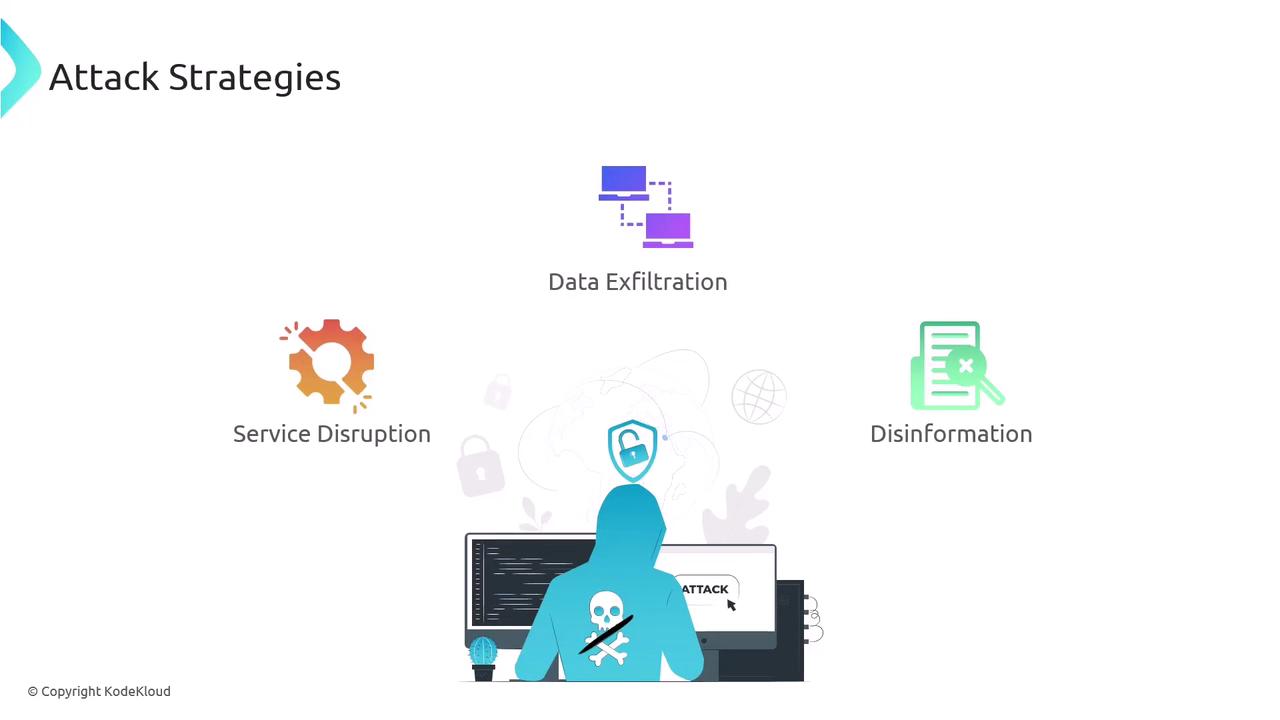
- Disrupting services or taking a website offline.
- Exfiltrating sensitive data from the target.
- Spreading disinformation by altering website content or posting false information on social media.
A prevalent motivation behind service disruption attacks is to create chaos, often driven by a desire for revenge. Such motivations can be especially dangerous when the threat actor is an insider, such as a former employee.
Types of Threat Actors
Hackers
Hackers possess the technical skills required to gain unauthorized access to systems. Although many associate hackers with breaches, some are authorized to test system vulnerabilities—commonly known as white hat hackers. On the other hand, unauthorized attackers are referred to as black hat hackers, and less sophisticated individuals using pre-made tools are often called “script kiddies.” More sophisticated and well-funded groups include nation-state actors and organized crime-affiliated hackers.Nation-State Threat Actors
Nation-state threat actors are typically well-financed and specialize in executing advanced persistent threats (APTs). These attackers establish long-term, covert access to target systems, frequently focusing on government agencies or critical infrastructure. In some instances, nation-states outsource operations to local organized crime groups to implement ransomware-as-a-service or other elaborate strategies.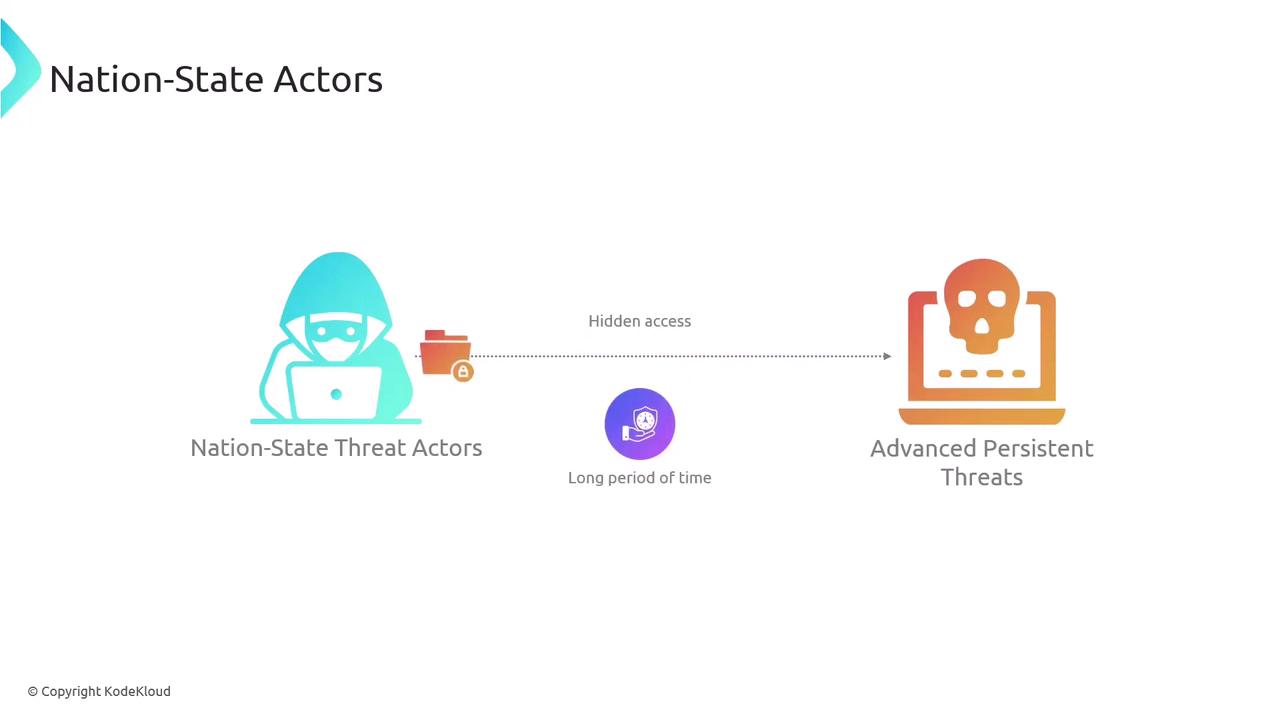
Organized Crime Threat Actors
Organized crime groups pose considerable challenges due to their cross-jurisdictional operations, which complicate investigations and prosecutions. These actors often execute their campaigns in regions other than their own, further escalating the difficulties encountered by law enforcement agencies.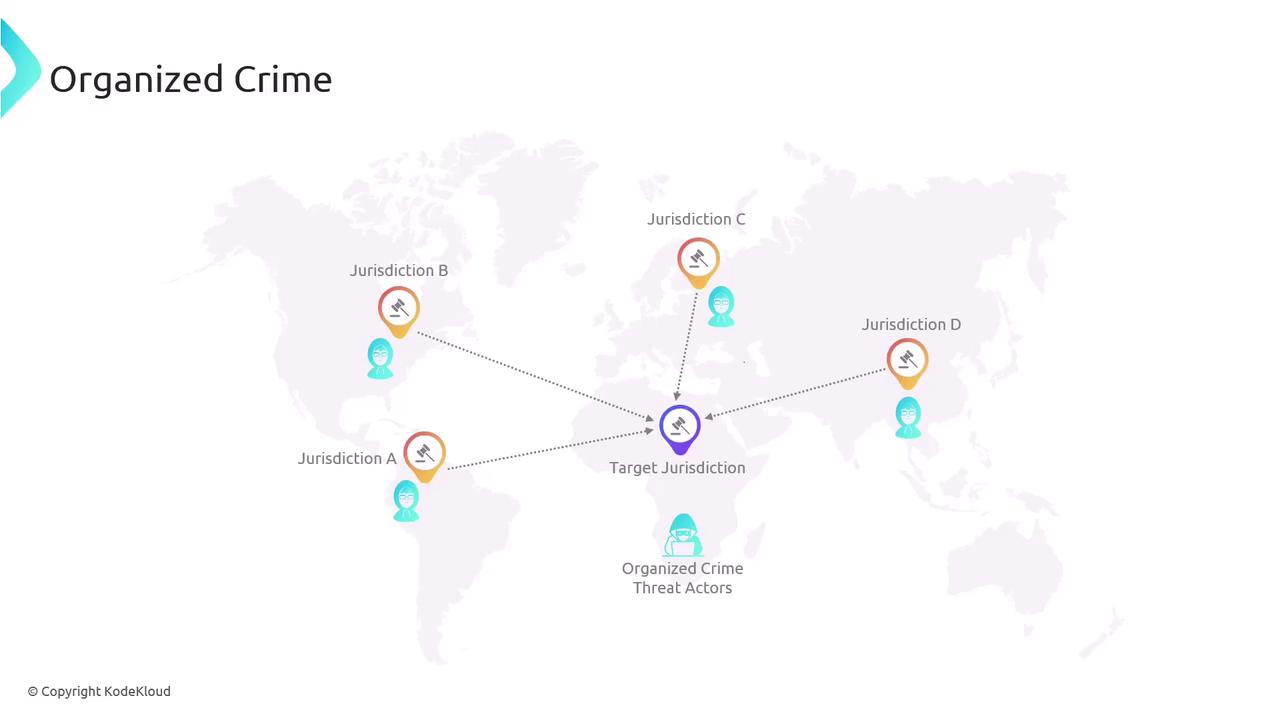
Corporate Espionage
Corporate espionage involves competitors infiltrating organizations to gain a market advantage by stealing trade secrets or sensitive information. This form of cyber espionage adds another layer of complexity to the cybersecurity landscape.Insider Threats
Insider threats can originate from both malicious actions and unintentional mistakes. Individuals with authorized access might misuse their privileges to sabotage operations, steal data for financial benefit, or disrupt services. For instance, an insider may remotely log in to download files and transfer them to a personal device. Additionally, unintentional insider threats can result from inadequate security training, weak policies, or shadow IT—when employees independently purchase or use unauthorized IT equipment or services.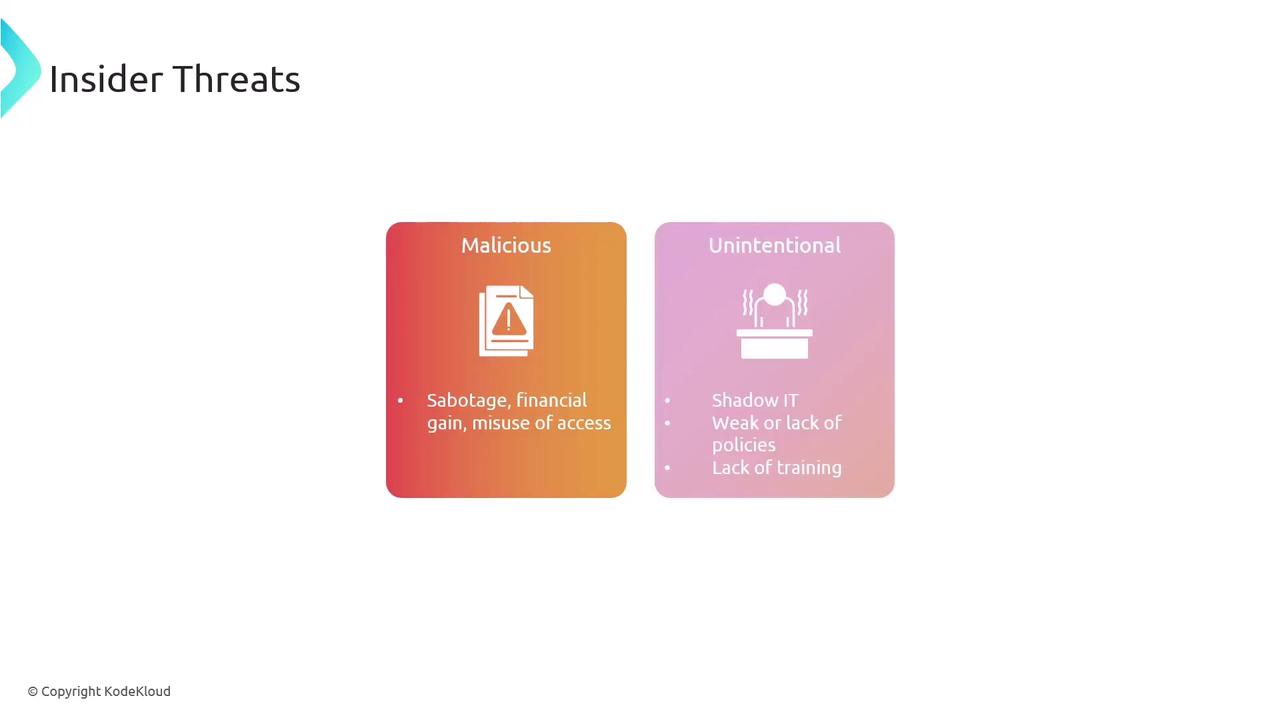
Always ensure that internal access and permissions are appropriately managed. Regular training and updated security policies can help mitigate the risks associated with insider threats.