Why Do We Need Encryption?
Encryption is vital for protecting data from breaches, man-in-the-middle attacks, and unauthorized access. By encrypting sensitive information, even if data is compromised, it remains unreadable to malicious actors. This layered defense makes unauthorized decryption practically impossible.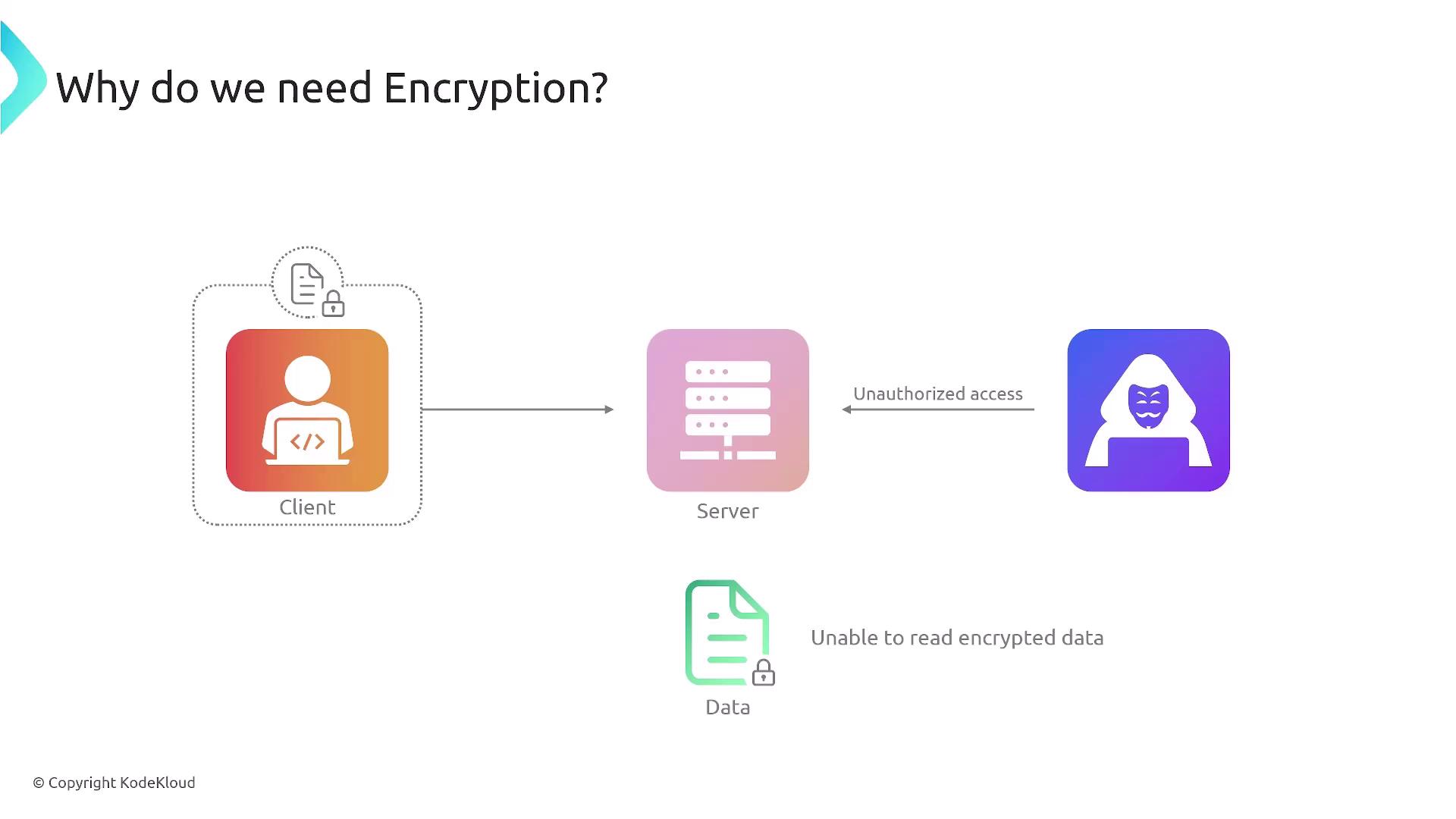
Key Metadata and Integration
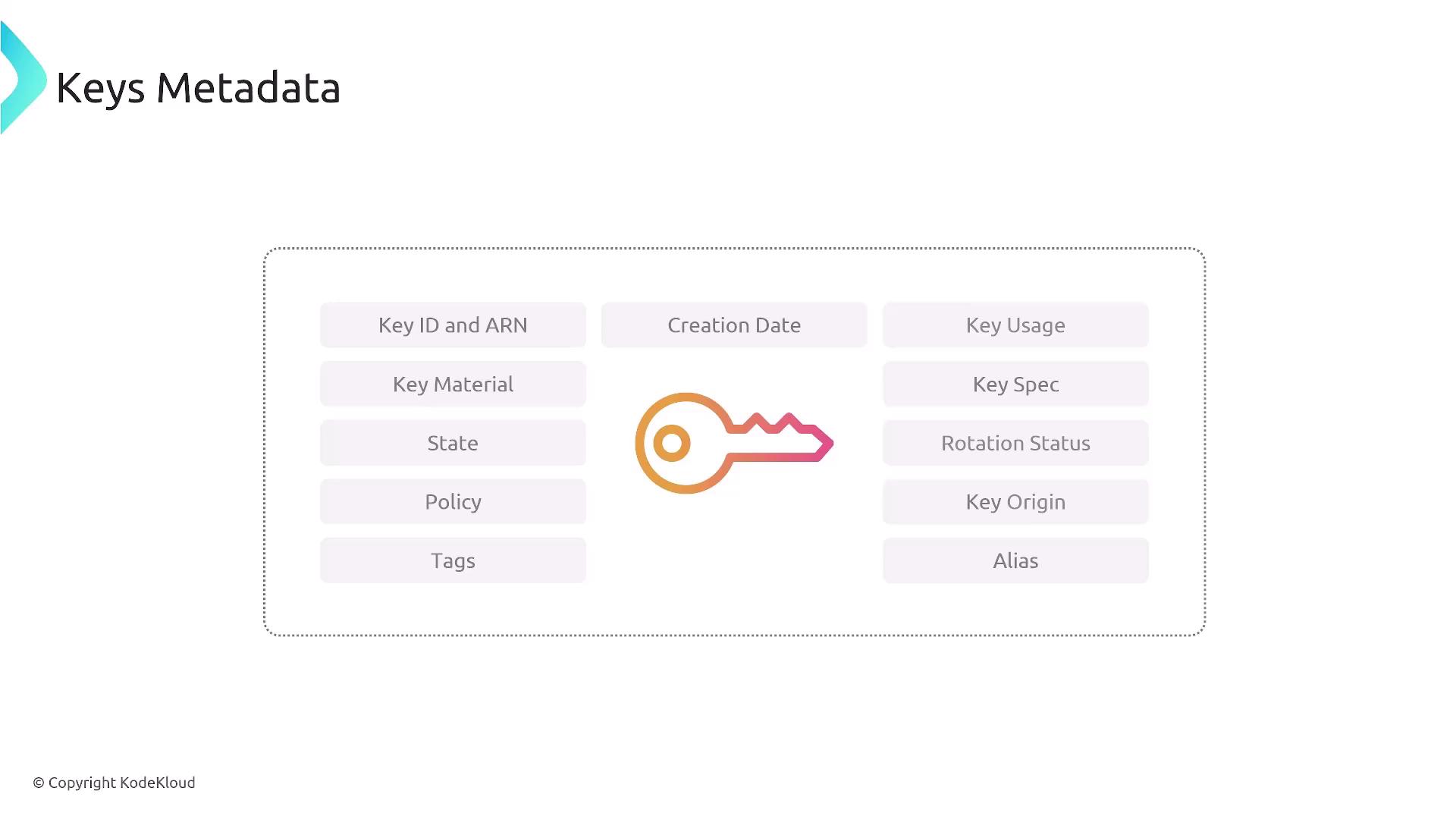
Each key managed by KMS includes crucial metadata such as:- Key ID and Amazon Resource Name (ARN)
- Cryptographic material (key material)
- State indicators (enabled, disabled, scheduled for deletion, etc.)
- Permissions similar to IAM roles
- Tags, creation date, key usage, key specifications, and rotation status
While memorizing these metadata details is not necessary, understanding them is important for secure key management at the SysOps level.
Types of Keys in KMS
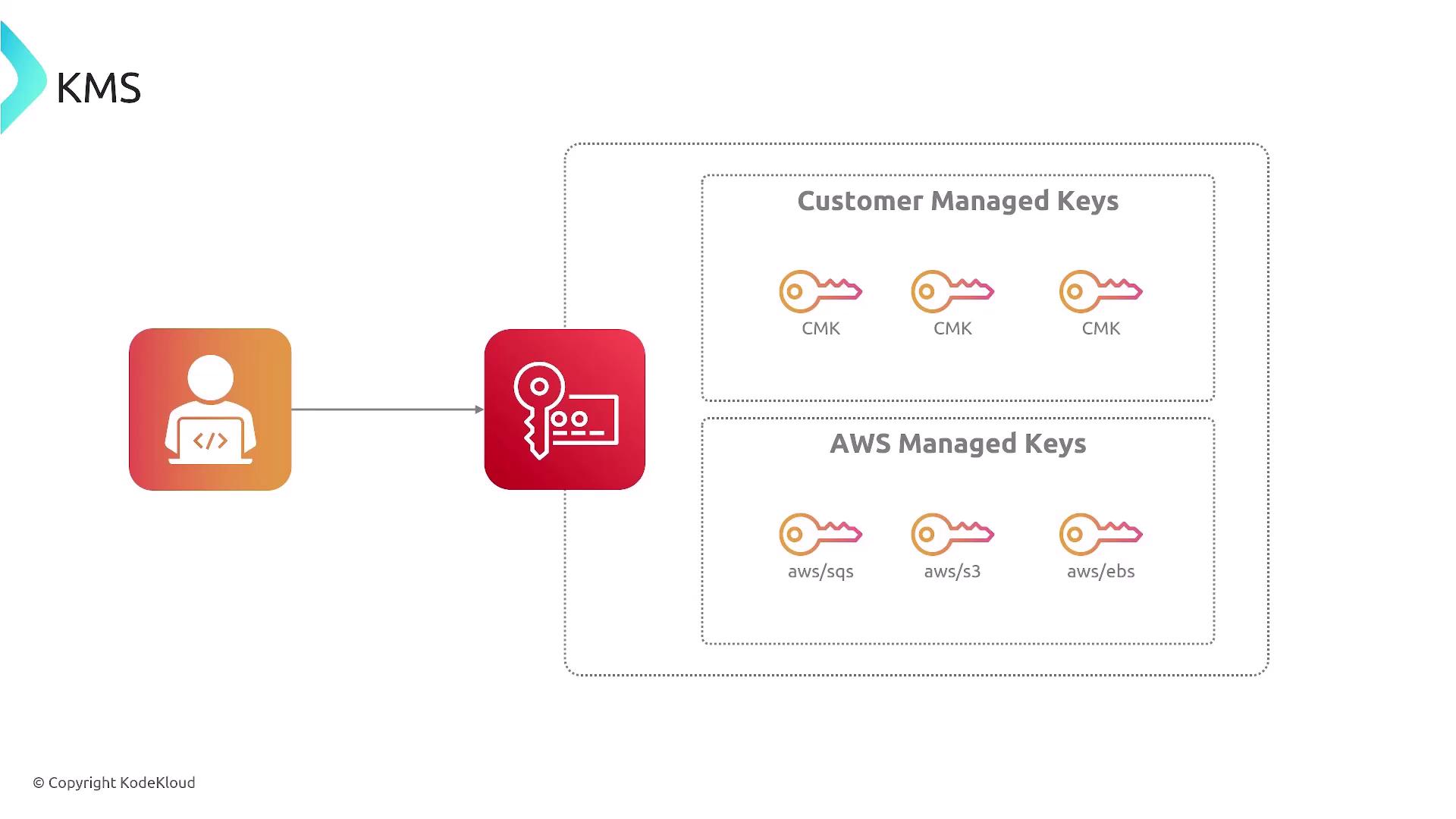
KMS supports multiple key types designed for various encryption needs:-
Customer Managed Keys (CMKs):
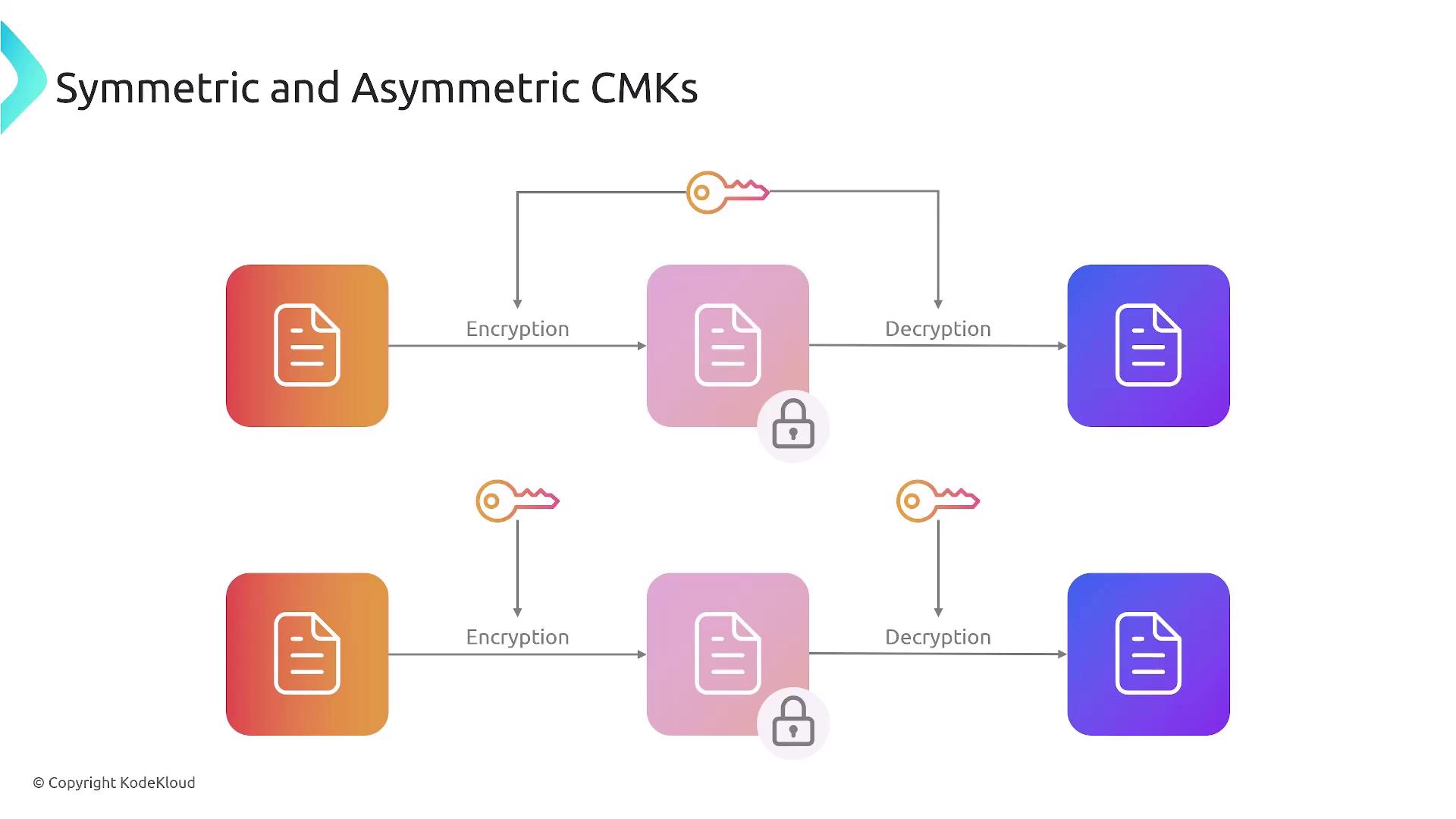
CMKs offer full flexibility and control. You can create, rotate, delete, and set permissions for these keys. They are available in both symmetric and asymmetric variants:- Symmetric keys: Use a single key for both encryption and decryption.
- Asymmetric keys: Use a public-private key pair; the public key is used for signature verification while the private key handles decryption and signing.
-
Data Keys:
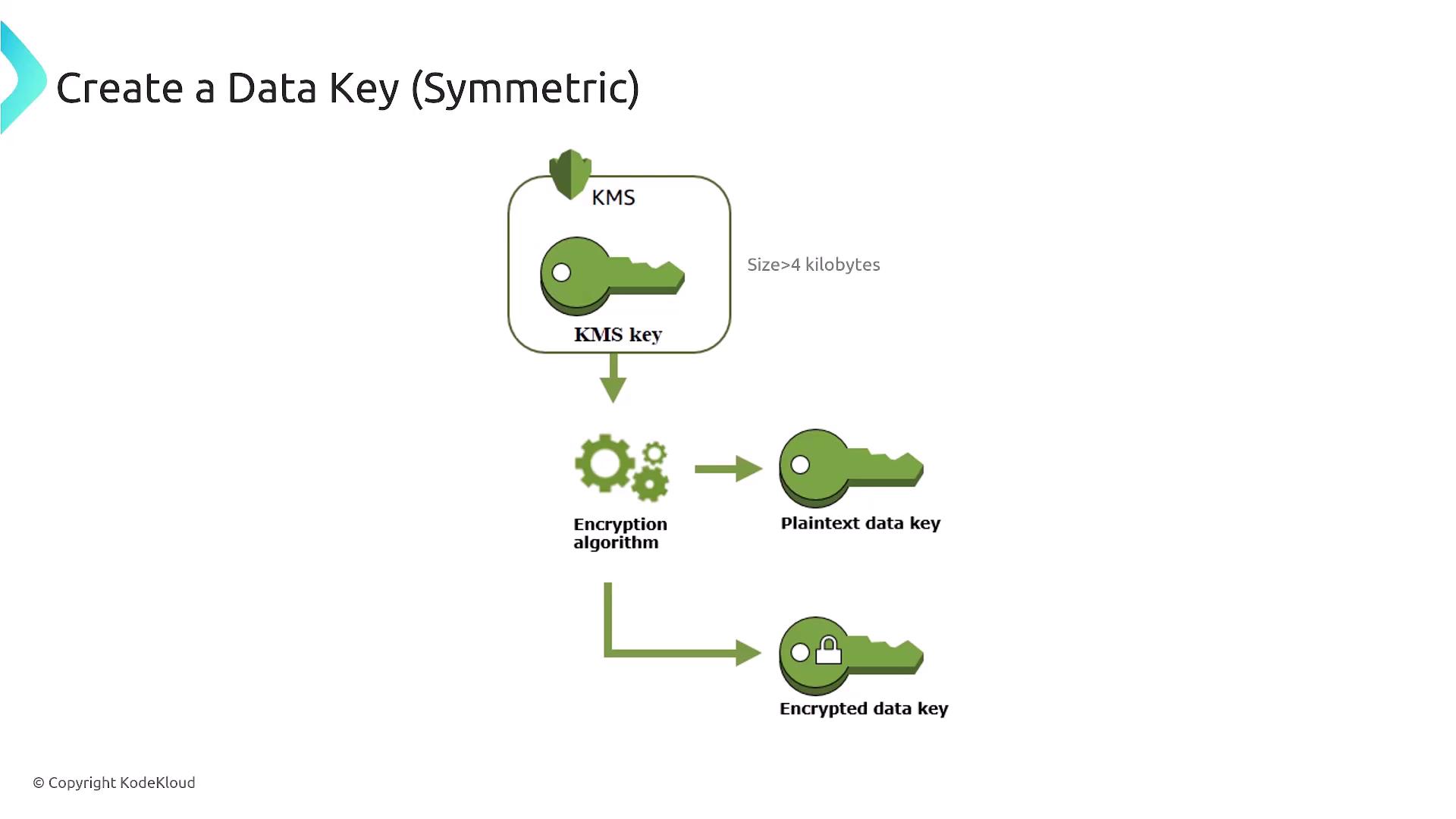
Data keys are used to encrypt and decrypt large volumes of data. Typically, a data key is generated and then protected (encrypted) by a CMK through envelope encryption. In this method, your data is secured with a data key, which is itself encrypted by a CMK, ensuring that even if stored alongside the encrypted data, the data key is protected.
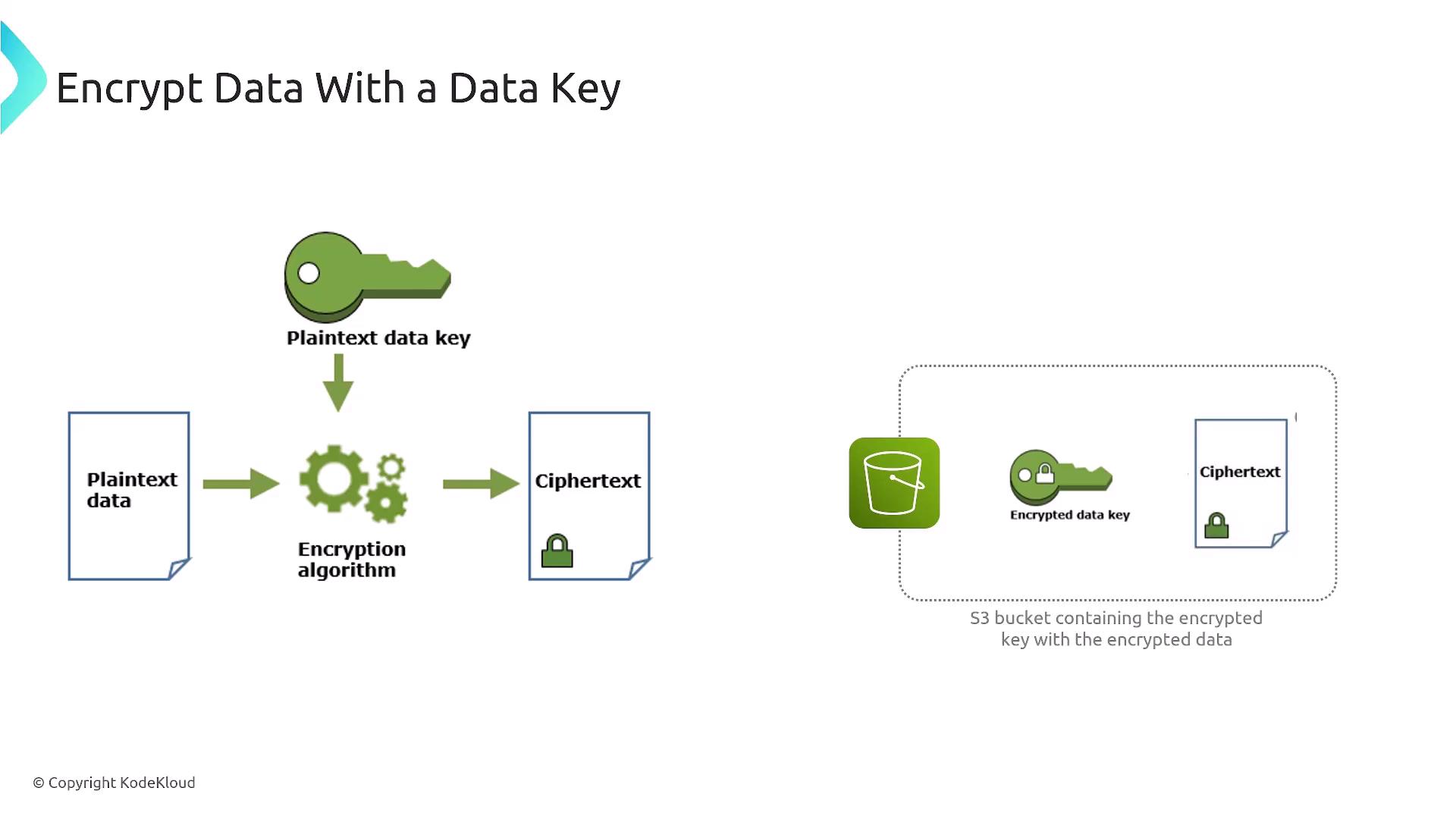
Envelope Encryption Process
Envelope encryption involves generating both a plaintext data key and an encrypted data key. The process is as follows:- The CMK encrypts the plaintext data key.
- The plaintext data key is used to encrypt your data.
- The encrypted data key is stored alongside the encrypted data.
- To decrypt the data, the encrypted data key is first decrypted using the CMK, and then the plaintext data key decrypts the data.
Software KMS Features
The software-based KMS service offers the following features:- Centralized key management
- Tight integration with AWS services
- Customer-controlled key management, including scheduled and automated key rotations
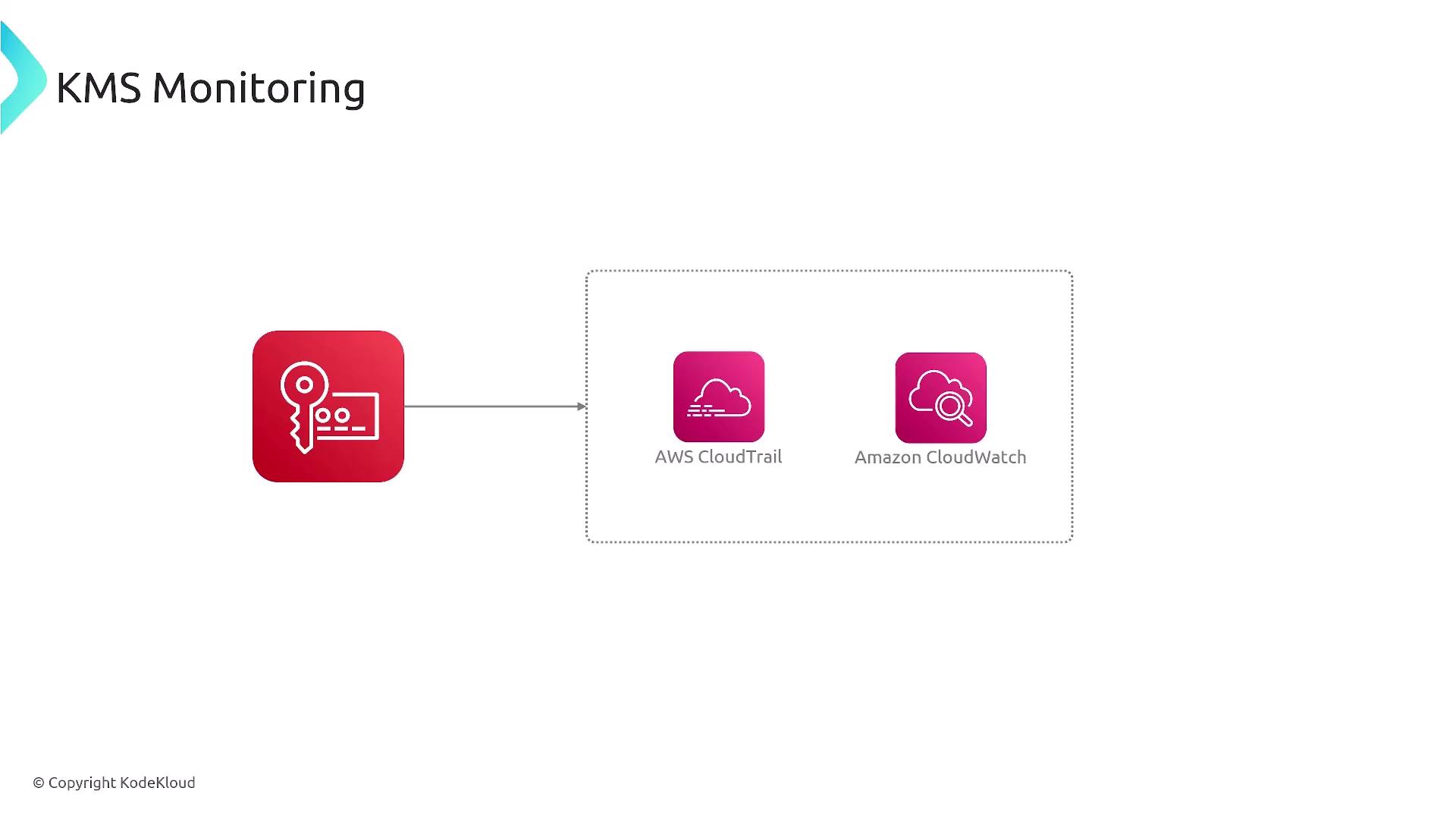
- Detailed audit and compliance capabilities through integration with CloudTrail and CloudWatch

Please note that the software version of KMS is not FIPS 140 compliant. For environments requiring stricter compliance, consider using the hardware alternative.
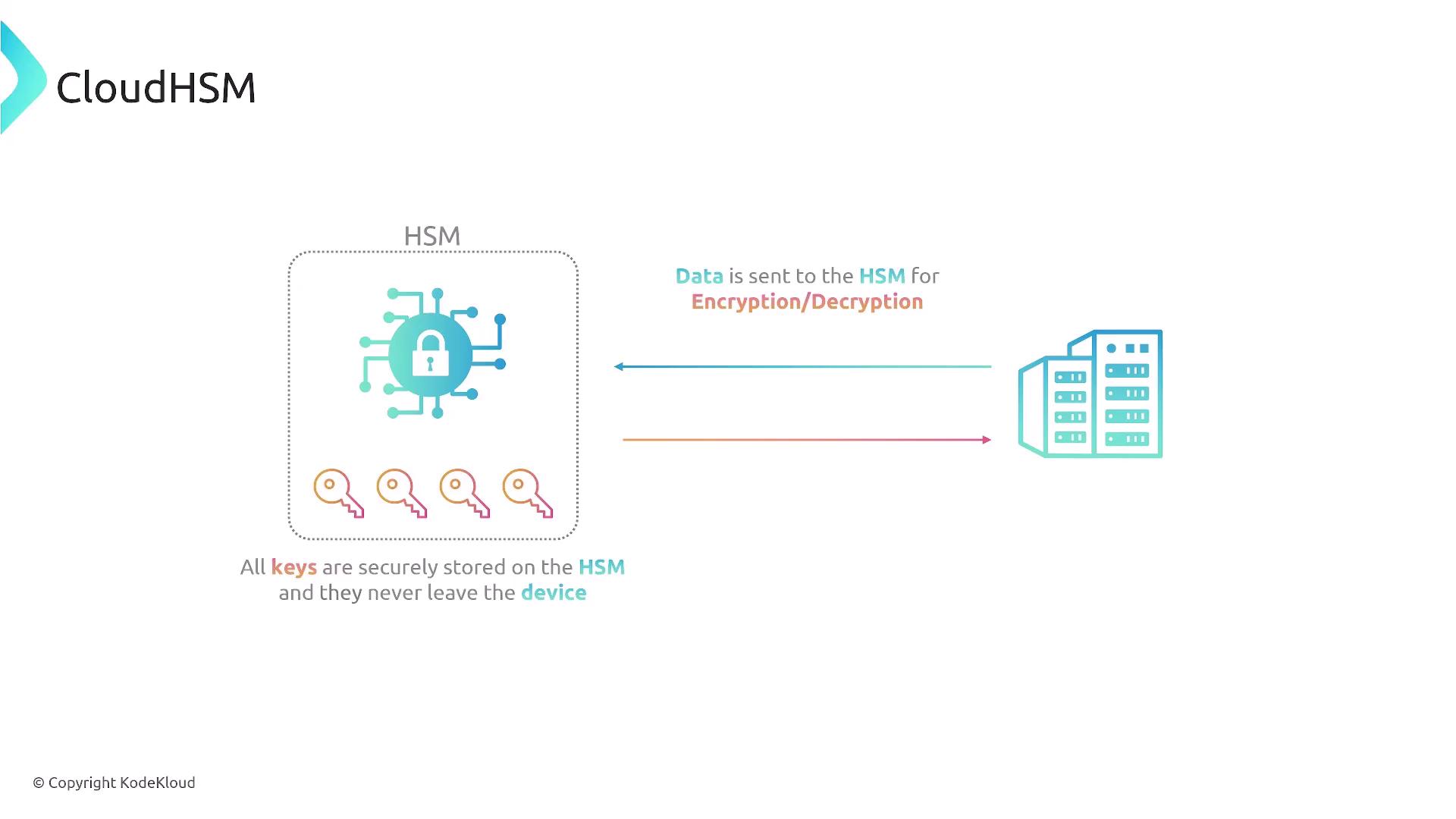
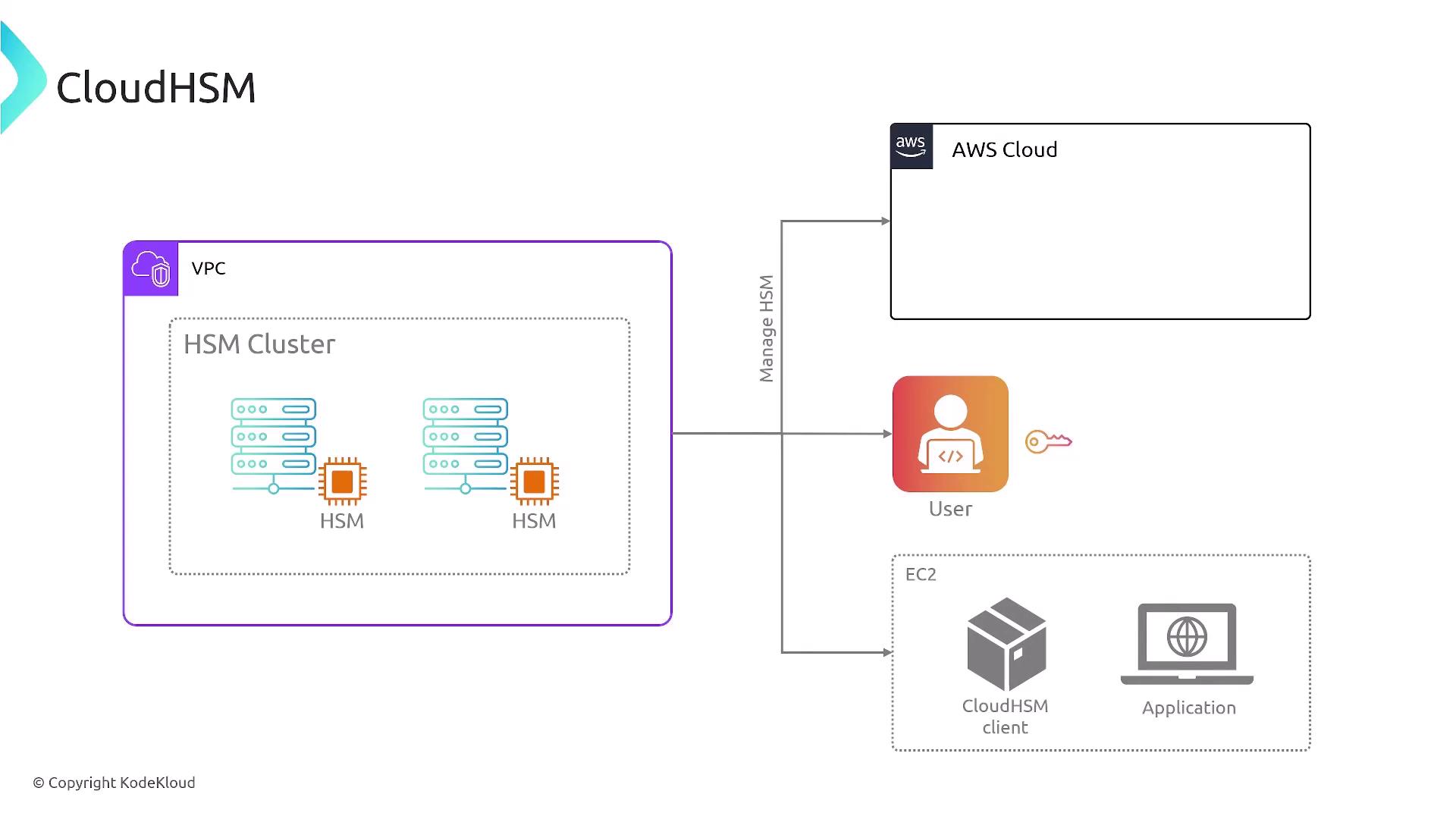
CloudHSM: The Hardware Version of KMS
For environments that must adhere to stringent security standards, such as FIPS 140-2, AWS provides CloudHSM—a hardware-based version of KMS. CloudHSM leverages dedicated hardware security modules (HSMs) for heightened cryptographic security. While offering similar core functionalities as KMS, CloudHSM ensures that cryptographic keys remain within secure, dedicated hardware. Key characteristics of CloudHSM include:- Key operations executed on dedicated hardware modules.
- Clustering of multiple HSMs for high availability and load balancing.
- Keys never leave the HSM cluster, preserving maximum security.
- Seamless integration with AWS services, while customers maintain complete control over their keys.
Summary
AWS provides two primary solutions for key management:- Software-based KMS: Delivers centralized management, flexibility, and seamless integration with AWS services.
- CloudHSM (Hardware KMS): Meets high compliance and security requirements by using dedicated HSMs to protect cryptographic keys.