Key Validation Points Across the DevOps Lifecycle
At every phase of the DevOps lifecycle, targeted validation steps provide rapid feedback. Early detection through IDE plugins or CI scans prevents defects from propagating downstream.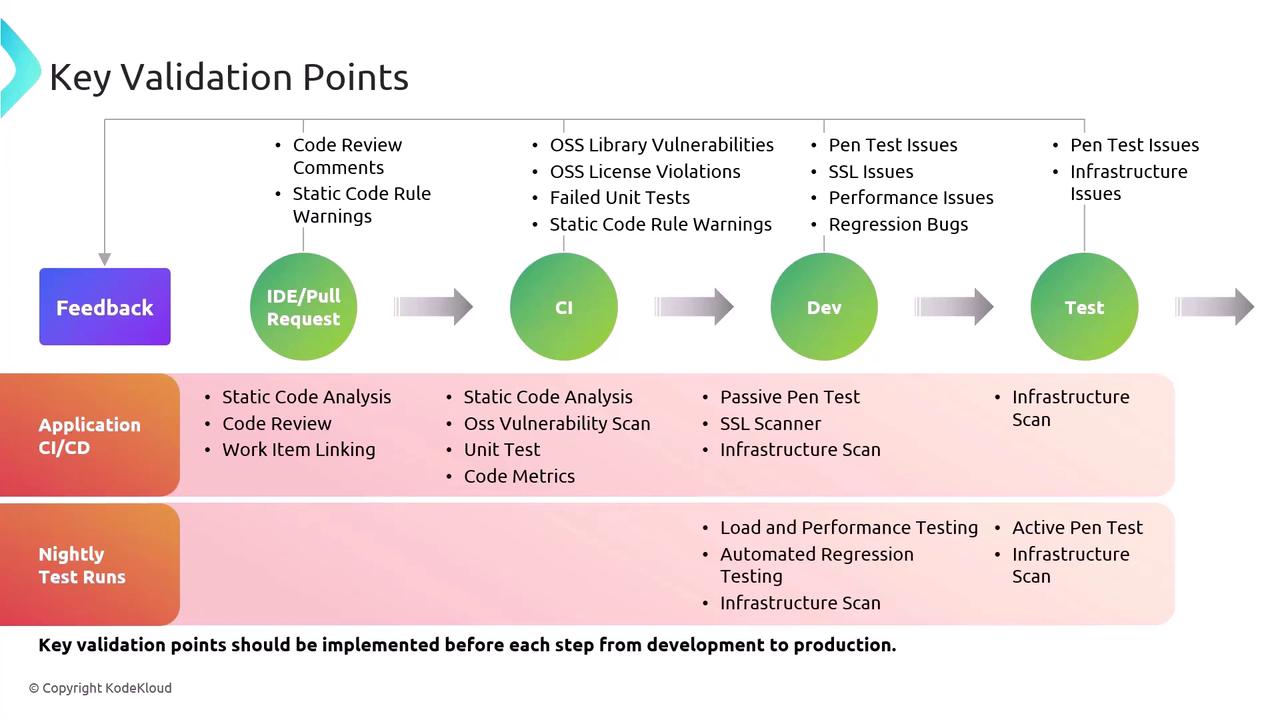
| Stage | Validation Checks | Examples |
|---|---|---|
| IDE & Pull Requests | Static analysis, peer code review | ESLint, SonarQube, GitHub/GitLab merge requests |
| Continuous Integration | Automated builds, unit & integration tests | Jenkins, Azure Pipelines, GitLab CI |
| Development Phase | Security scans, performance testing | OWASP ZAP, SonarCloud, JMeter |
| Testing Stage | Penetration testing, infrastructure validation | Metasploit, Terraform validate, Chef InSpec |
Shifting validation left means catching issues in IDEs or CI—before they reach QA or production.
The True Cost of Defects at Each Stage
Defect remediation cost escalates dramatically the later you catch it. Below are industry averages: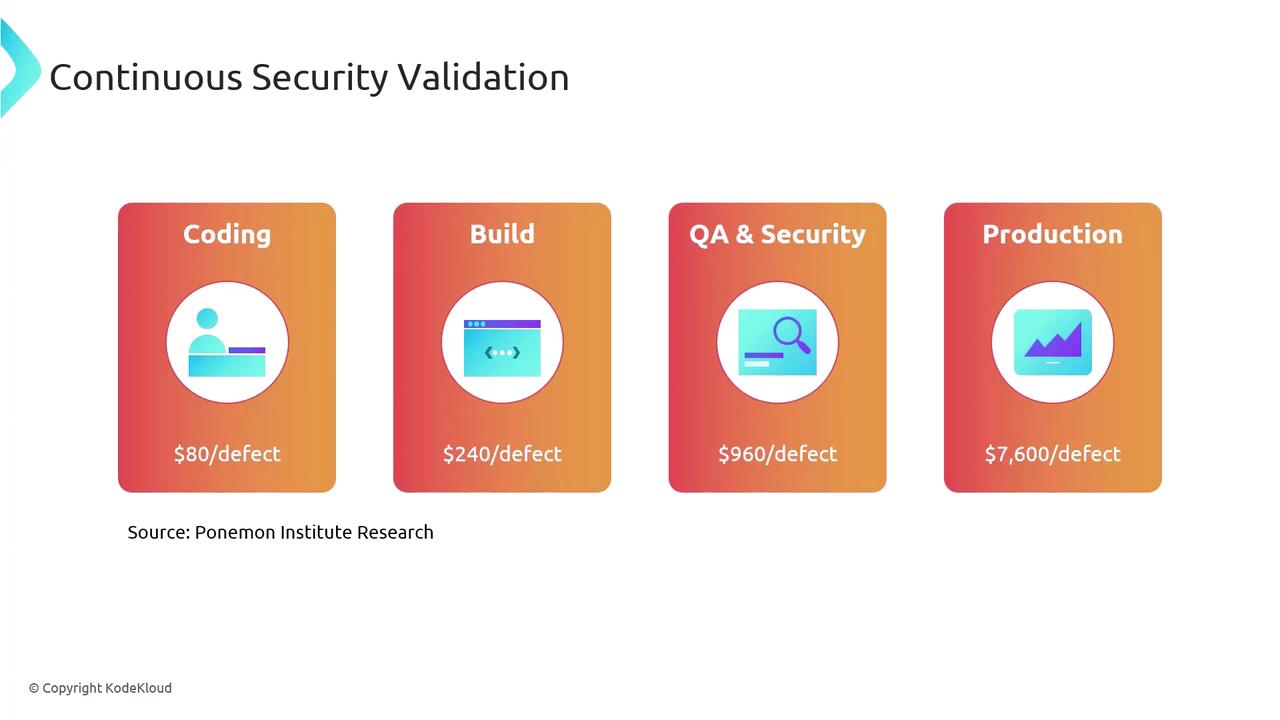
| Phase | Average Cost per Defect |
|---|---|
| Coding | $80 |
| Build | $240 |
| QA & Security | $960 |
| Production | $7,600 |
Fixing a bug during development can cost up to 90% less than patching it in production.
Shifting Security Left
Embedding security early in your DevOps pipeline empowers developers to remediate vulnerabilities before they become critical.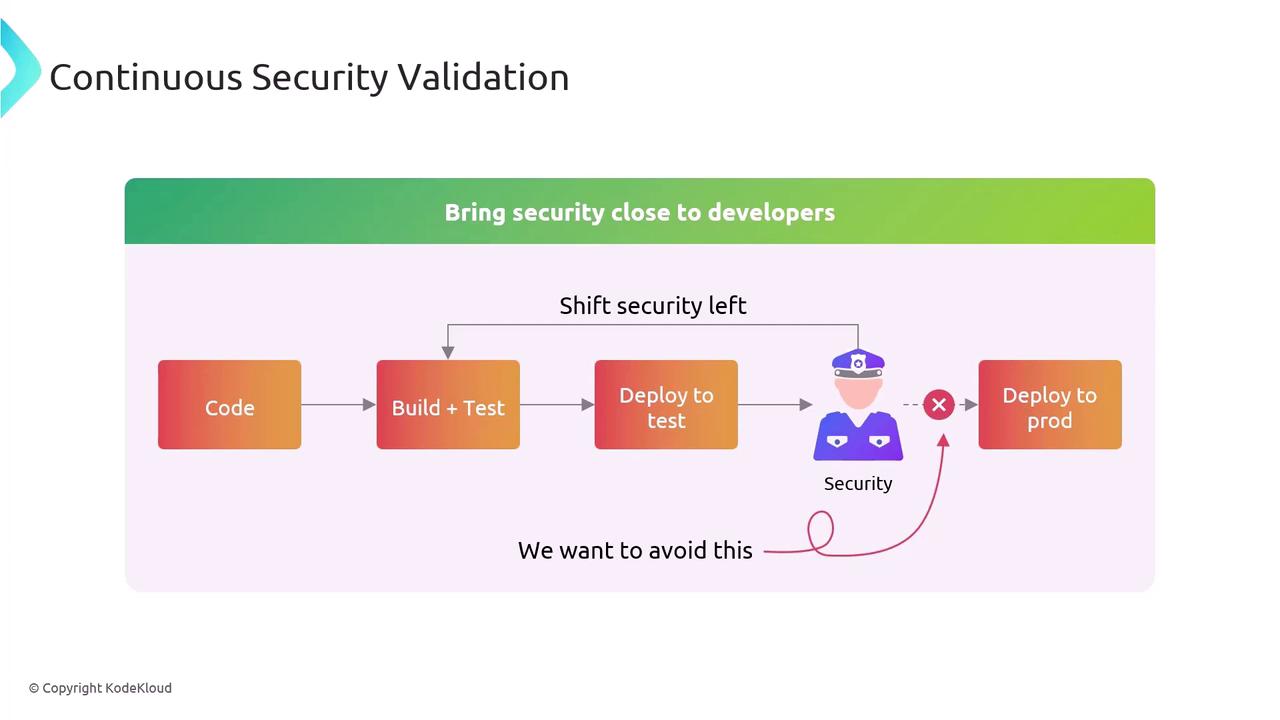
- Early detection of vulnerabilities in code and dependencies
- Faster, automated remediation workflows
- Significant cost savings per defect
Delaying security tests until the end of the pipeline can lead to critical vulnerabilities slipping into production.
Continuous Security Validation and Automation
Automating security checks at every commit, build, and release ensures that security keeps pace with rapid deployments.
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
- Software Composition Analysis (SCA)
- Runtime Application Self-Protection (RASP)
Combine multiple tools in your CI/CD pipeline to cover code flaws, third-party risks, and runtime threats.