Table of Contents
- Traffic Flow Fundamentals
- Kubernetes Networking Basics
- Default Behavior vs. Intentional Isolation
- Defining a NetworkPolicy
- CNI Plugin Support
- Further Reading
Traffic Flow Fundamentals
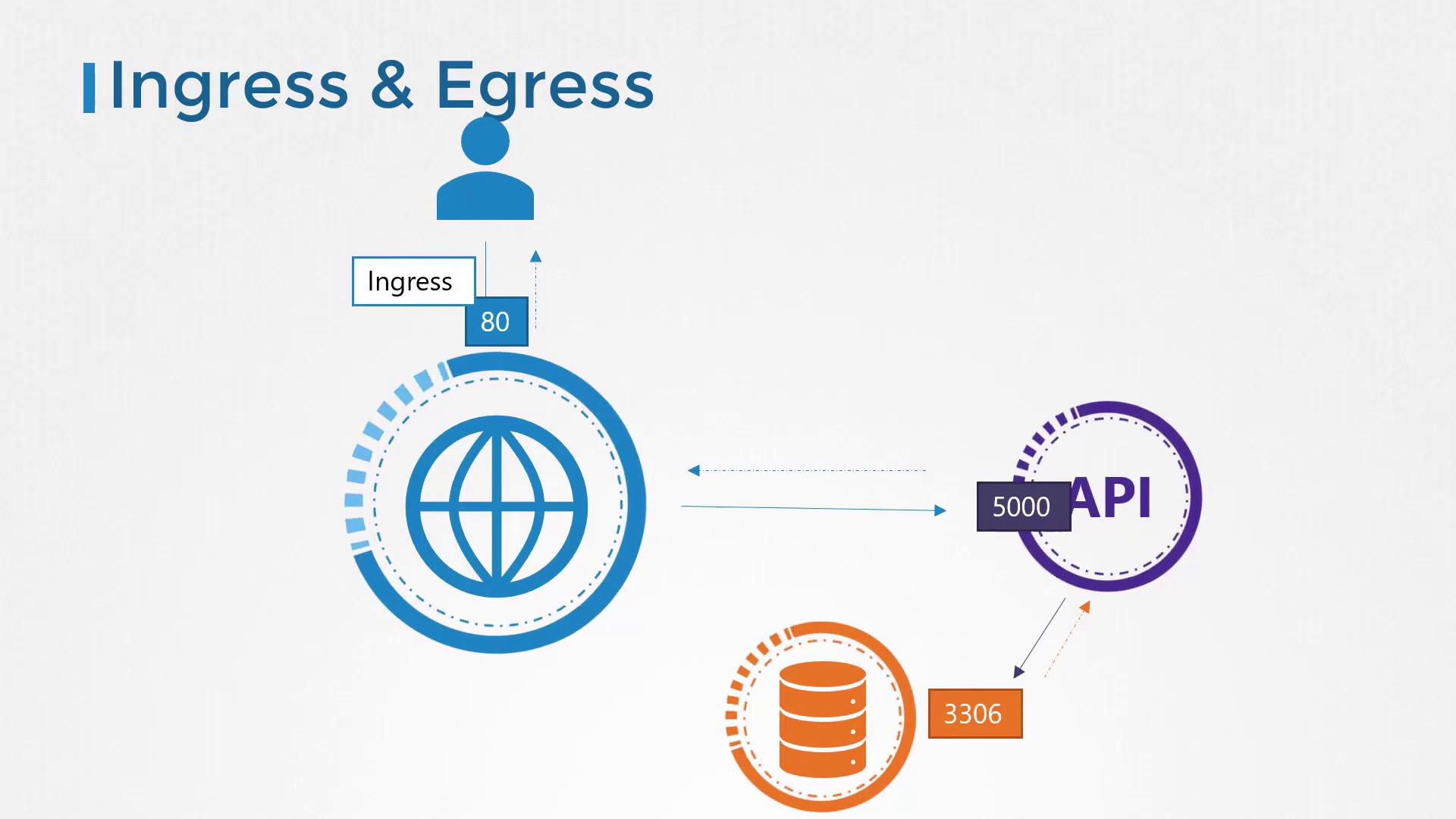
Consider a three-tier application:- Web Server: Receives HTTP requests (port 80).
- API Server: Processes logic (port 5000).
- Database Server: Stores data (port 3306).
- User → Web server on port 80: ingress to the web server
- Web server → API server on port 5000: egress from web, ingress to API
- API server → Database on port 3306: egress from API, ingress to database
Response packets for established connections are automatically allowed. You only need to define rules for the initial traffic direction.
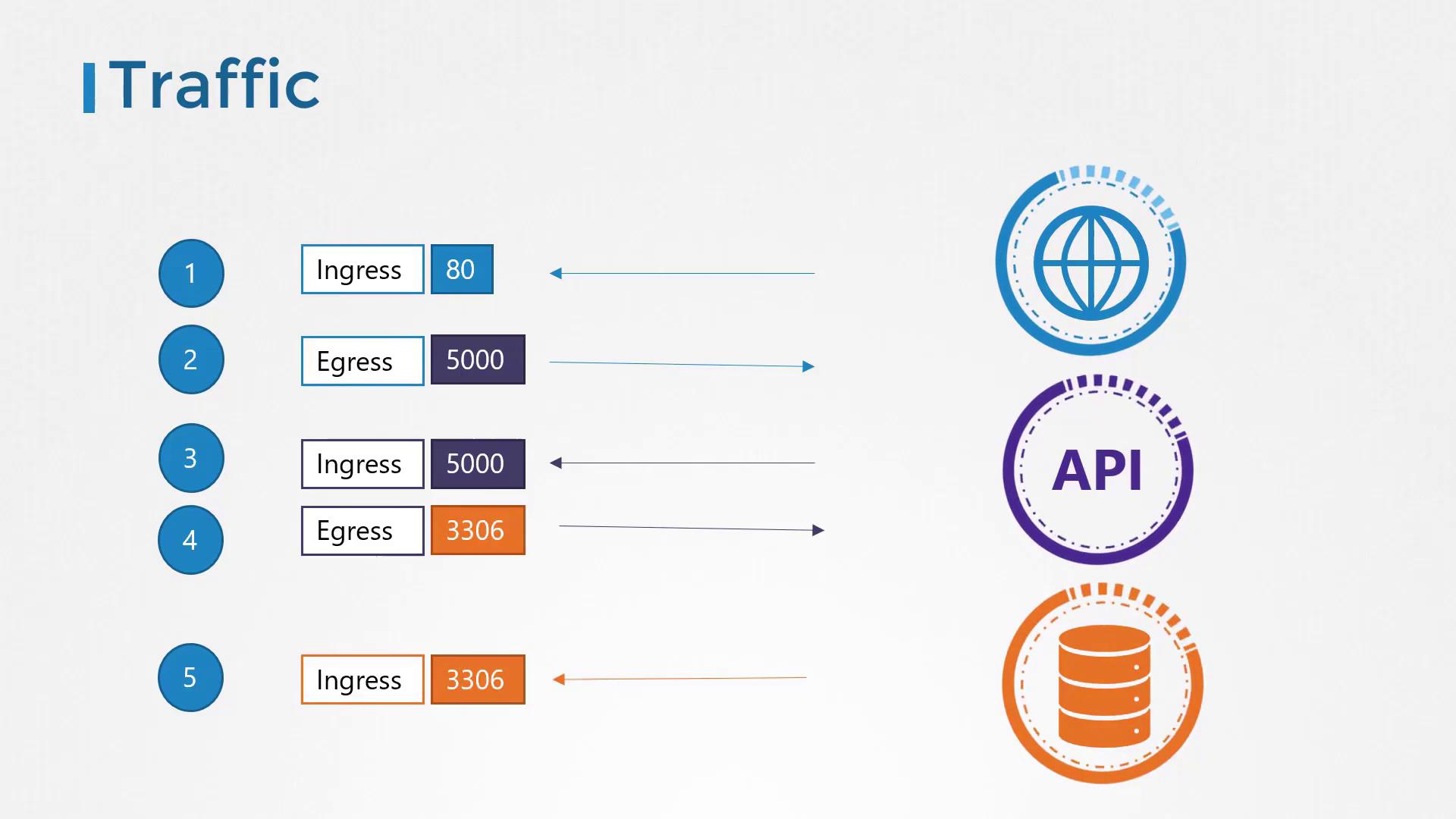
- Web Server
- Ingress: TCP port 80
- Egress: TCP port 5000 to API
- API Server
- Ingress: TCP port 5000
- Egress: TCP port 3306 to Database
- Database Server
- Ingress: TCP port 3306
Kubernetes Networking Basics
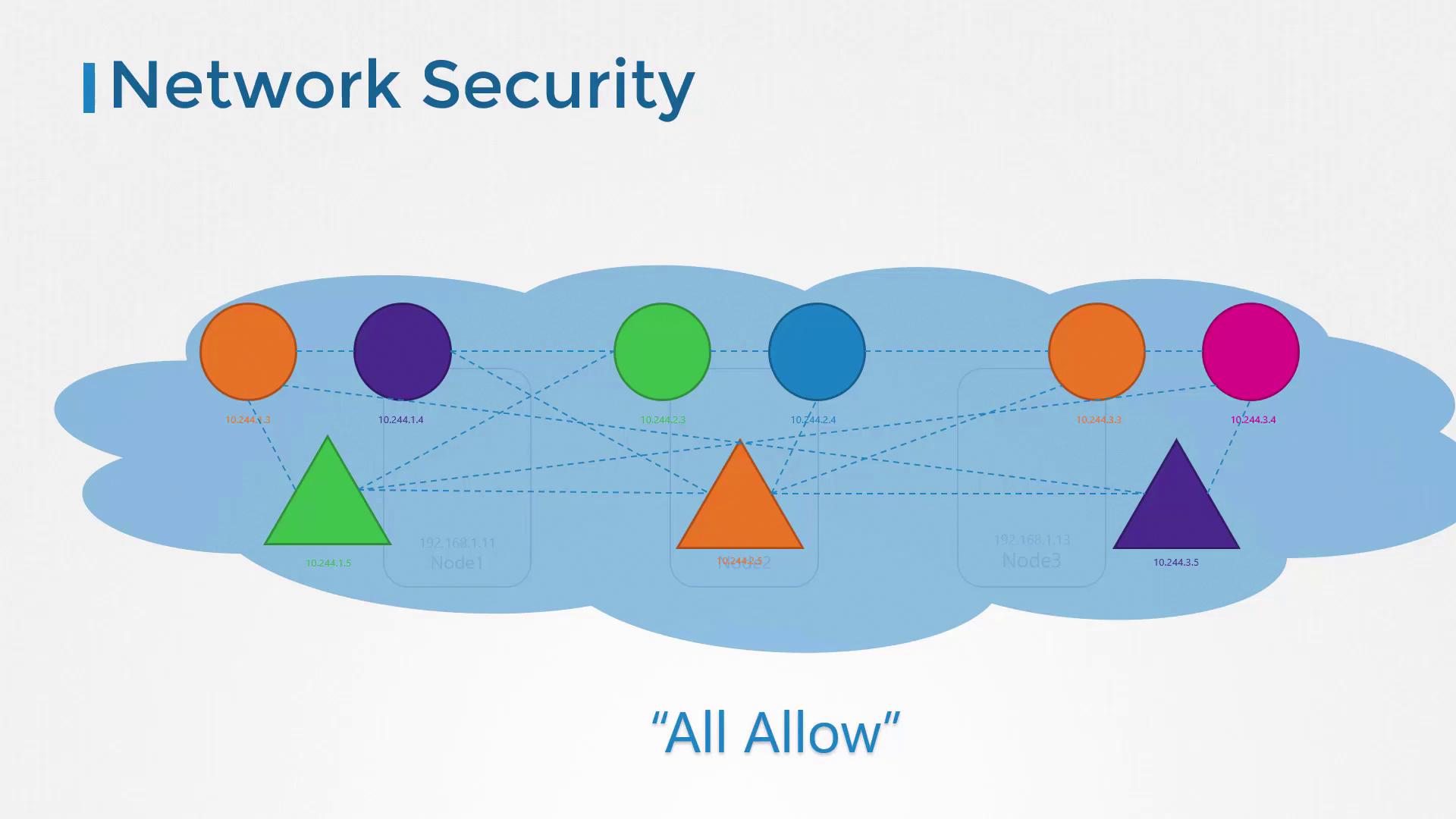
In a Kubernetes cluster with a compliant CNI plugin:- All pods share a flat virtual network.
- Pods reach each other via IP or DNS.
- Services provide stable endpoints (
ClusterIP,NodePort,LoadBalancer). - Default behavior: allow all pod-to-pod traffic.
Default Behavior vs. Intentional Isolation
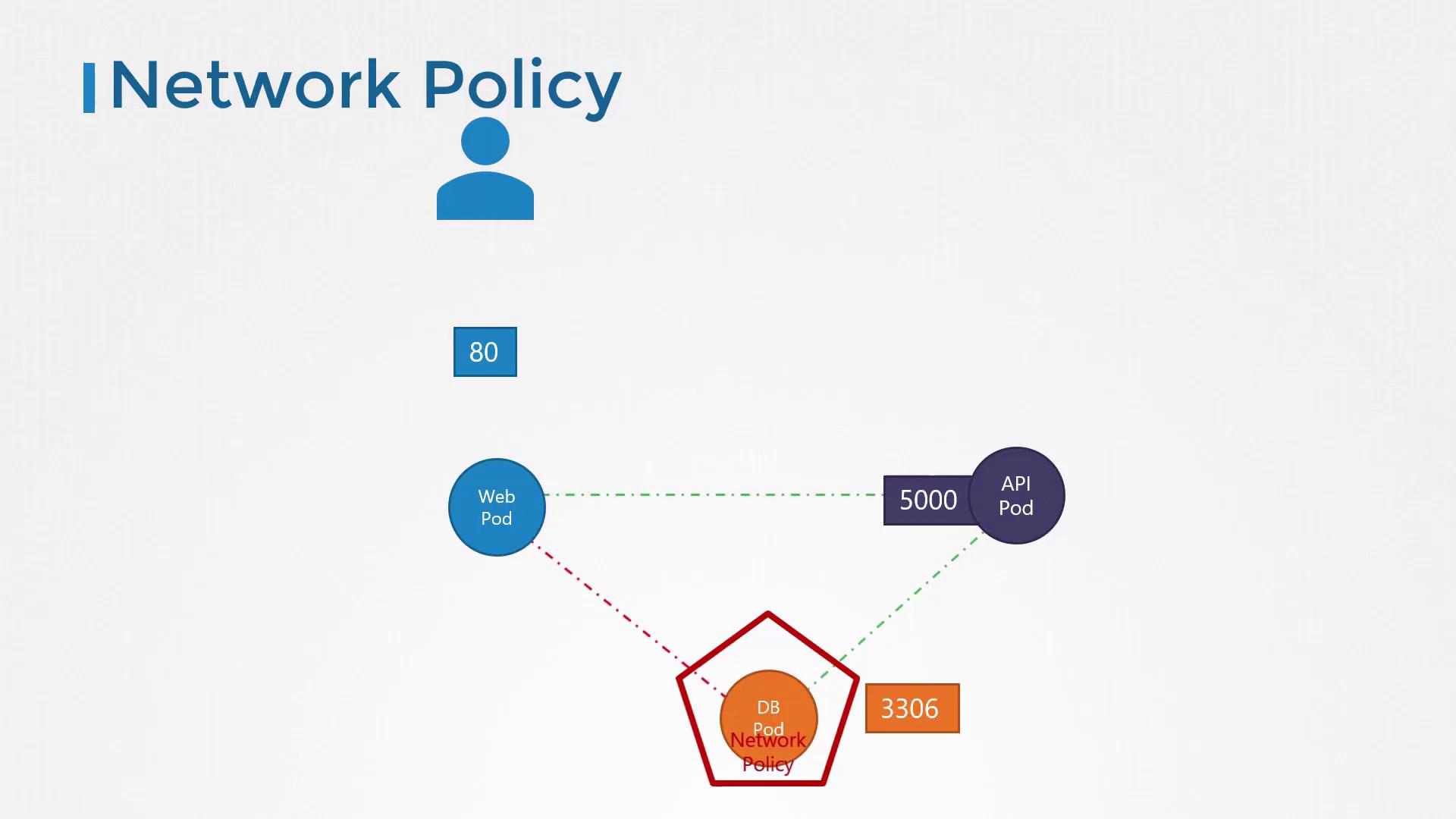
Deploying our three tiers on Kubernetes:- Web Pod exposed on port 80 via a Service.
- API Pod exposed on port 5000 via a ClusterIP Service.
- DB Pod exposed on port 3306 via a ClusterIP Service.

Defining a NetworkPolicy
ANetworkPolicy:
- Resides in a namespace and selects pods via
podSelector. - Specifies
policyTypes:Ingress,Egress, or both. - Lists allowed traffic rules; any unspecified traffic is denied.
Example: Restrict DB Pod Ingress
- Label the DB pod
Add a label to your Pod manifest: - Create the NetworkPolicy
Only allow pods labeledname: api-podto connect on port 3306: - Apply the policy
name=api-pod may reach the DB Pod on TCP port 3306. All other ingress is denied, while egress from the DB Pod remains unrestricted.
CNI Plugin Support
Not all CNI plugins enforce NetworkPolicies. Below is an overview:| CNI Plugin | NetworkPolicy Support |
|---|---|
| Kube-router | Yes |
| Calico | Yes |
| Romana | Yes |
| Weave Net | Yes |
| Flannel | No |
Flannel does not enforce NetworkPolicies by default. You may still create policy objects, but they won’t take effect. Always verify your CNI’s capabilities in its documentation.
