- GitHub Apps
- GITHUB_TOKEN
- Personal Access Tokens (PATs)
1. GitHub Apps
GitHub Apps act on behalf of your application—independent from user credentials. They can be installed on organizations or user accounts to interact with repositories, respond to events, and automate tasks like code reviews, CI/CD, and issue management.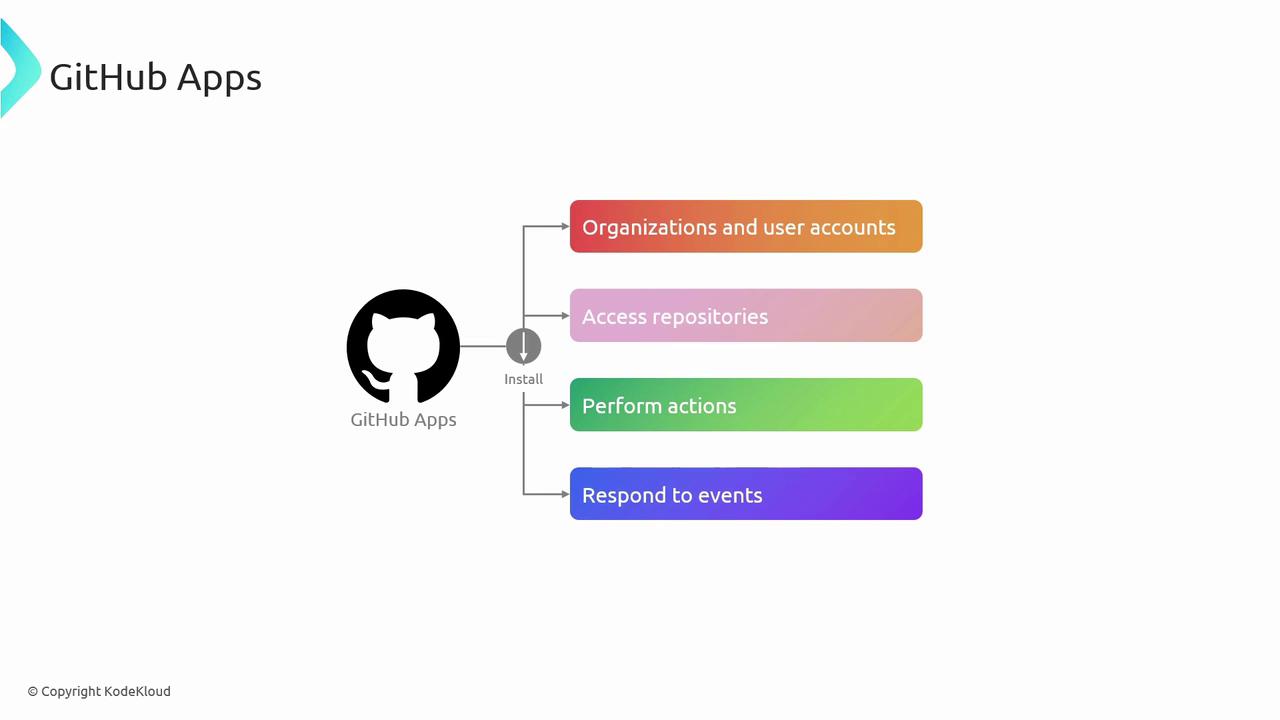
Benefits
- Fine-grained permissions scoped to required actions
- Enhanced security by separating app identity from user credentials
- Detailed audit logs and install-based access control
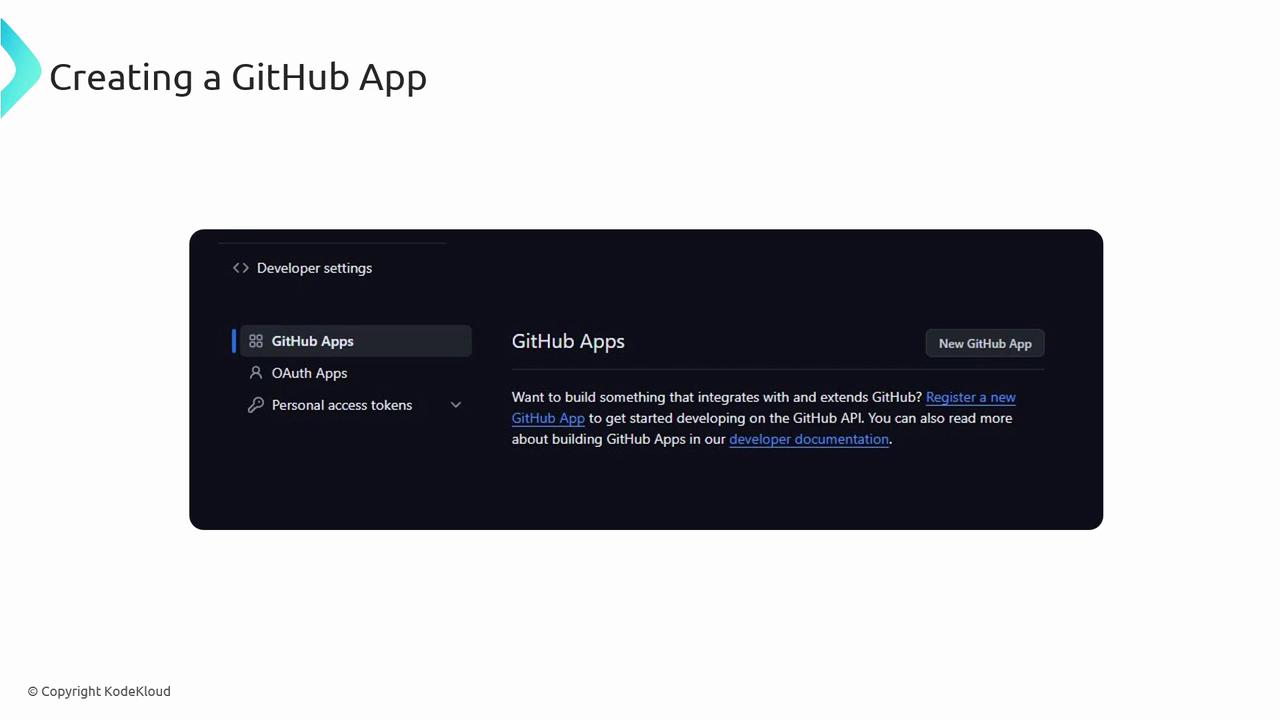
Creating a GitHub App
- Navigate to GitHub Settings → Developer Settings.
- Select GitHub Apps and click New GitHub App.
- Provide the App name, homepage URL, and callback URL.
- Configure the required permissions and subscribe to relevant events.
- Save and download the private key for authentication.
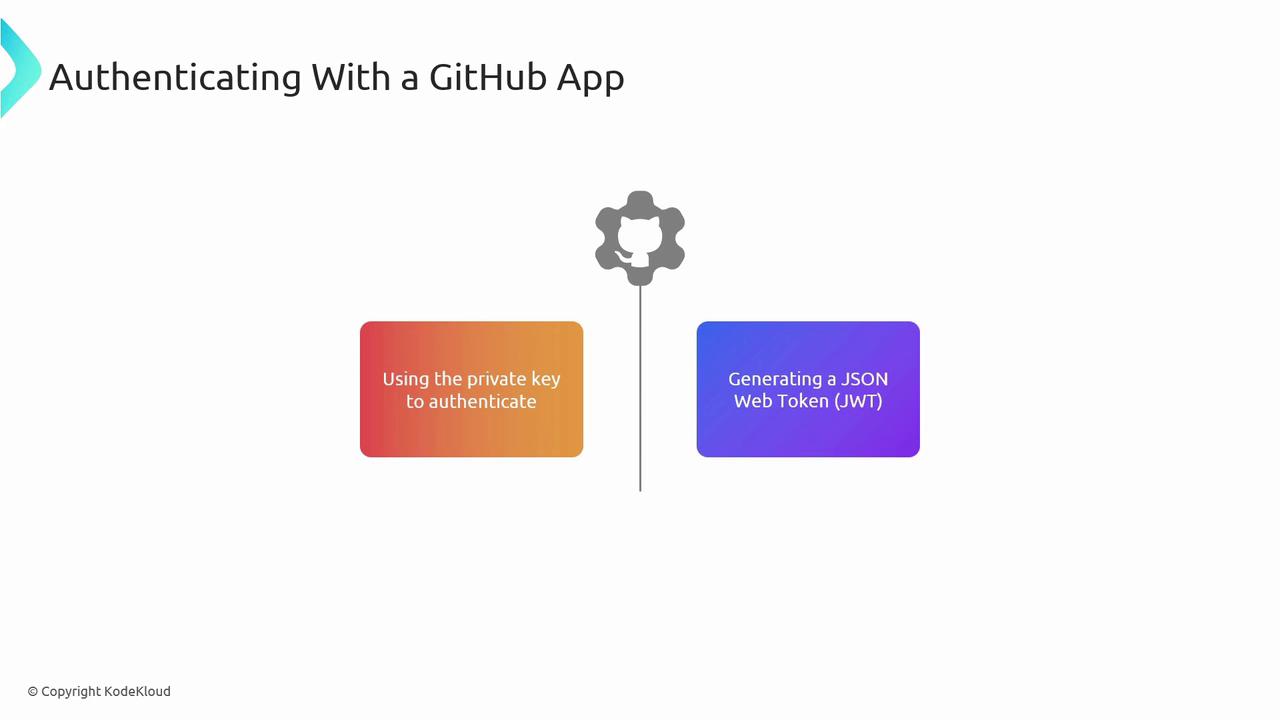
Authenticating with a GitHub App
Authentication is a two-step process:- Generate a JSON Web Token (JWT) using your App’s private key.
- Exchange the JWT for an installation access token via GitHub’s API.
APP_ID and PRIVATE_KEY).
jwt_token to request an installation access token:
After updating permissions, you must regenerate the installation access token for changes to take effect.
Managing Permissions
Regularly audit your App’s permissions in Settings. Use the App’s dashboard or API to adjust scopes and monitor usage.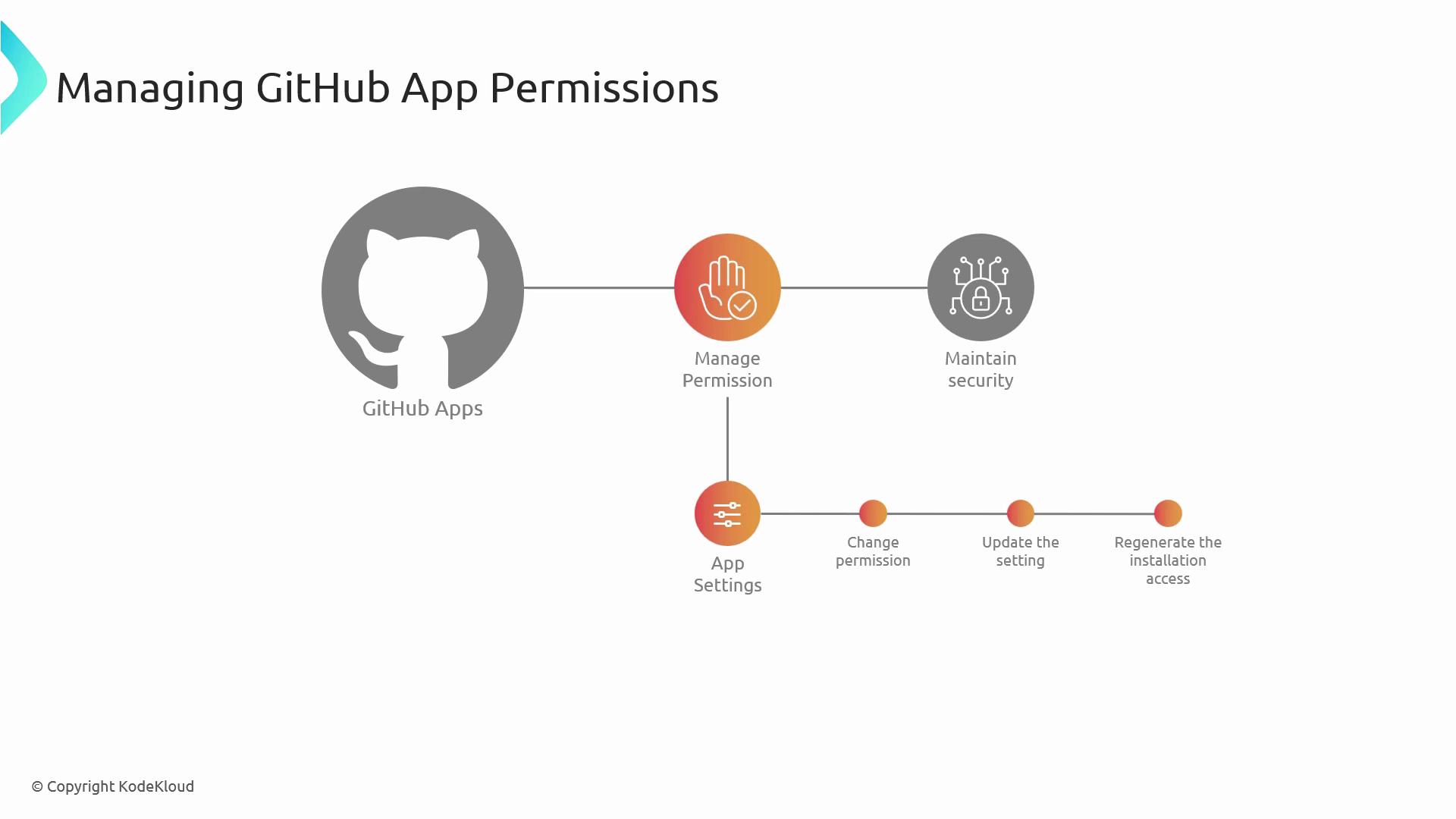
2. GITHUB_TOKEN
GITHUB_TOKEN is an automatically generated secret available in GitHub Actions workflows. It provides repository-scoped authentication for checkout, API calls, and publishing packages—without manual secret management.
Benefits
- Auto-generated for every workflow run
- Limited to current repository to minimize blast radius
- No manual rotation or storage needed

Usage Example
UseGITHUB_TOKEN from the secrets context:
Do not expose
GITHUB_TOKEN to external URLs or untrusted actions—limit usage to internal steps only.3. Personal Access Tokens (PATs)
Personal Access Tokens (PATs) provide user-level authentication for GitHub APIs and Git operations. You can choose classic or fine-grained tokens to control scope and expiration.
Use Cases
- CLI or script-based Git operations
- REST or GraphQL API integrations
- Third-party service authentication
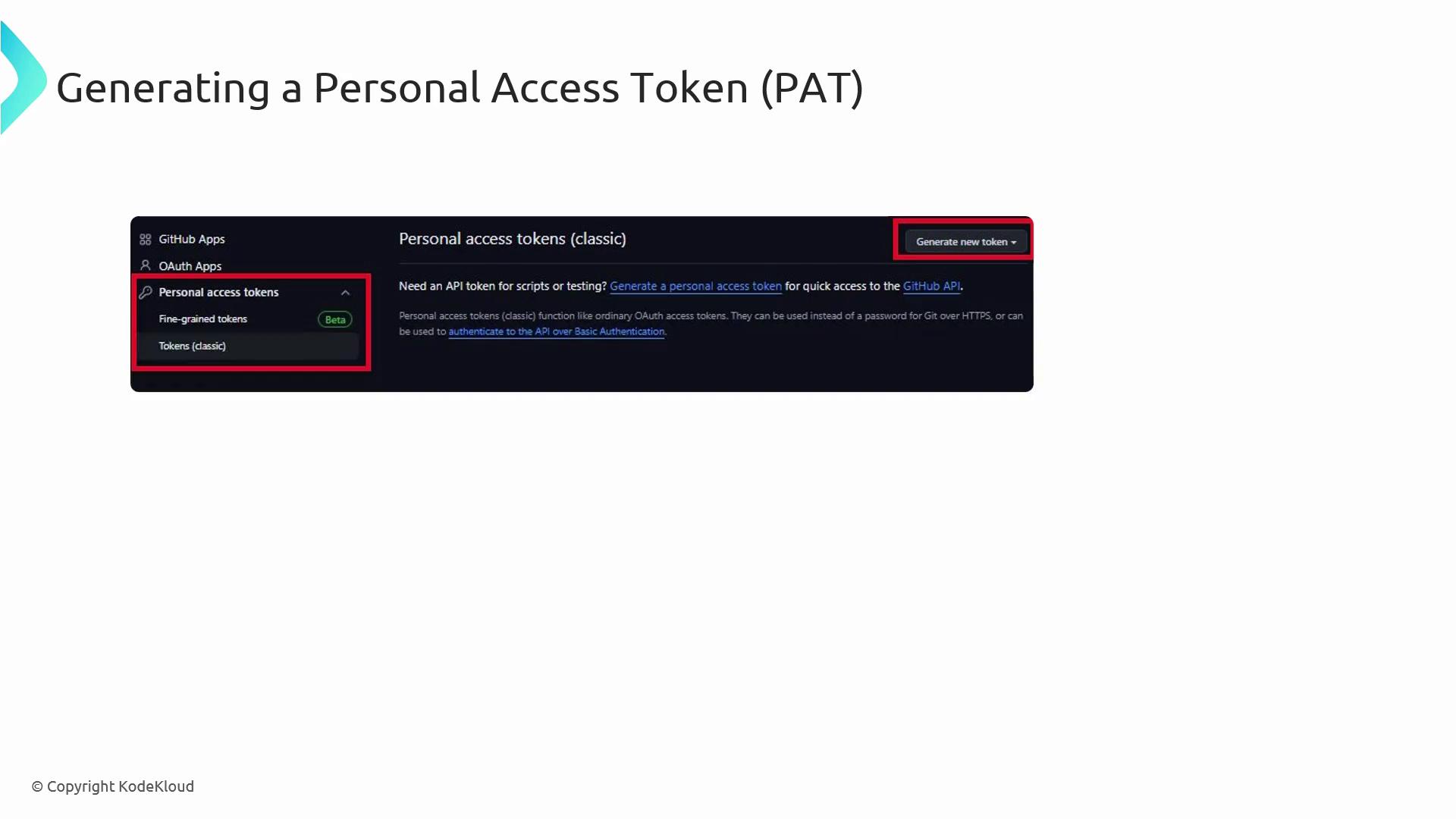
Generating a PAT
- In GitHub Settings, open Developer Settings → Personal access tokens.
- Click Generate new token.
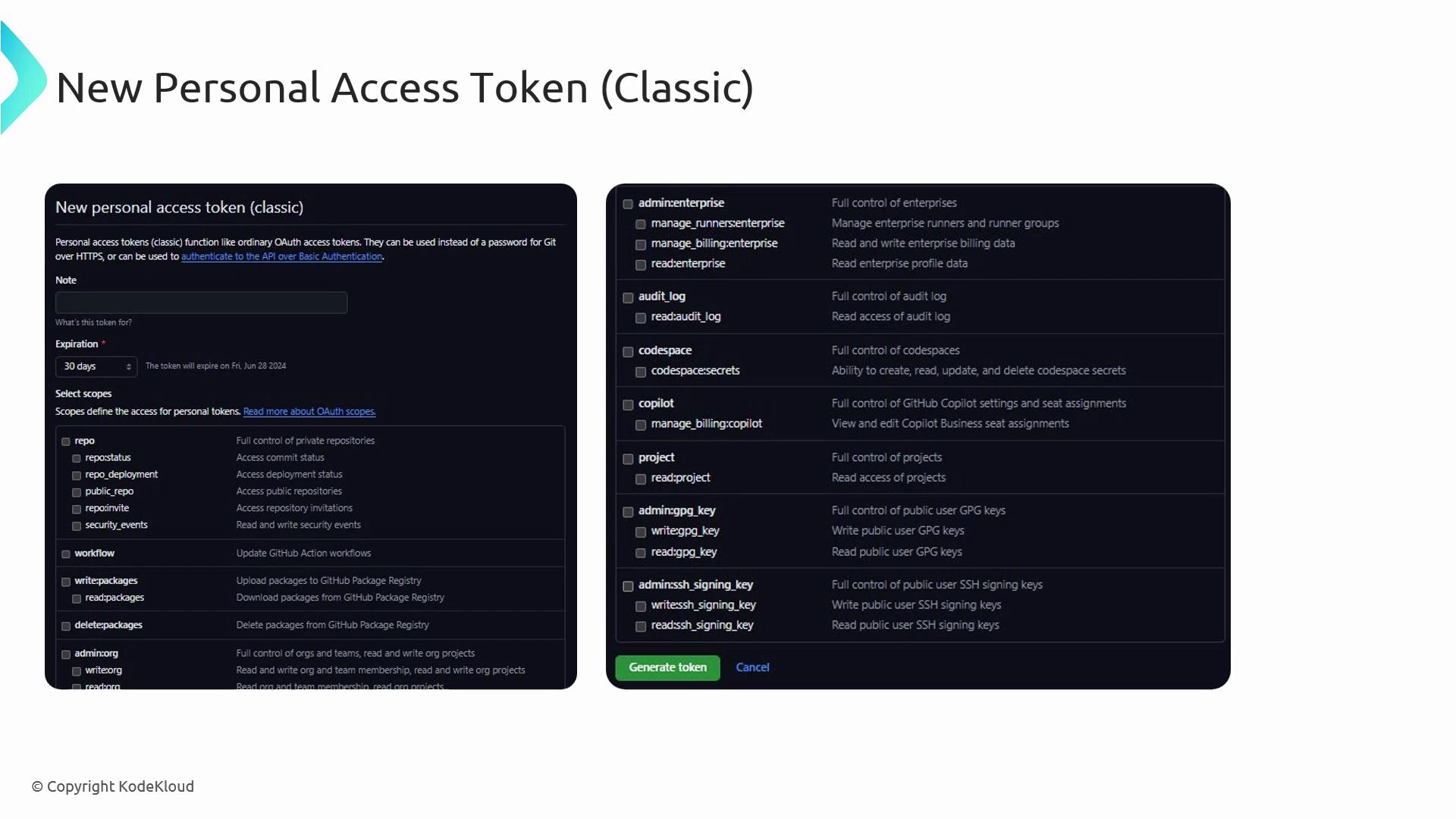
- Choose classic or fine-grained.
- Select scopes (e.g.,
repo,workflow,admin:org). - Generate the token and store it securely.
Authenticating with a PAT
Include the token in theAuthorization header for API calls:
Store PATs in a secure vault or GitHub Secrets, rotate them regularly, and avoid embedding them in code.
Method Comparison and Best Practices
| Method | Scope | Rotation | Ideal Use Case |
|---|---|---|---|
| GitHub Apps | Org & repo, fine-grained | Manual/API | Integrations, bots, automated workflows |
| GITHUB_TOKEN | Single repo | Auto-rotated | GitHub Actions workflows |
| PATs | User-level, broad or narrow | Manual | CLI scripts, local development, third-party tools |
- Grant the minimum required permissions.
- Rotate keys and tokens frequently.
- Monitor audit logs for unauthorized access.
- Enforce SAML SSO, OAuth apps, and branch protection rules.