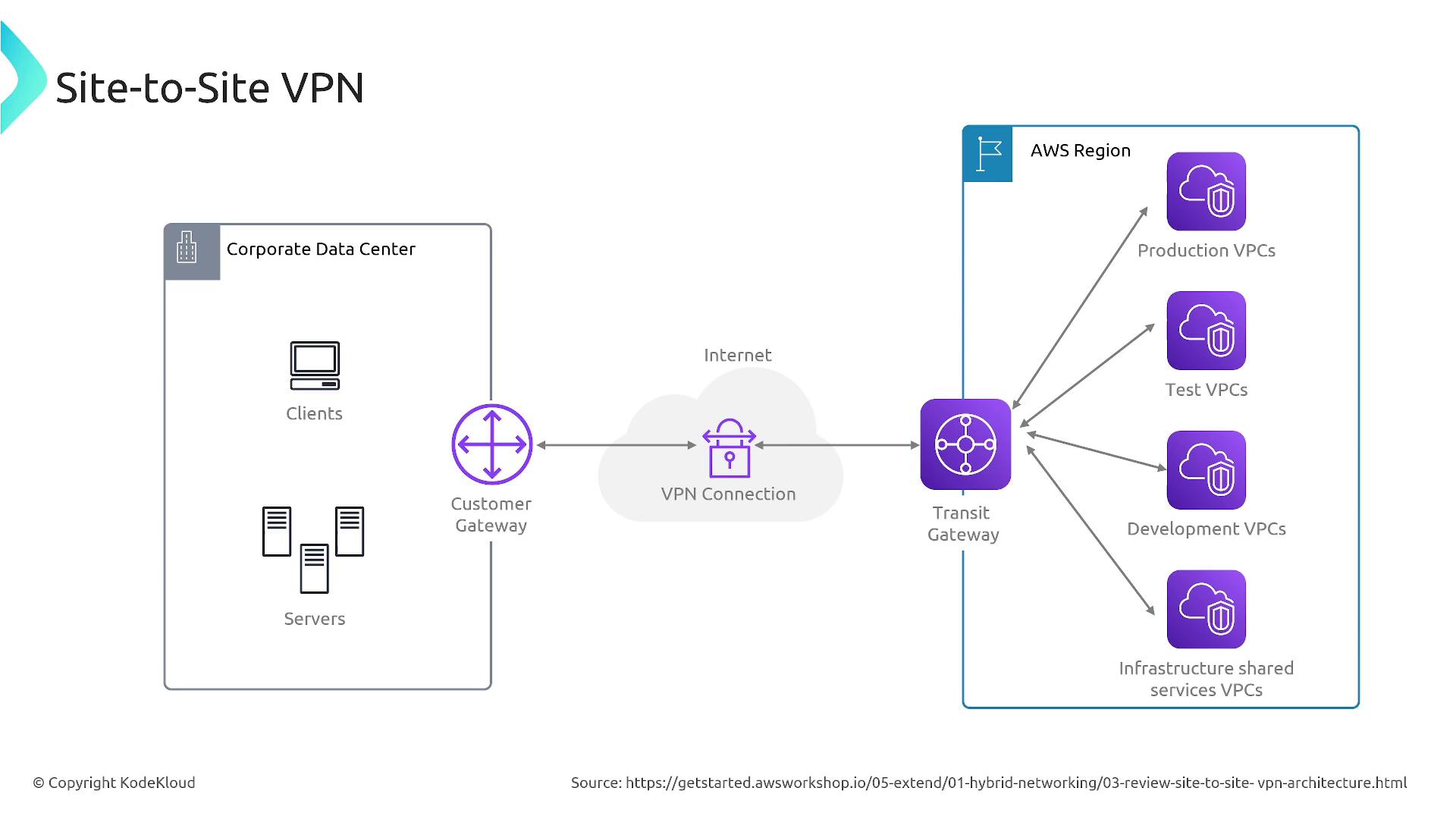
Site-to-Site VPN
Site-to-Site VPN secures the connection between an on-premises network and an AWS VPC over the public internet using an encrypted IPSec tunnel. This configuration is ideal for organizations that need to extend their data centers into the AWS cloud.How It Works
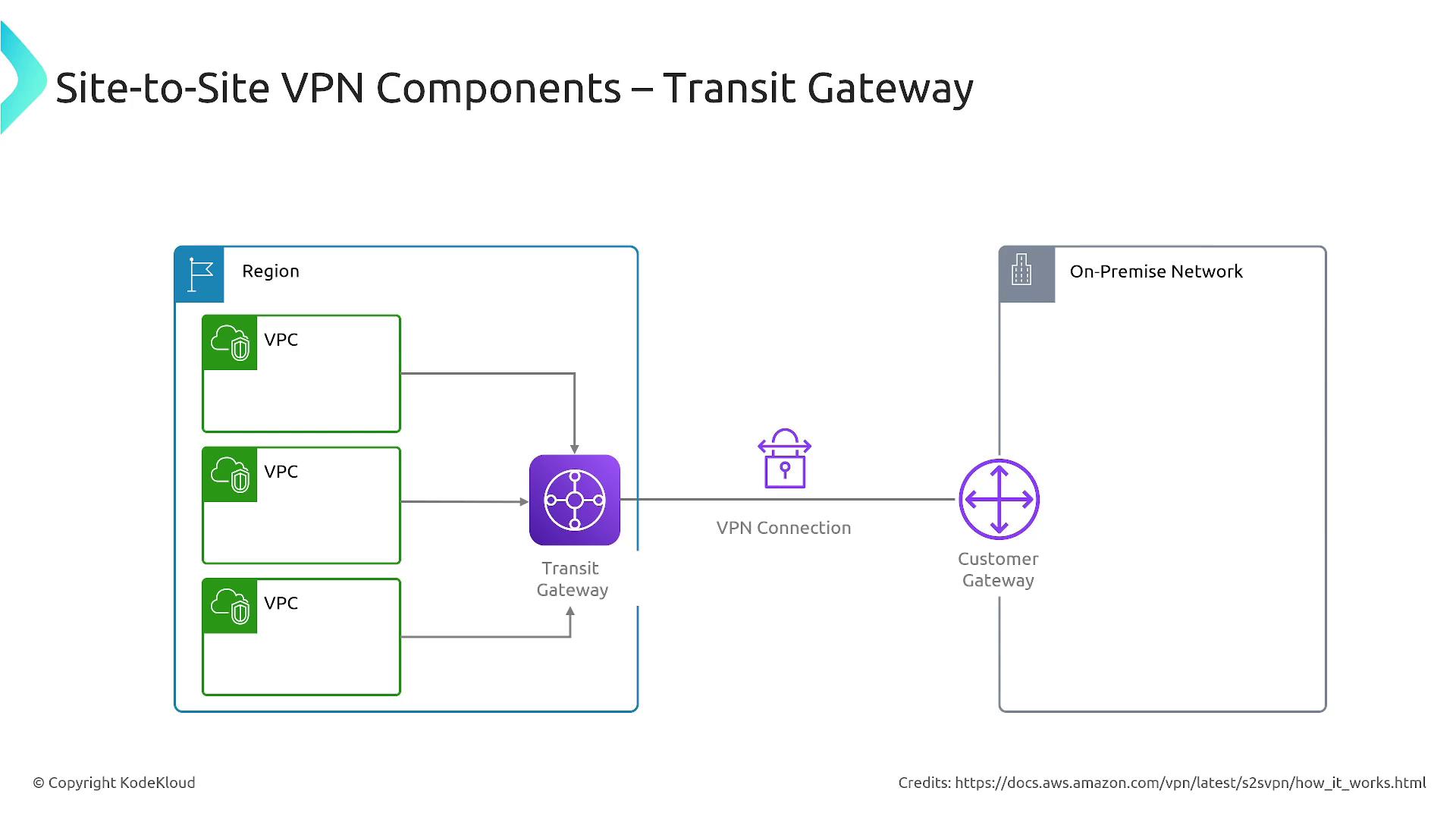
- Virtual Private Gateway (VGW) and Customer Gateway (CGW):
AWS uses a Virtual Private Gateway to establish an encrypted VPN tunnel with your on-premises customer gateway. Both physical and software-based devices can serve as customer gateways. - Routing:
Configure your VPC route tables to forward traffic between your on-premises network and AWS via the VPN connection. This routing can be managed dynamically with BGP (Border Gateway Protocol) or through static routing rules. - Transit Gateway Integration:
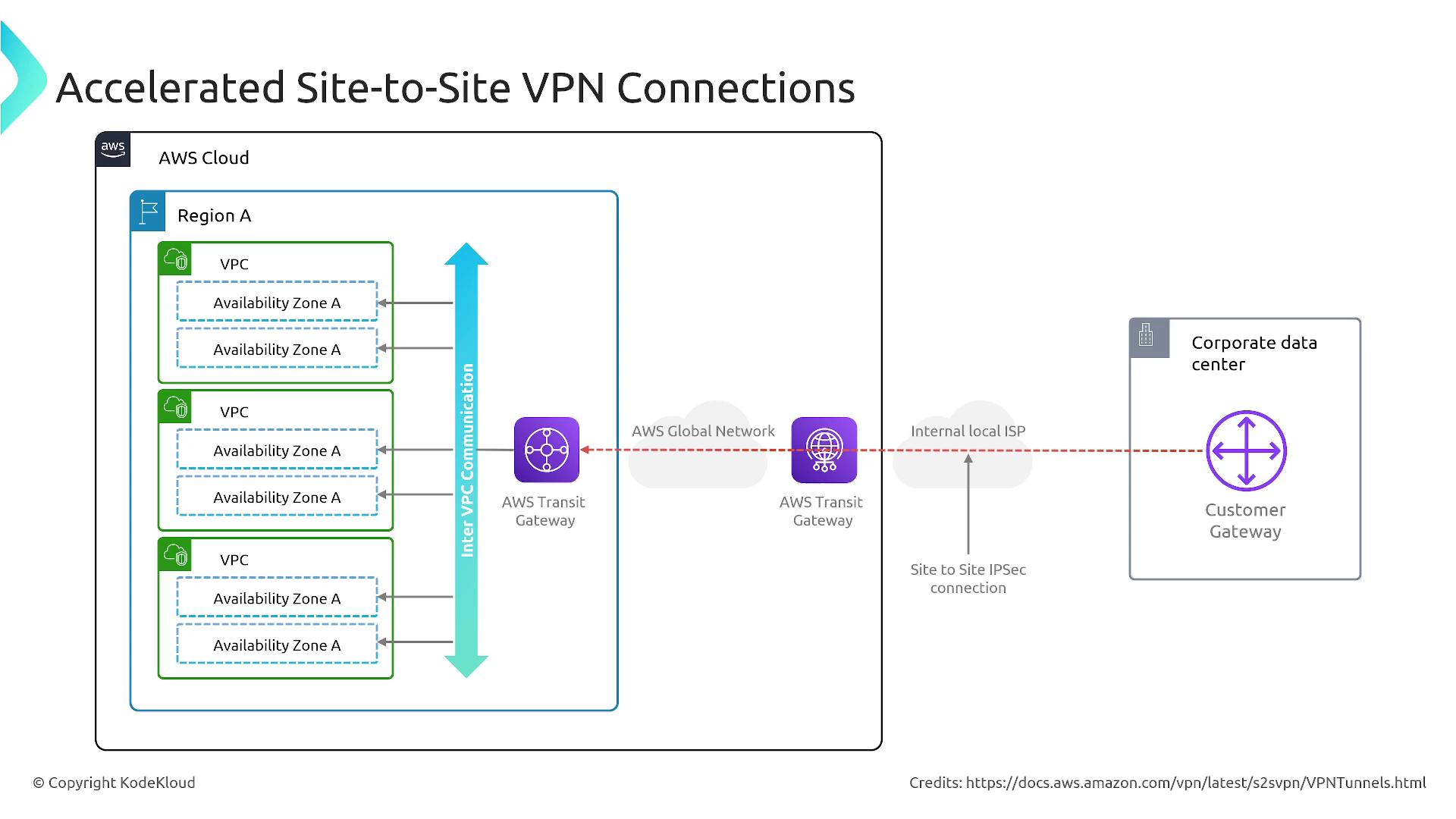
For complex scenarios involving multiple VPCs or endpoints, AWS Transit Gateway centralizes management and routing of VPN connections for efficient network communication.
A customer gateway can be a physical device or a software-based application. Ensure it is properly configured to work seamlessly with AWS for a reliable connection.
Routing Considerations
Proper routing ensures that traffic between the AWS VPC and on-premises network reaches its intended destination. For example, if your VPC uses the CIDR block 10.1.0.0/16 and your on-premises network uses 10.2.0.0/16, you must advertise these routes correctly.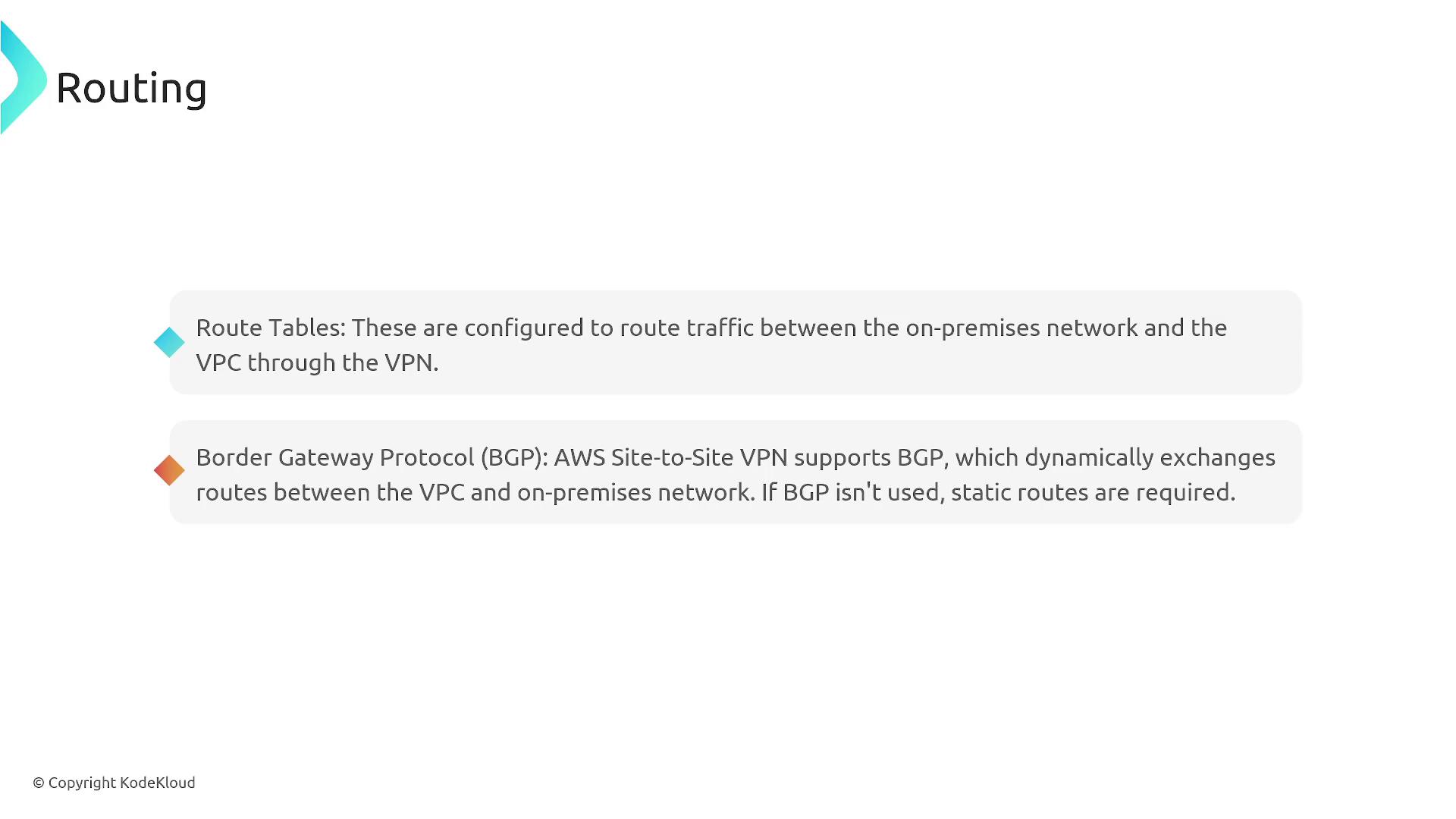
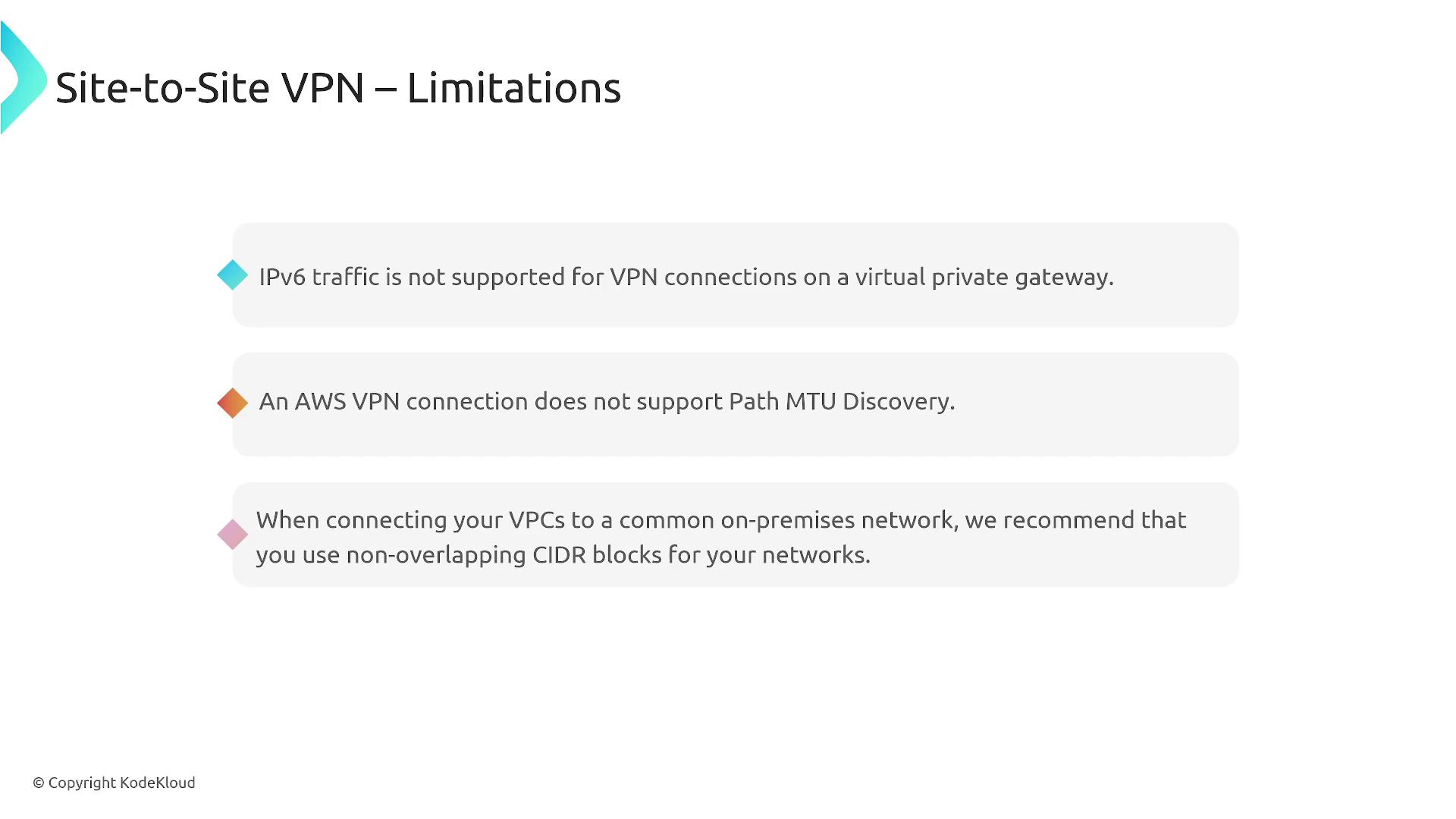
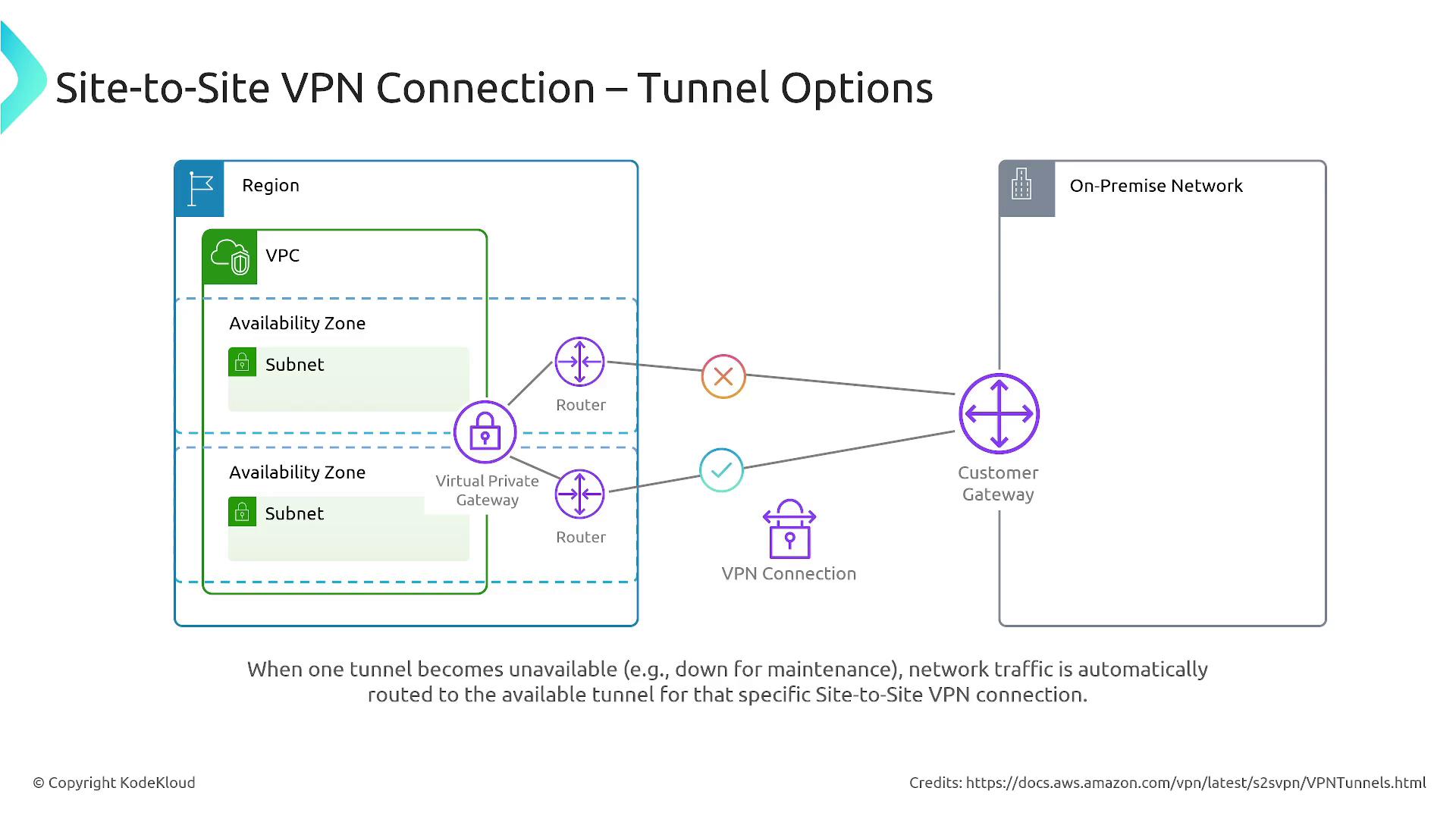
Limitations and Tunnel Redundancy
There are a few key limitations and design considerations with Site-to-Site VPN:- IPv6 traffic is not supported via the Virtual Private Gateway.
- AWS VPN connections do not support Path MTU Discovery.
- Overlapping IP ranges between your VPC and on-premises network can cause misrouted traffic.
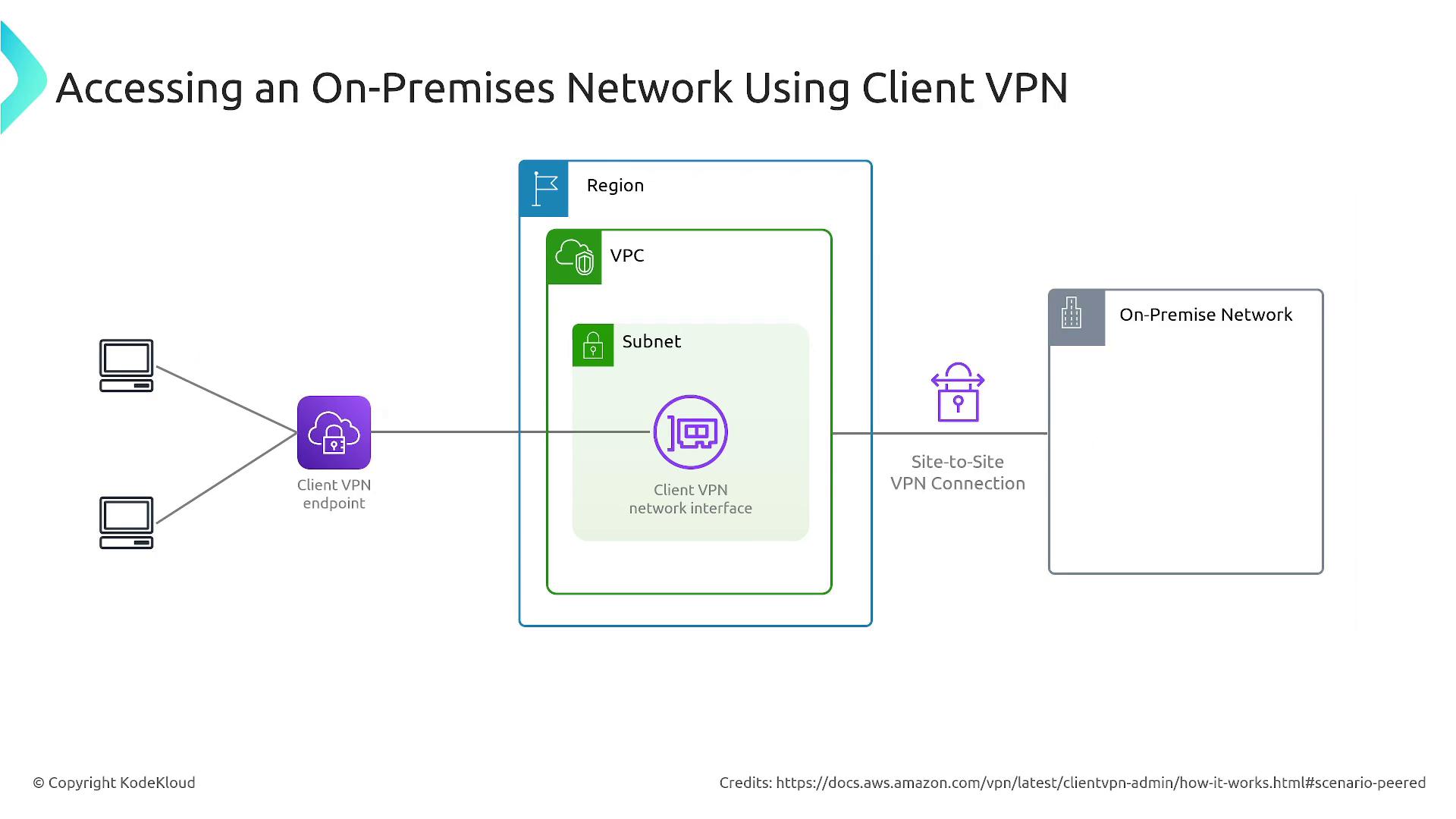
Client VPN
AWS Client VPN allows individual users to establish a secure connection from their devices to an AWS VPC or other networks interconnected via Site-to-Site VPN. This solution is ideal for remote access, ensuring that users can securely connect to backend resources.How Client VPN Works
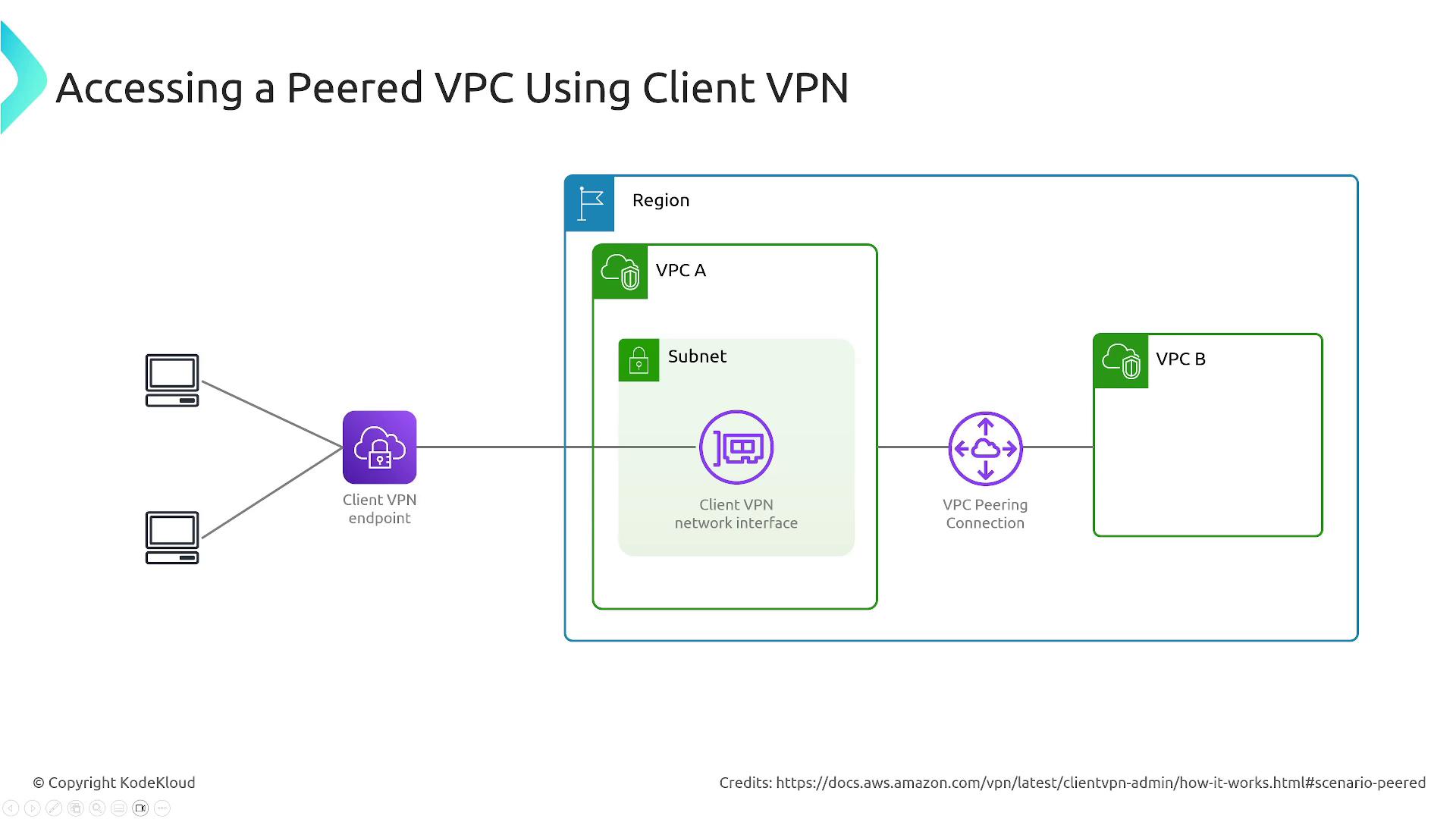
In a Client VPN setup, users connect to a managed VPN endpoint that terminates the VPN session. This endpoint is linked to a specific subnet that routes traffic to target resources. The service supports OpenVPN-based clients and leverages AWS-managed infrastructure to provide a scalable and secure connection.
Key Features
- Multiple authentication methods including Active Directory, SAML-based federated authentication, certificate-based authentication, and single sign-on.
- Support for both TCP and UDP protocols on ports 443 (default for SSL/TLS) and 1194.
- Each client receives a unique IP address from a predetermined, non-overlapping client CIDR range.
- Centralized management of sessions with integration into AWS routing mechanisms, using choices like Transit Gateway or VPC peering for complex scenarios.
Client VPN Configuration Considerations
When configuring a Client VPN endpoint, keep these important rules in mind:| Configuration Parameter | Requirement / Limitation |
|---|---|
| Bandwidth per User | Minimum 10 Mbps per connection |
| CIDR Block Overlap | Client VPN, VPC, and on-premises CIDRs must be non-overlapping |
| Client CIDR Block | Defined during endpoint creation and immutable; ranges from /22 to /12 |
| Subnet Association | All associated subnets must be in the same VPC; only one per availability zone |
