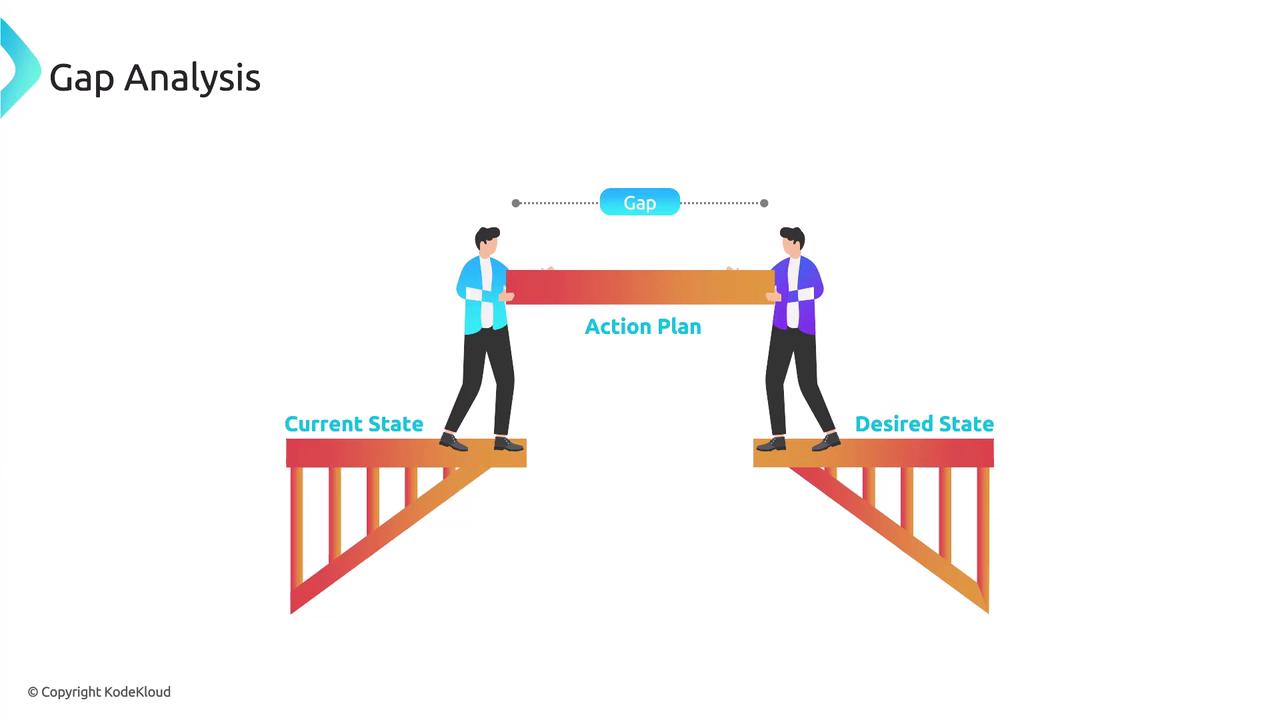
Conducting a gap analysis provides a clear pathway for enhancing your organization’s security measures by identifying specific vulnerabilities and areas for improvement.
Using the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is built on standards, guidelines, and best practices that help organizations manage cybersecurity risks systematically. Its structure, organized around five key functions, enables organizations to effectively implement and enhance security measures. Let’s explore each function in detail:1. Identify
The Identify function involves understanding your organization’s critical systems, assets, data, and associated risks. This foundational step in a cybersecurity gap analysis requires you to:- Inventory all assets (hardware, software, data, etc.) to ensure that nothing critical is overlooked.
- Identify current security policies and procedures for subsequent comparison with industry best practices.

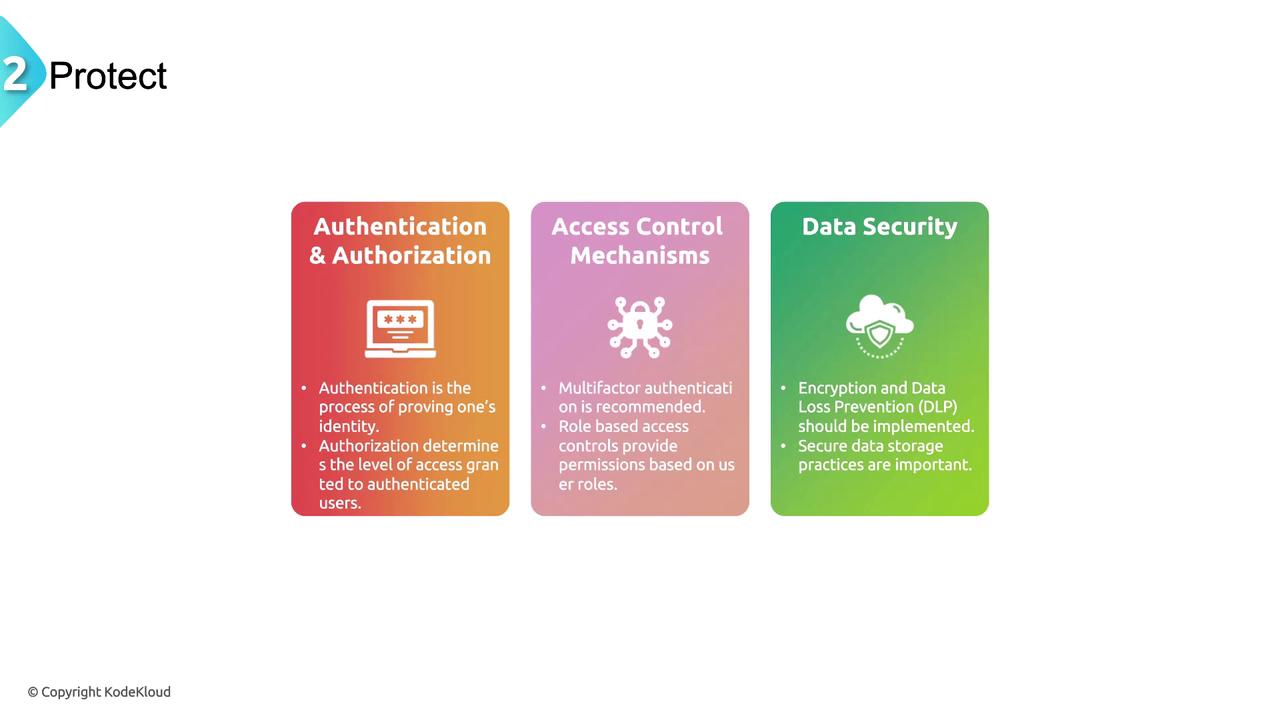
2. Protect
The Protect function focuses on implementing safeguards to ensure the delivery of critical infrastructure services. In this phase, you should:- Evaluate current access control mechanisms and enforce strong authentication and authorization protocols.
- Incorporate practices such as multi-factor authentication (MFA) and role-based access controls.
- Assess data protection measures like encryption, Data Loss Prevention (DLP), and secure data storage practices.
- Review training and awareness programs, alongside regular maintenance plans including security patching and software updates.
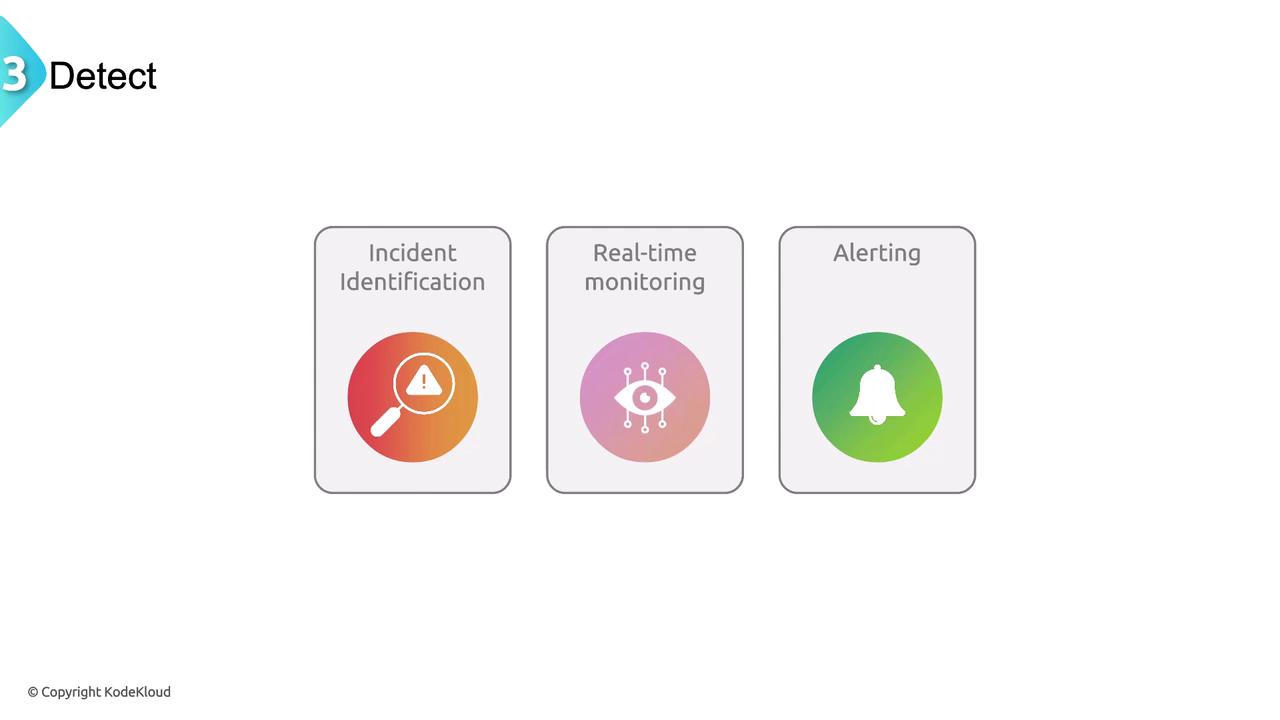
3. Detect
The Detect function is all about implementing the necessary activities to identify cybersecurity events as they occur. Key initiatives include:- Establishing real-time monitoring and alerting mechanisms.
- Deploying automated tools that continuously monitor your network and systems.
- Defining what constitutes normal activity in order to effectively detect anomalies or intrusions.
4. Respond
The Respond function involves setting up and testing incident response plans to manage cybersecurity breaches effectively. This includes:- Reviewing and refining the efficiency of current incident response plans.
- Developing and practicing detailed procedures for incident response and communication to ensure a coordinated reaction when a breach is detected.
5. Recover
The Recover function is dedicated to restoring any capabilities or services that are impaired following a cybersecurity incident. Best practices in this phase include:- Developing a resilient recovery plan that is regularly reviewed and improved.
- Ensuring that recovery strategies remain adaptable to address new and emerging cyber threats.
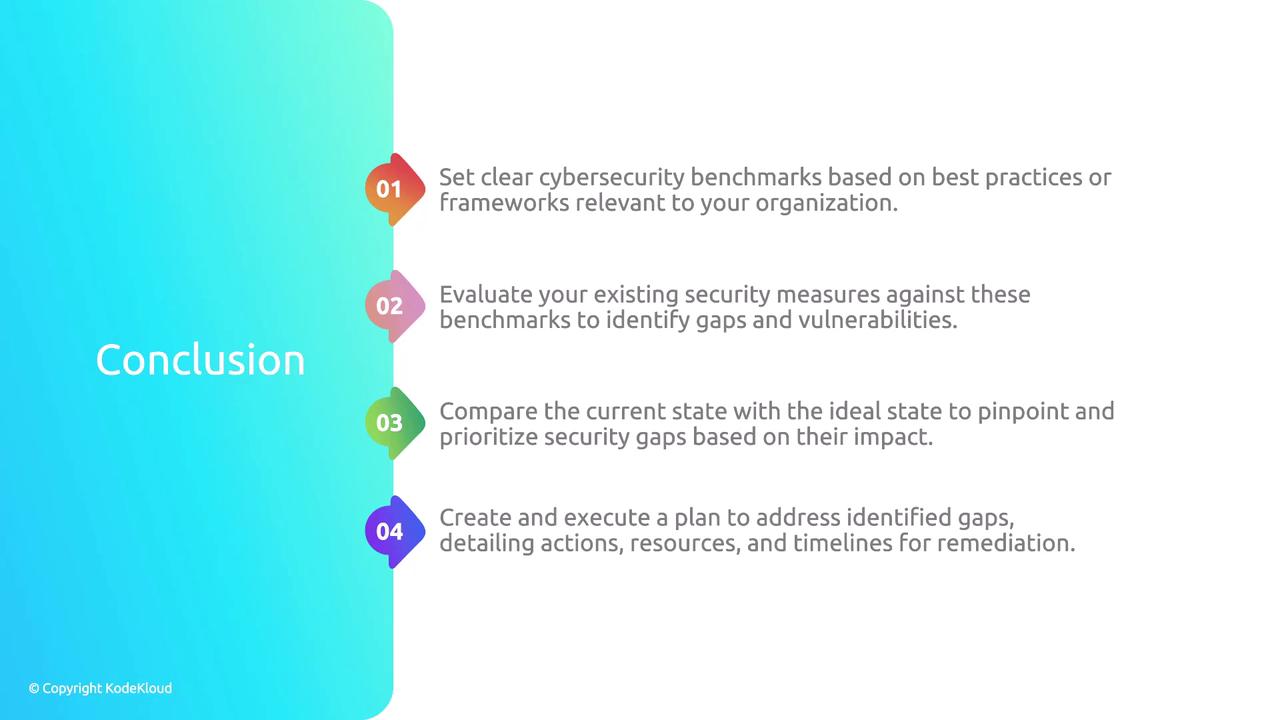
Conclusion
In this lesson, we used the NIST Cybersecurity Framework as an example to illustrate the process of a gap analysis. The primary goal of a gap analysis is to identify and address cybersecurity vulnerabilities by comparing your ideal state with your current state. Although the NIST framework is widely adopted, other frameworks may be used depending on regional or organizational preferences—the process remains fundamentally the same. Conducting a thorough gap analysis is a powerful strategy to bolster your organization’s cybersecurity defenses. By systematically evaluating the functions of Identify, Protect, Detect, Respond, and Recover, organizations can significantly reinforce their security posture against evolving cyber threats.