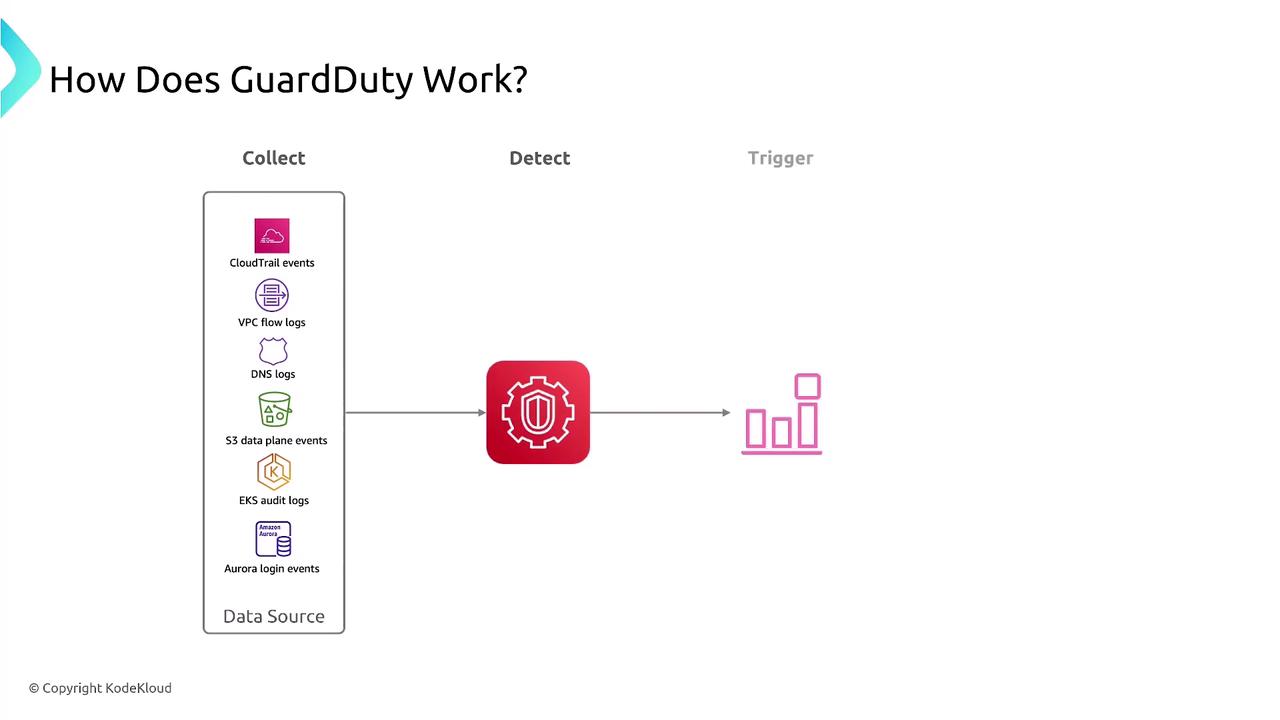
- High Severity: Indicates a compromised resource that demands immediate remediation.
- Medium Severity: Signals suspicious activity warranting investigation to verify its legitimacy.
- Low Severity: Suggests minor issues such as port scans or failed login attempts that could be indicative of broader malicious behavior.
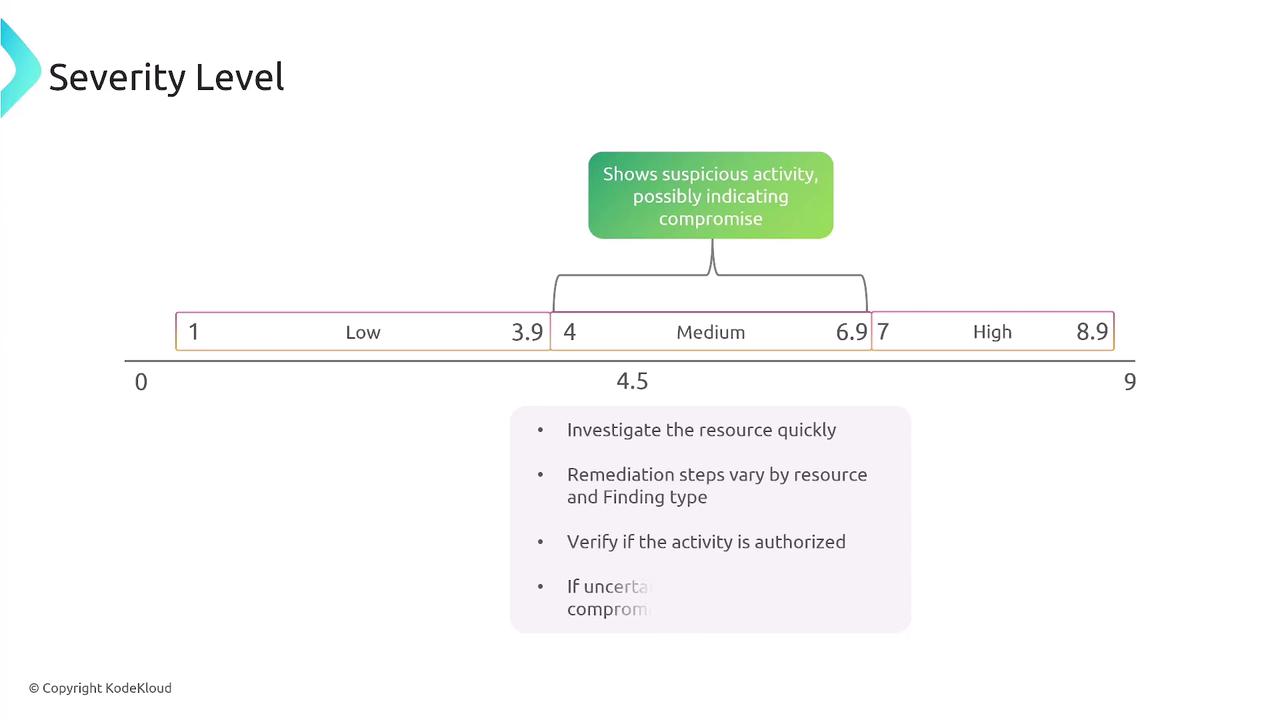
GuardDuty supports the use of both trusted and threat IP lists. Trusted IP lists include IP addresses known to be safe (e.g., used for security scanning), while threat IP lists contain addresses associated with malicious activity. GuardDuty ignores entries on the trusted list but flags those on the threat list as dangerous. Note that these lists can include up to 250,000 CIDR ranges or individual IP addresses.
- Reconnaissance: Unusual port scanning or unauthorized port probing.
- Instance Compromise: Activities such as using instances for cryptocurrency mining, deploying malware, or launching denial-of-service attacks.
- Account Compromise: Suspicious API calls, attempts to disable logging, modifications to password policies, or unexpected resource deployments.
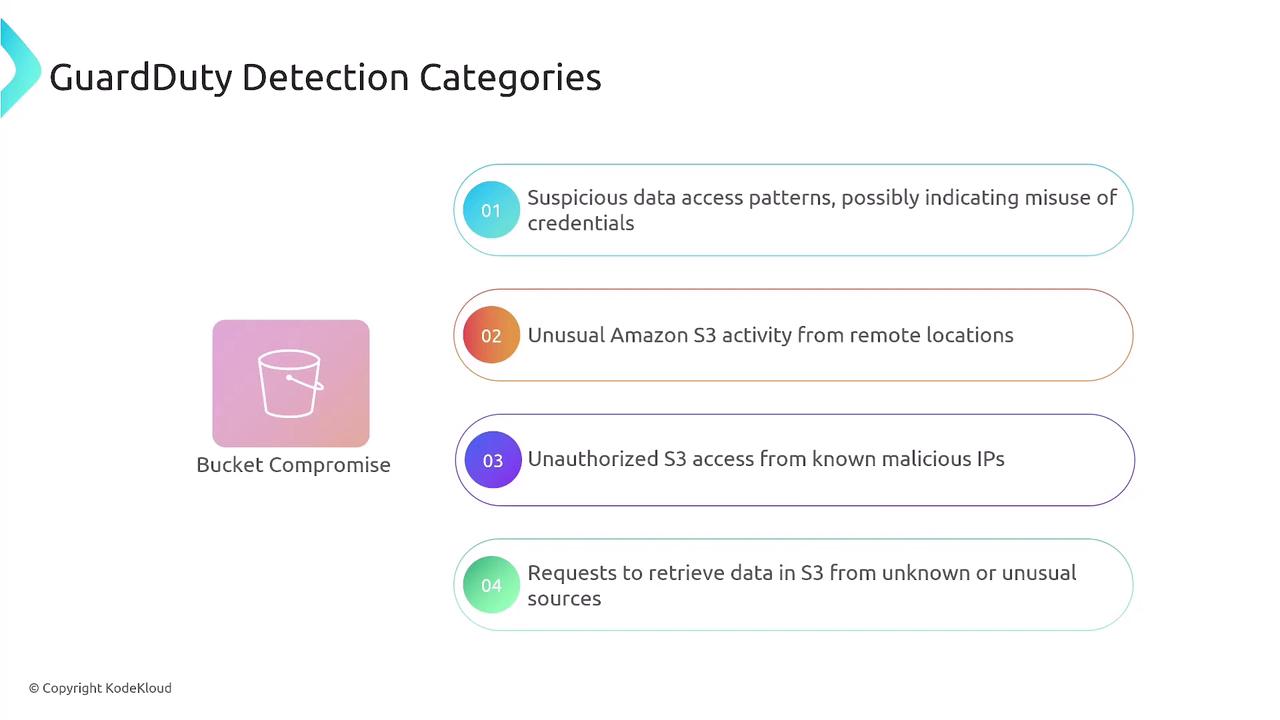
- Bucket Compromise: Unusual activities linked to Amazon S3 operations.

In summary, AWS GuardDuty serves as a vigilant guardian for your AWS infrastructure, continuously monitoring network traffic and control plane activities to promptly detect potential intrusions or threats. This proactive approach is pivotal in protecting your cloud resources against evolving security challenges.