MemoryDB for Redis
MemoryDB for Redis is a fully managed, persistent in-memory database service that runs a Redis-compatible engine. It employs a primary-replica architecture where a primary node handles write operations while replica nodes serve read requests through a configuration endpoint.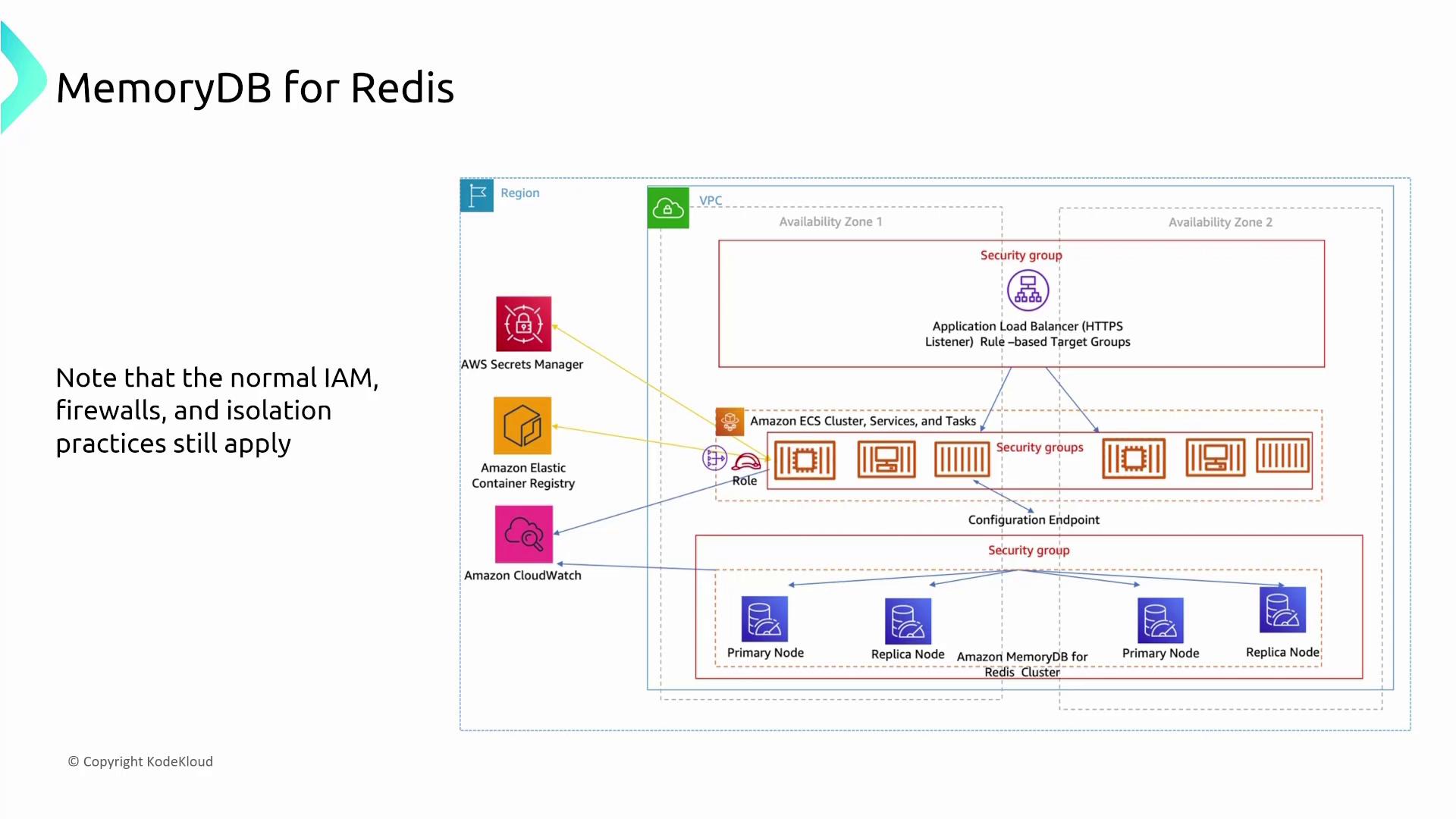
- Replication across multiple availability zones.
- Microsecond read latencies comparable to ElastiCache.
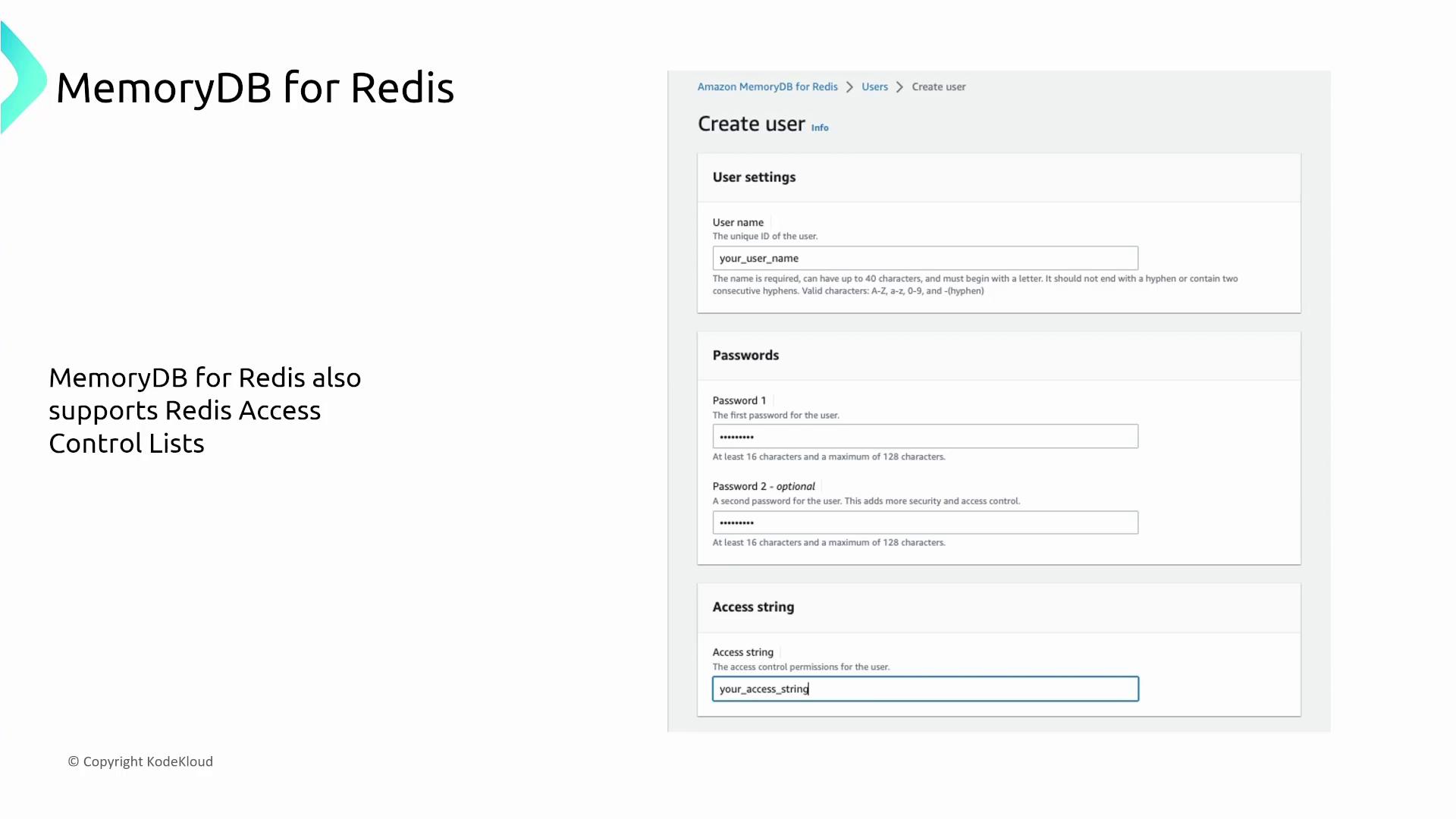
- Support for Redis Access Control Lists (ACLs) to enforce command- and key-level permissions. Note that while IAM policies control resource-level access (e.g., console/API operations), Redis ACLs strictly manage access within the database.
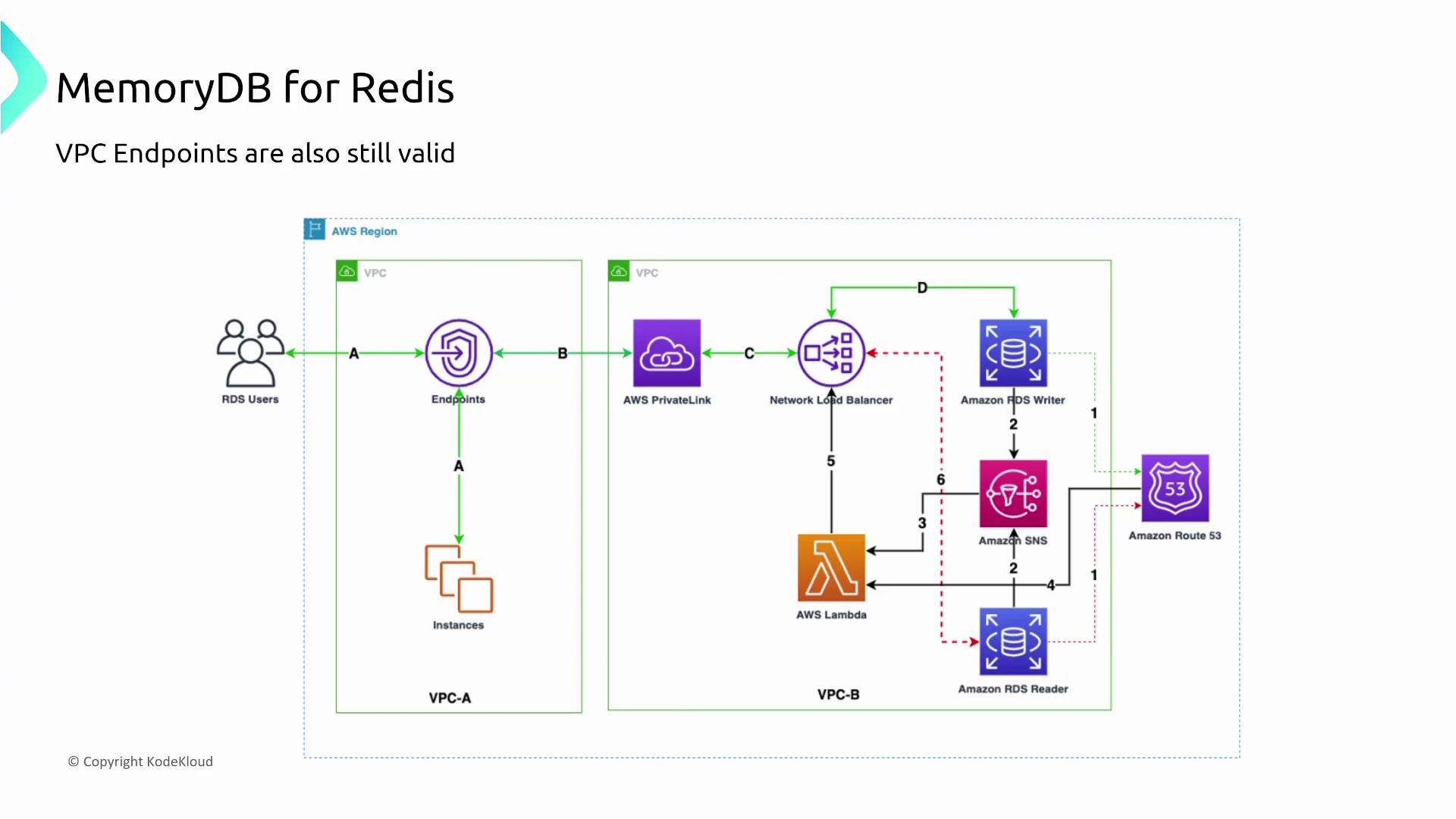
- Support for VPC interface endpoints for private connectivity.
- Non-support of gateway endpoints.
- Utilization of standard AWS data transfer paths without bypass or acceleration.
Security Features
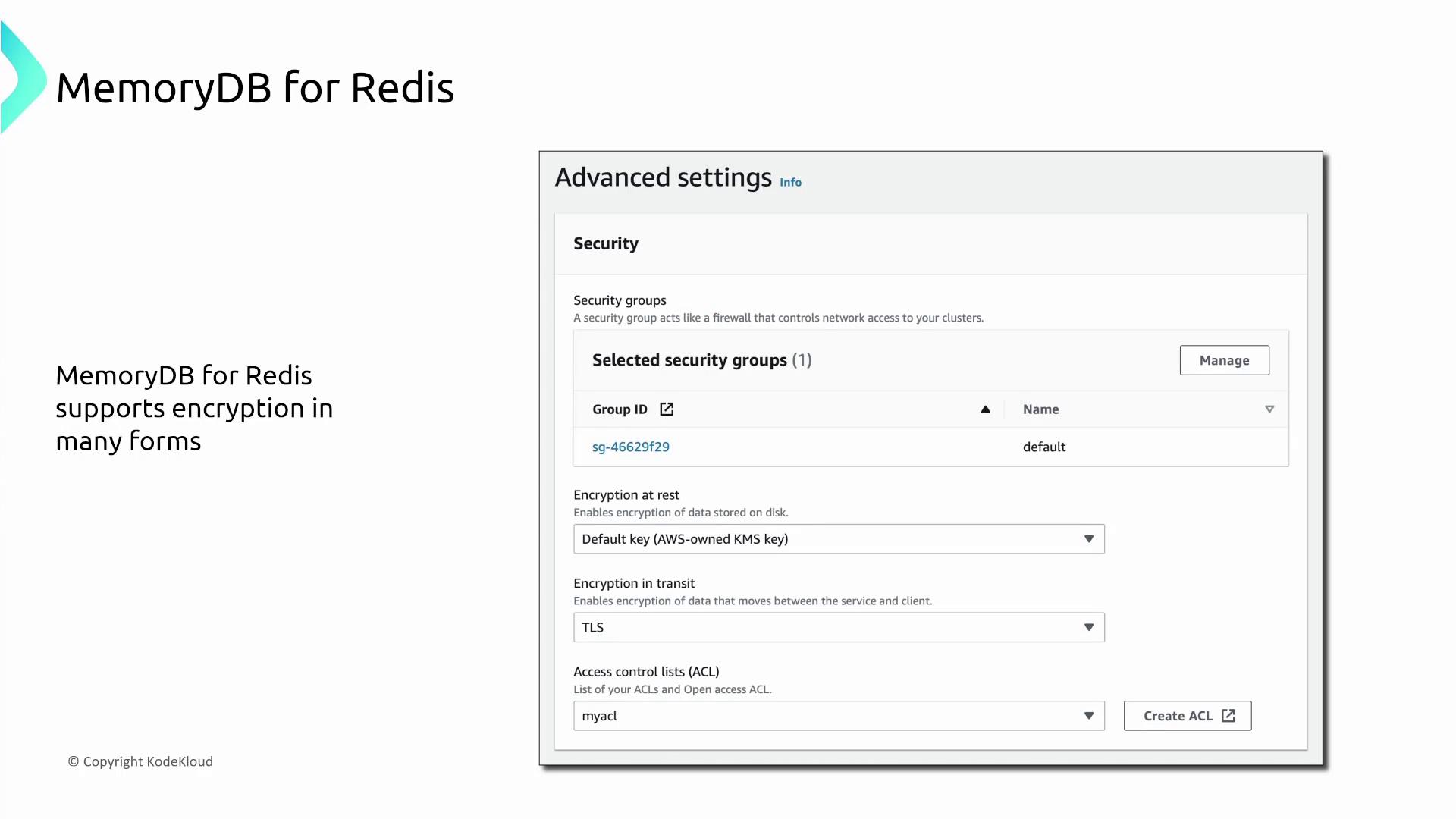
MemoryDB for Redis offers robust encryption and security:- Encryption at rest using AWS Key Management Service (KMS).
- Encryption in transit via TLS.
- Use of Redis ACLs for detailed command and key-level control.
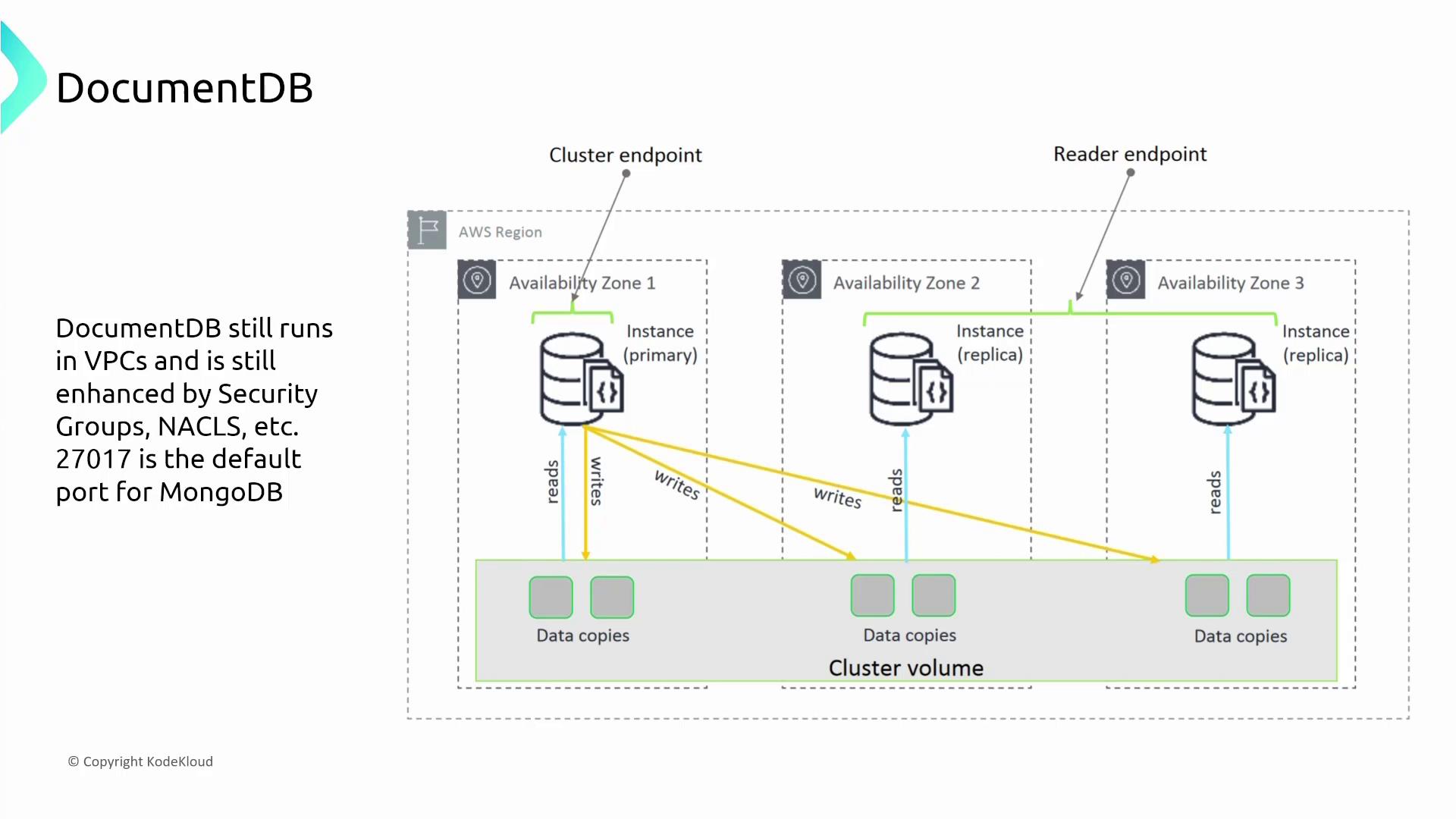
DocumentDB
Amazon DocumentDB is a MongoDB-compatible document database service that provides native username/password authentication for client connections. For administrative operations, access is governed by IAM roles.
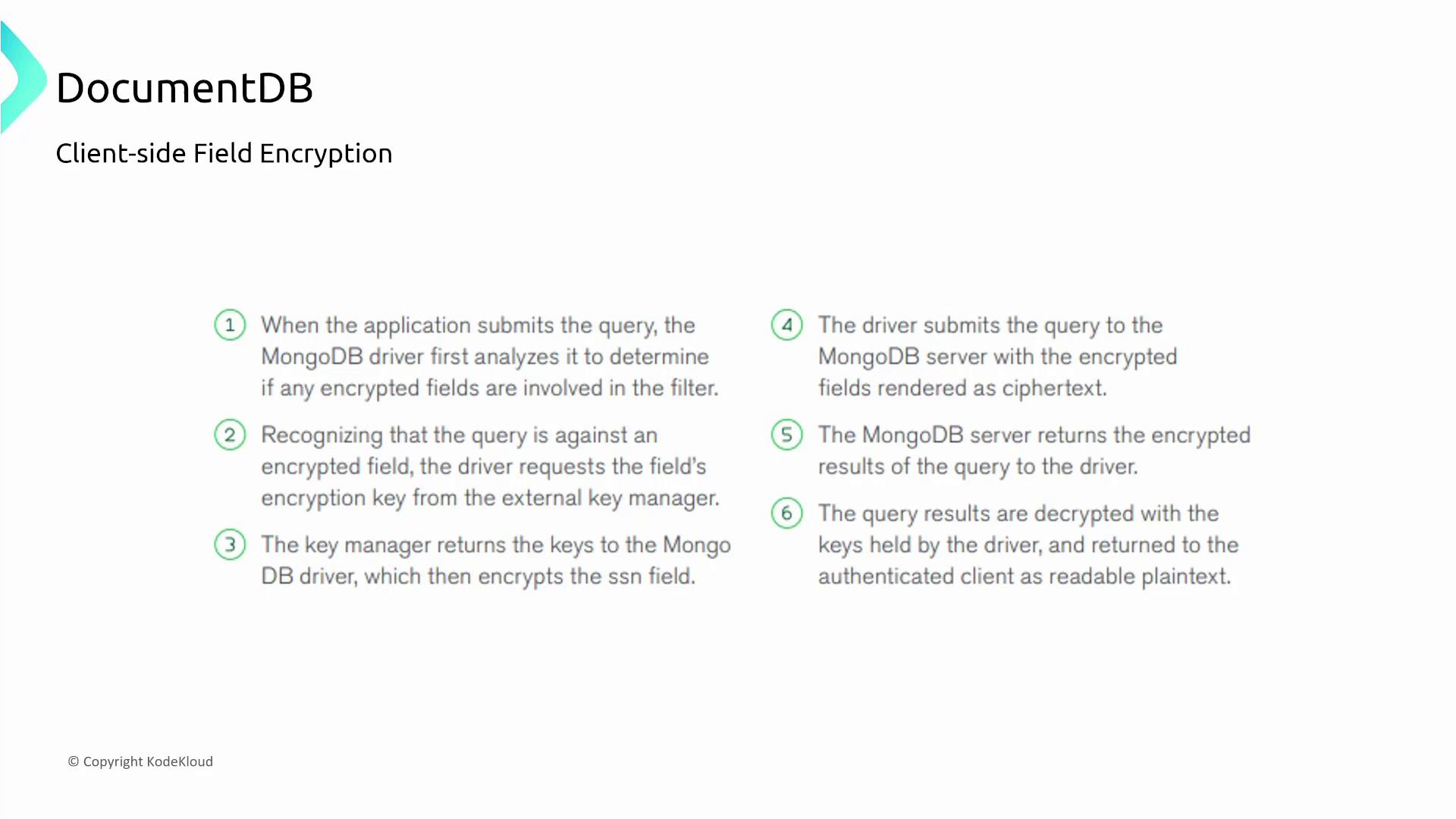
Client-Side Field Encryption
DocumentDB supports client-side field encryption processed by the MongoDB driver. When querying an encrypted field, the process involves:- Detecting the encrypted field.
- Requesting the required encryption key from an external key manager (typically AWS KMS).
- Encrypting the field before query submission.
- Decrypting the response on the client side using the decryption key.
- Create an encryption key using AWS KMS.
- Associate the key with an appropriate IAM role.
- Configure your application to interact with AWS KMS during CRUD operations.
Monitoring and Detection
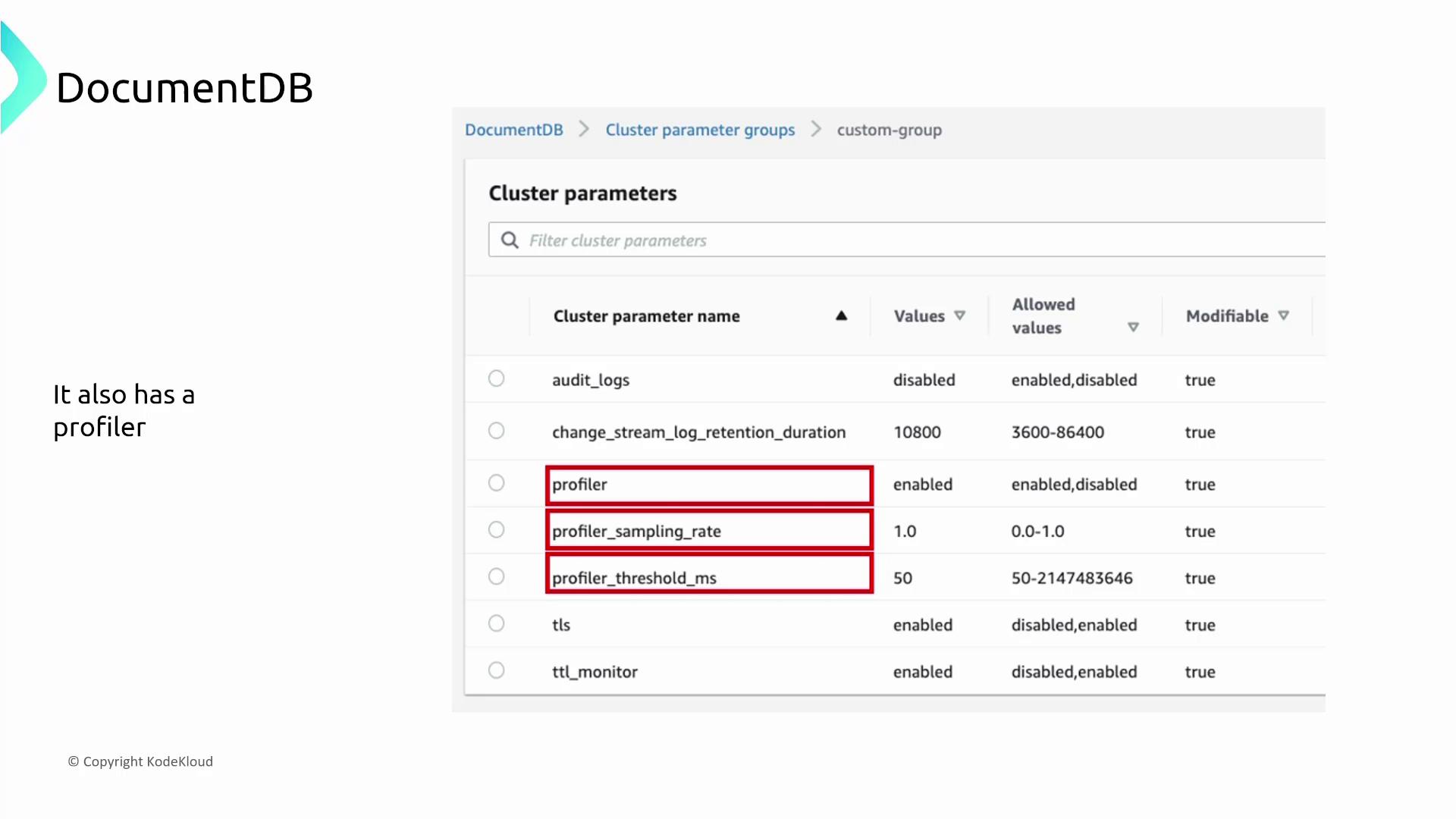
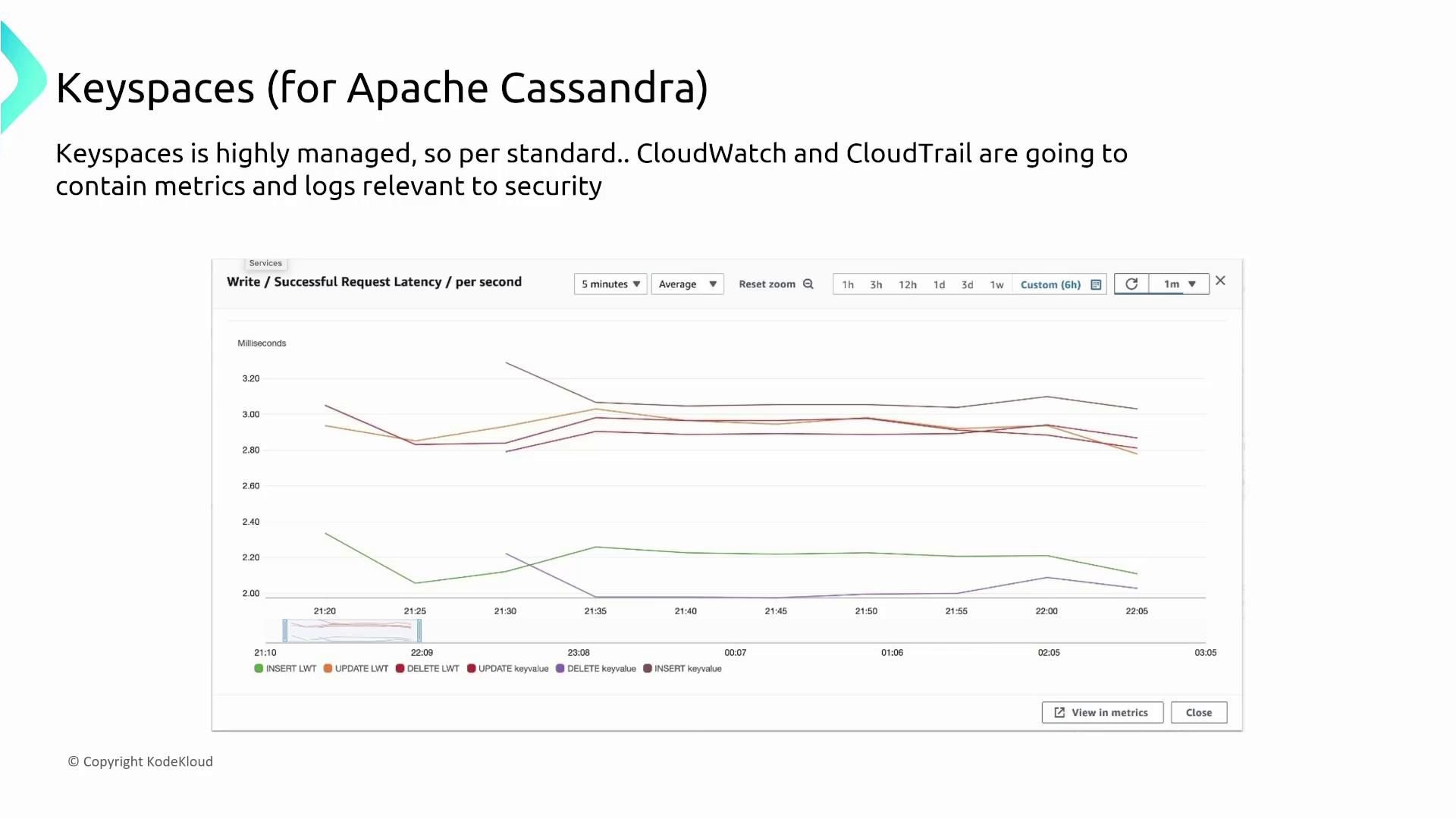
DocumentDB leverages CloudWatch for performance monitoring. CPU utilization is typically the first metric that indicates cluster activity. Additionally, a built-in profiler logs slow operations to diagnose performance issues. Audit logs further support detailed tracking of database events.
Keyspaces for Apache Cassandra
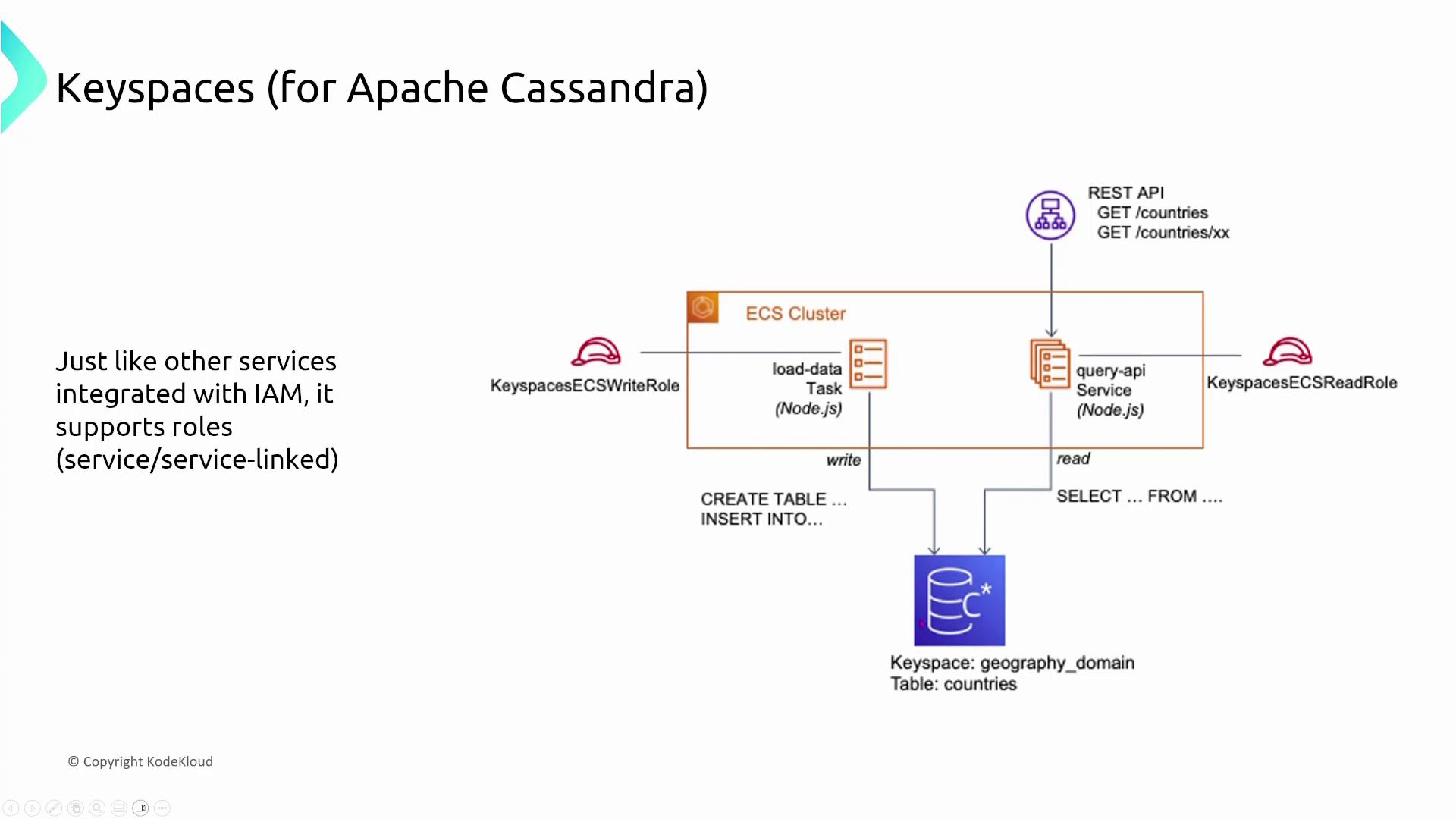
Amazon Keyspaces is an AWS-managed service that is compatible with Apache Cassandra. It exclusively uses IAM for both authentication and authorization, in contrast to DocumentDB’s native username/password approach. For example, the following snippet shows how Secrets Manager is used to manage credentials in the setup script:
Security and Encryption
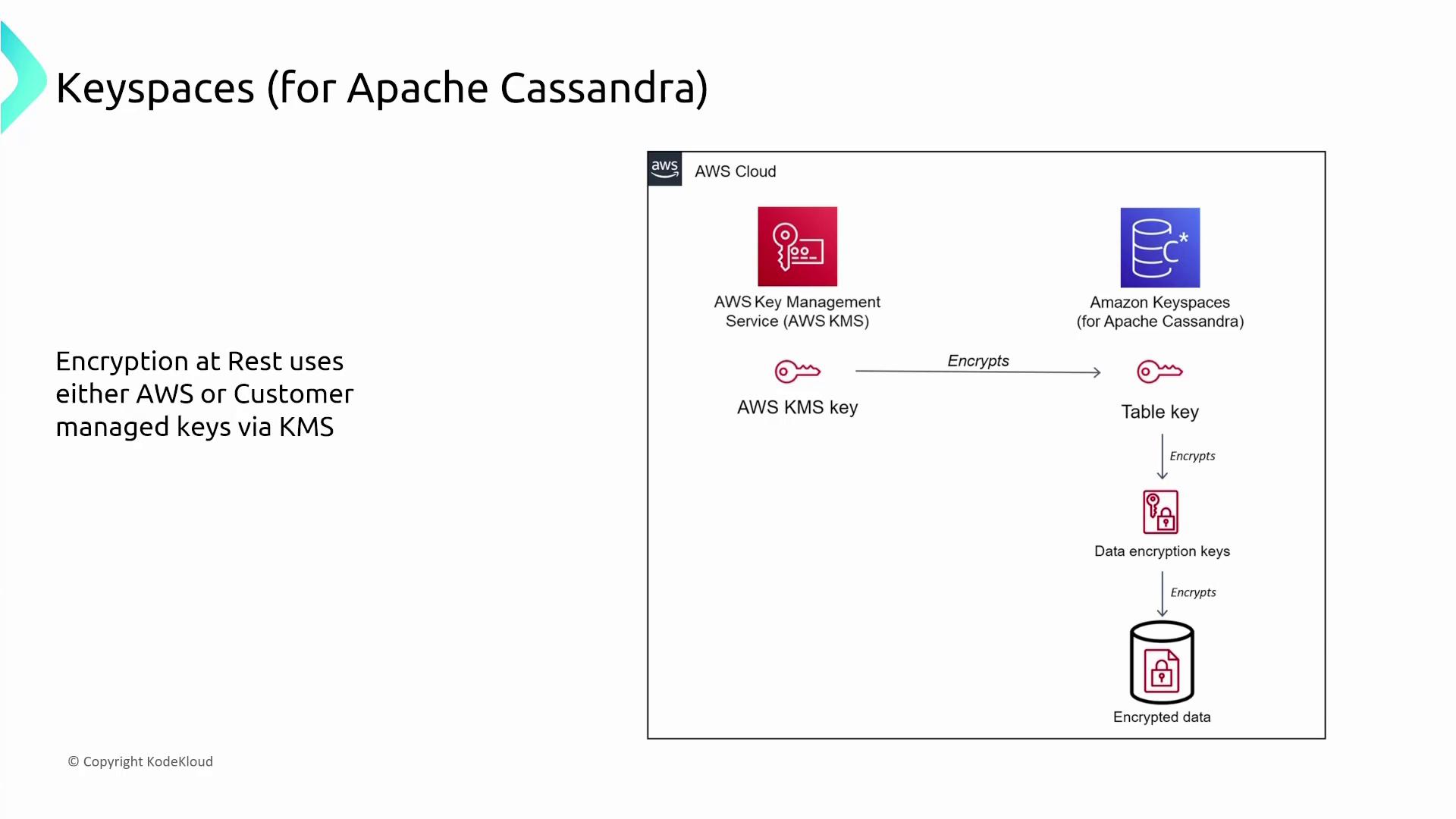
Key security features for Keyspaces include:- Encryption at rest using AWS KMS (with AWS-managed or customer-managed keys).
- Encryption in transit by default via TLS.
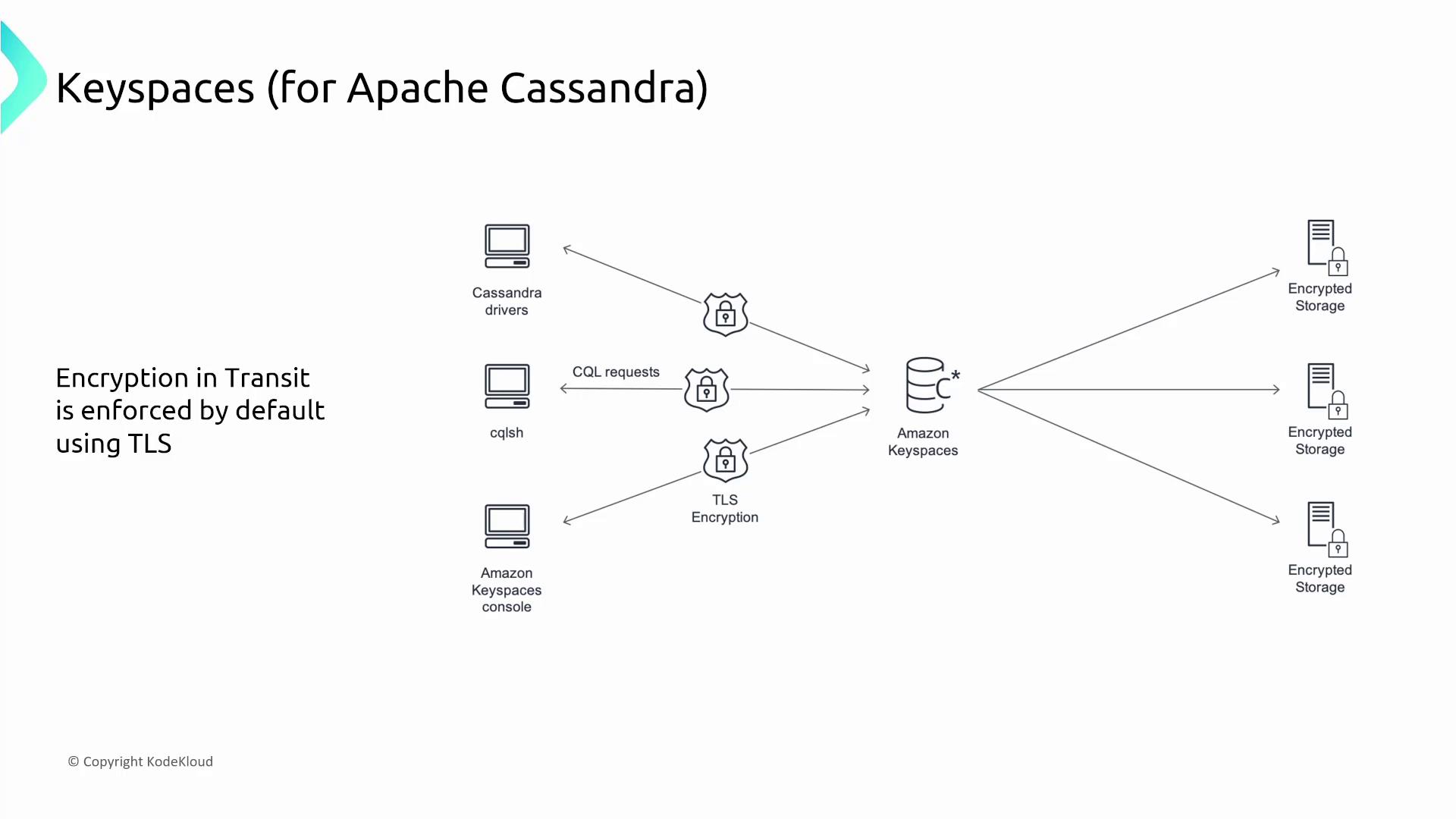
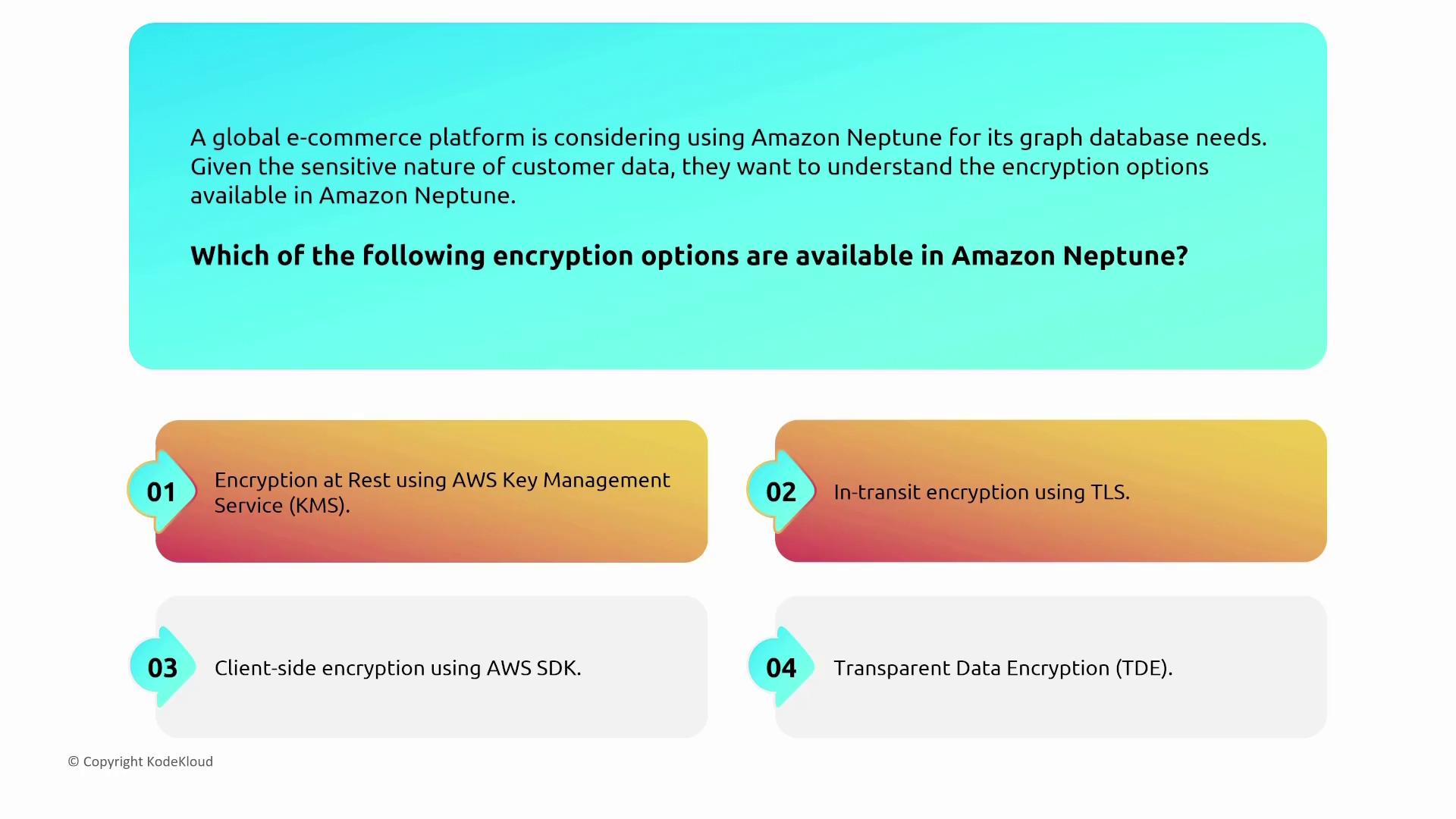
Neptune
Amazon Neptune is a managed graph database service similar to Neo4j. It supports both IAM database authentication and local user authentication for application-level management.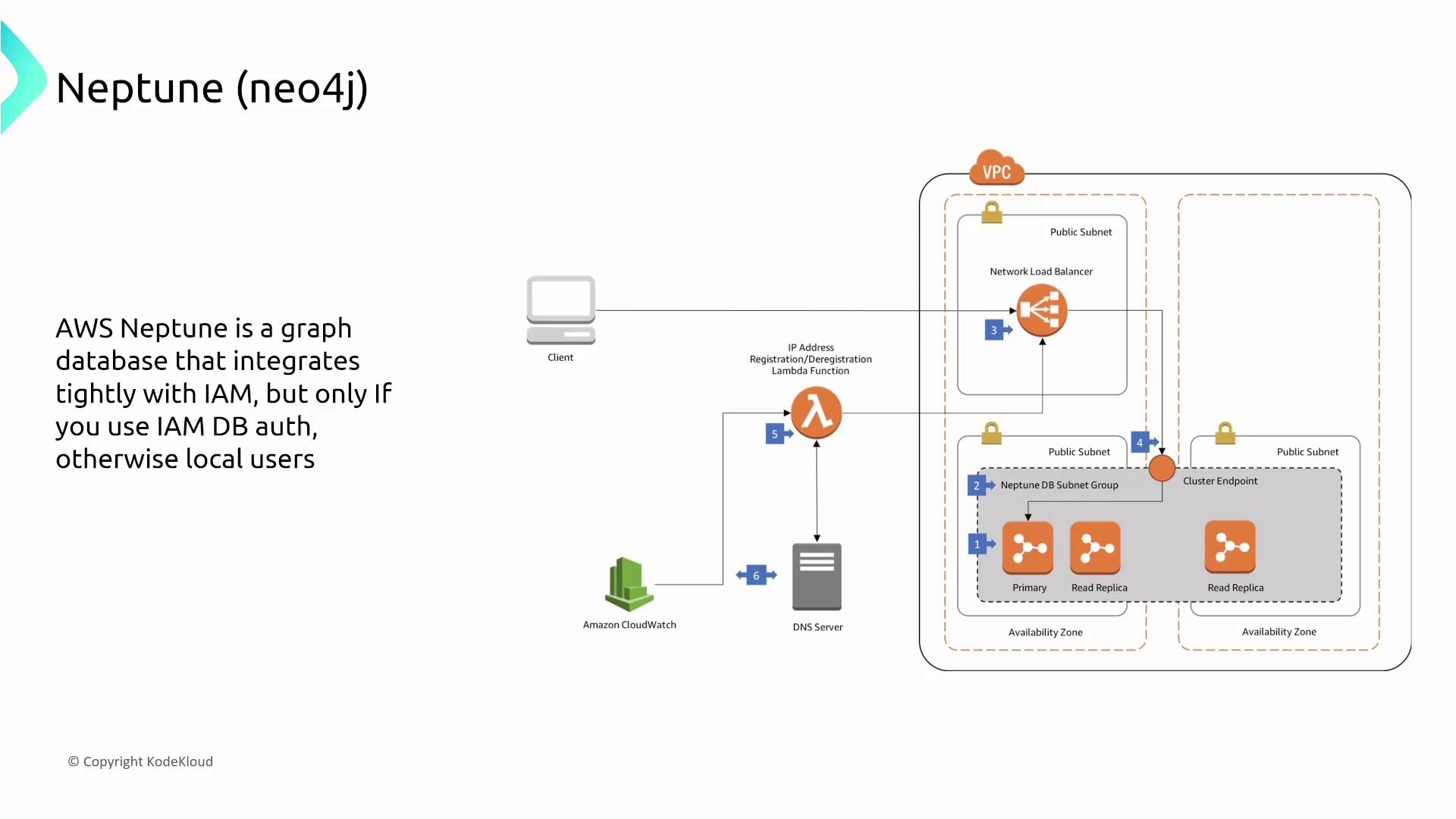

- Encryption at rest via AWS KMS.
- In-transit encryption using TLS.
Monitoring and Logging
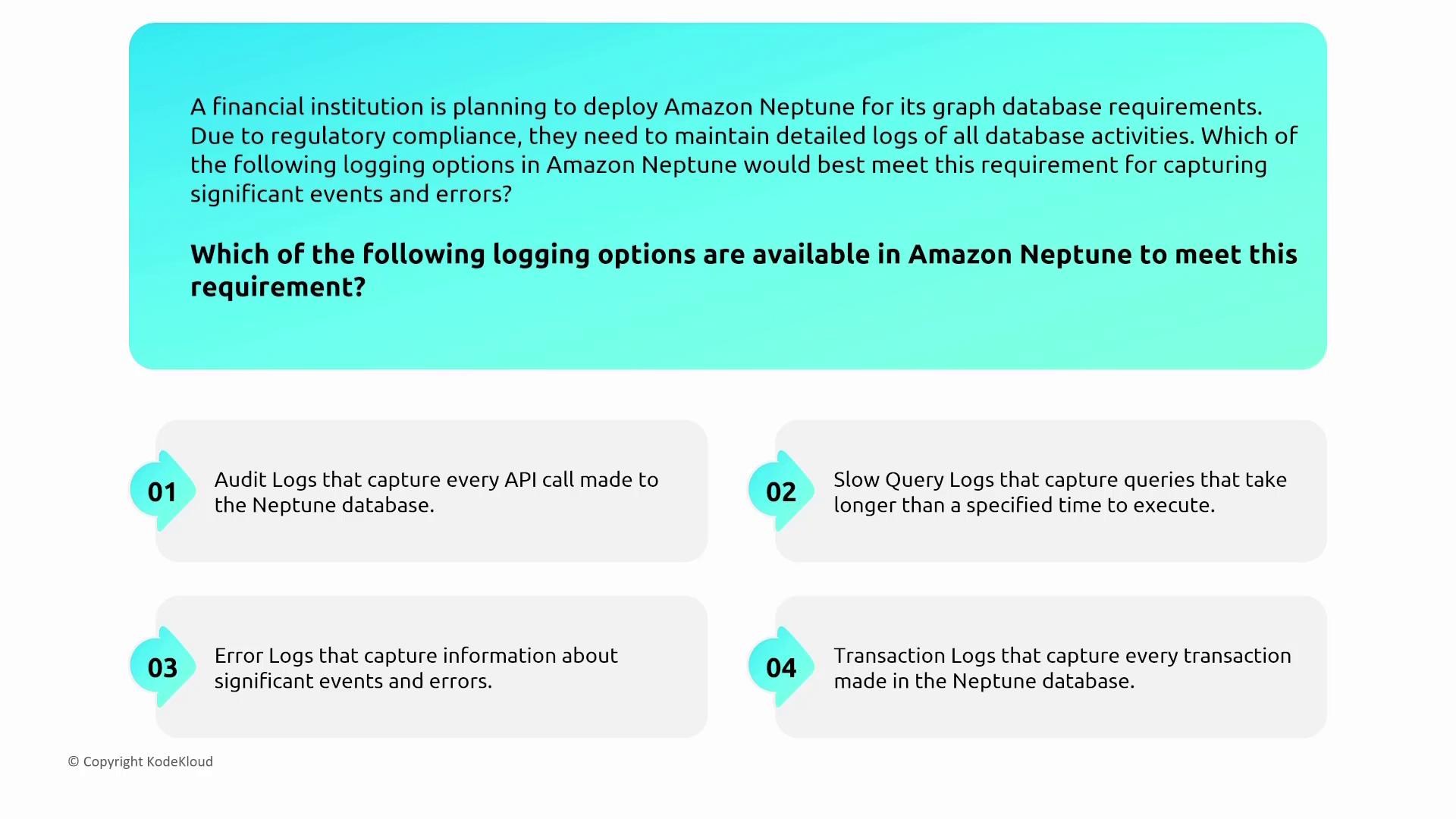
Neptune leverages CloudWatch for monitoring and CloudTrail for auditing API calls. Although native slow query logs are not available, error logs and cluster status events play an essential role in troubleshooting.Audit logs are available in Neptune, which assist in tracking database events for compliance and performance troubleshooting.
This comprehensive overview has covered the security design and operational details for MemoryDB for Redis, DocumentDB, Keyspaces for Apache Cassandra, and Neptune. By leveraging AWS-managed features such as VPC isolation, IAM, encryption, and monitoring, you can design robust and secure database architectures on AWS. For more detailed information, consider exploring: