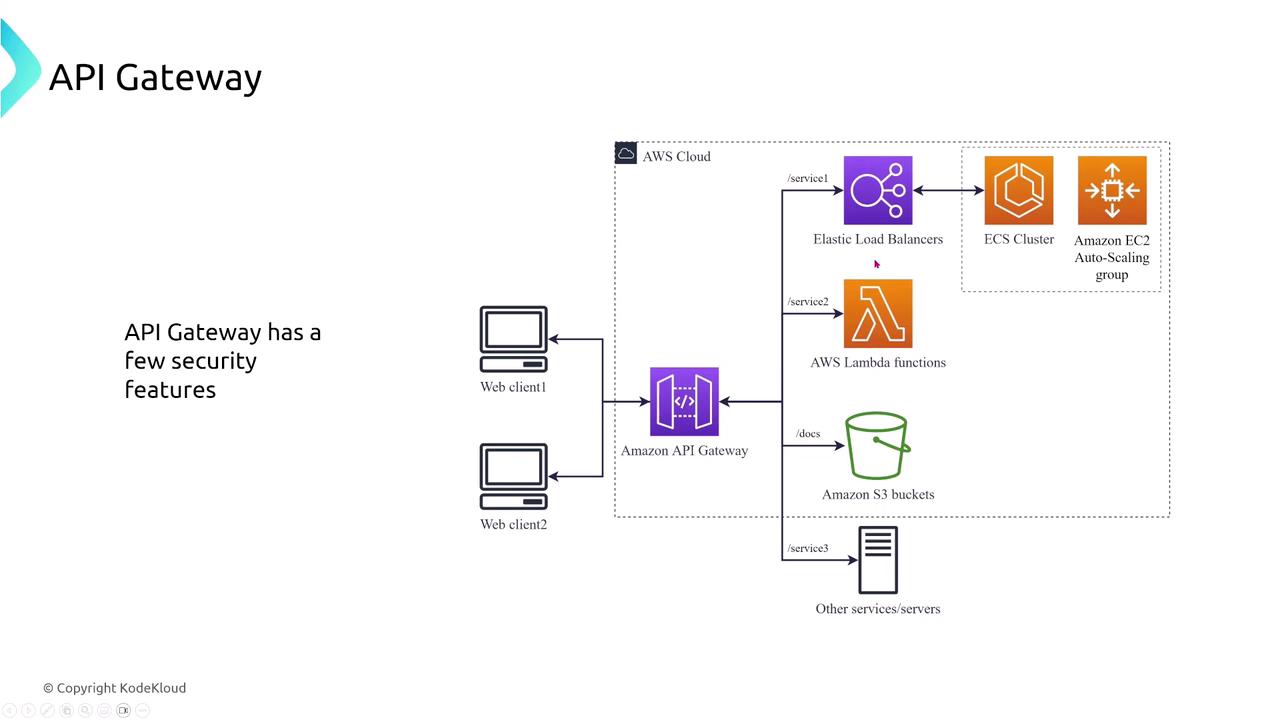
API Gateway Security Features
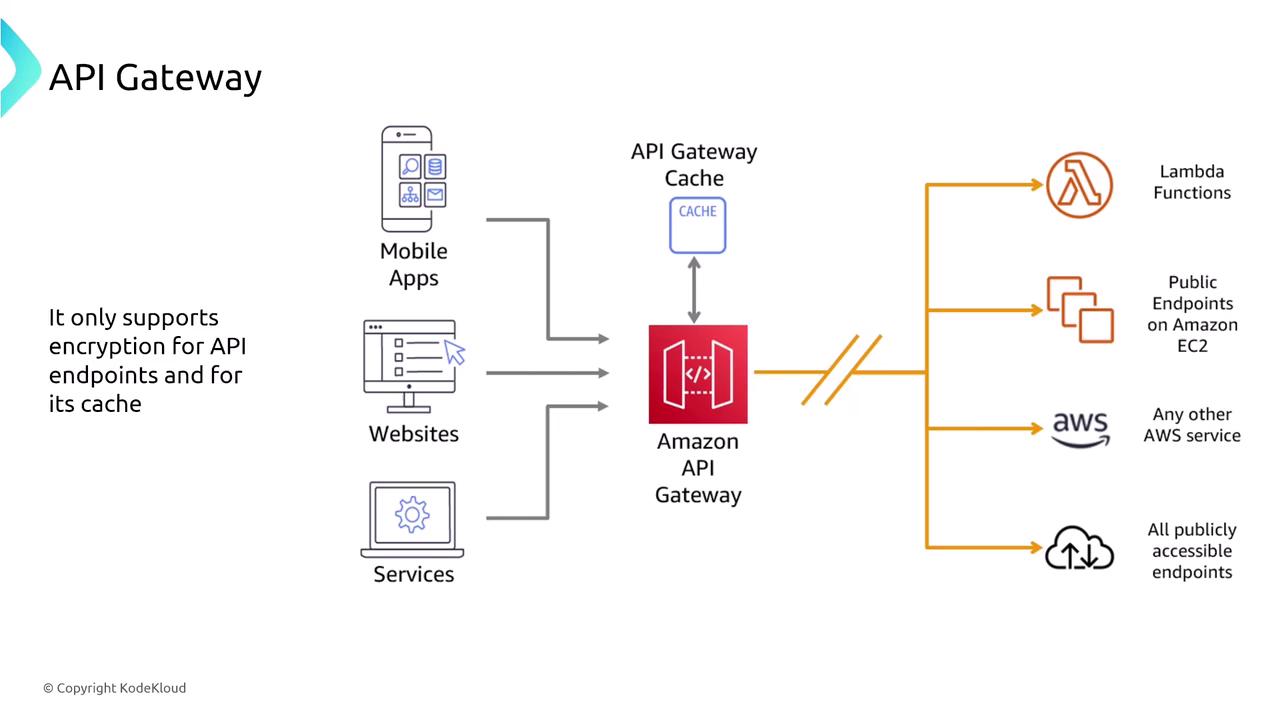
API Gateway serves as the entry point for accessing backend services and offers distinct security features compared to load balancers. Its capabilities include:- Encryption: Endpoints are secured using SSL/TLS, and cached responses can also be encrypted.
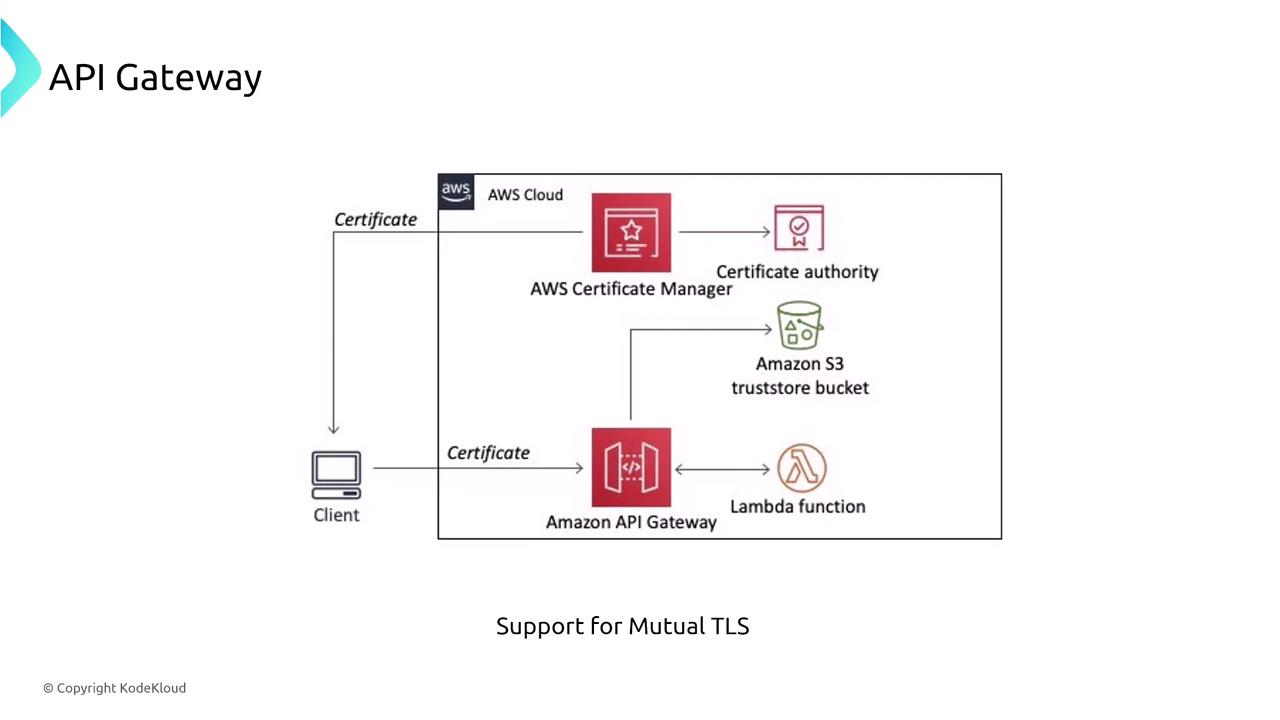
- Mutual TLS: Ensures both the client and server mutually authenticate each other.
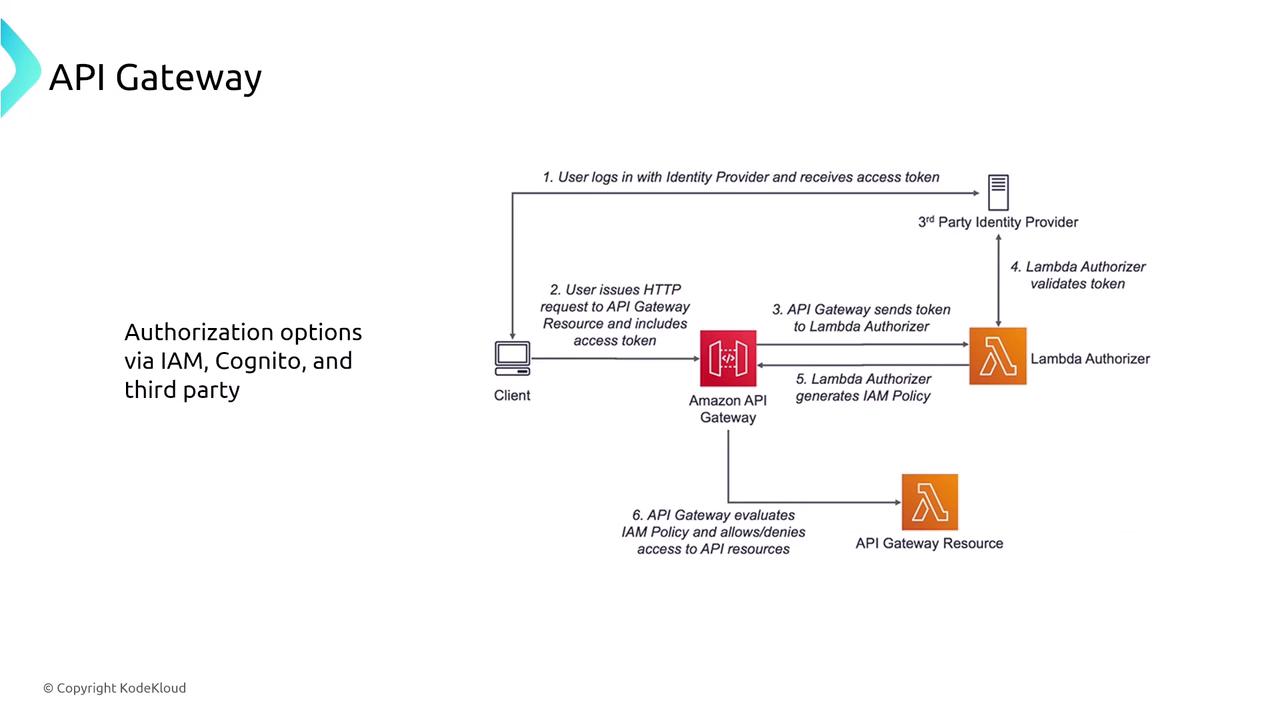
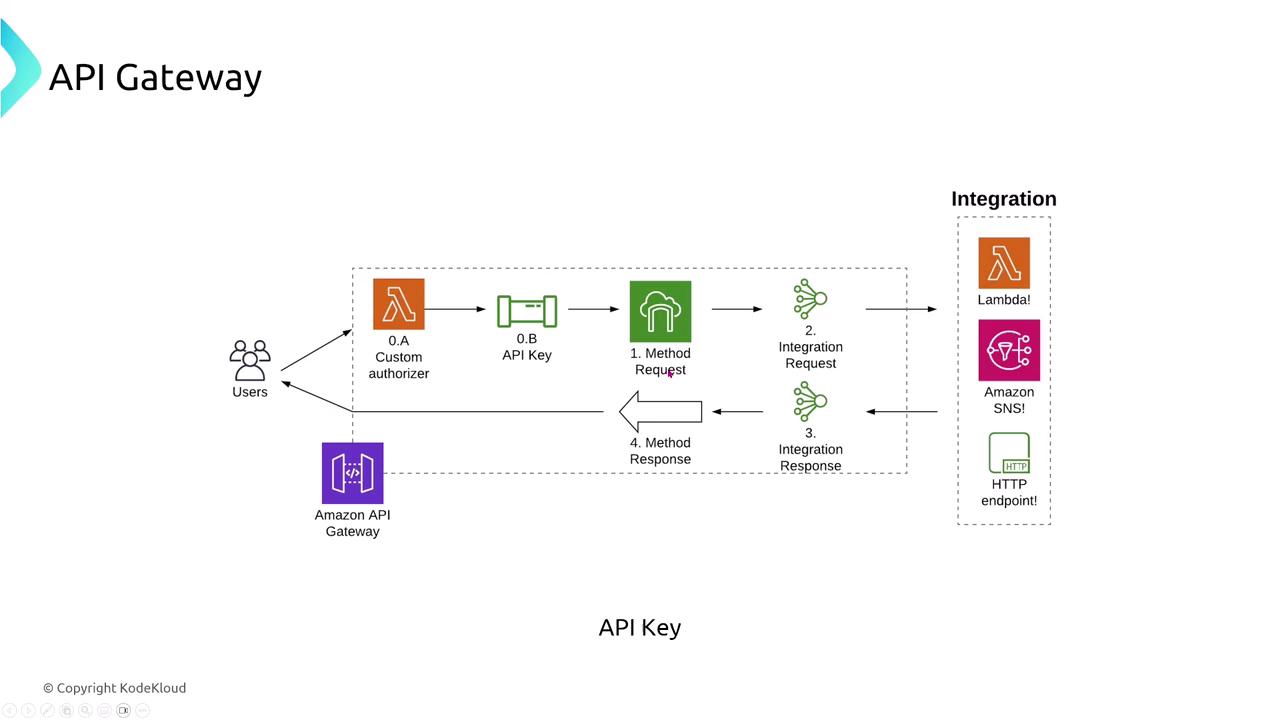
- Custom Authorization: Offers several authentication options, including Lambda Authorizers for custom logic.
- Usage Plans and Throttling: Protects backend resources by supporting quotas and rate limiting.
- Logging and Tracing: CloudWatch Logs, detailed metrics, and X-Ray tracing provide comprehensive visibility into API activity.