Before diving into vulnerabilities, it is crucial to have a solid grasp of core cloud concepts, as these form the foundation for identifying and mitigating risks.
Core Cloud Concepts
Cloud platforms deliver virtualized IT services that companies can rent, significantly lowering costs and management overhead compared to maintaining internal infrastructure.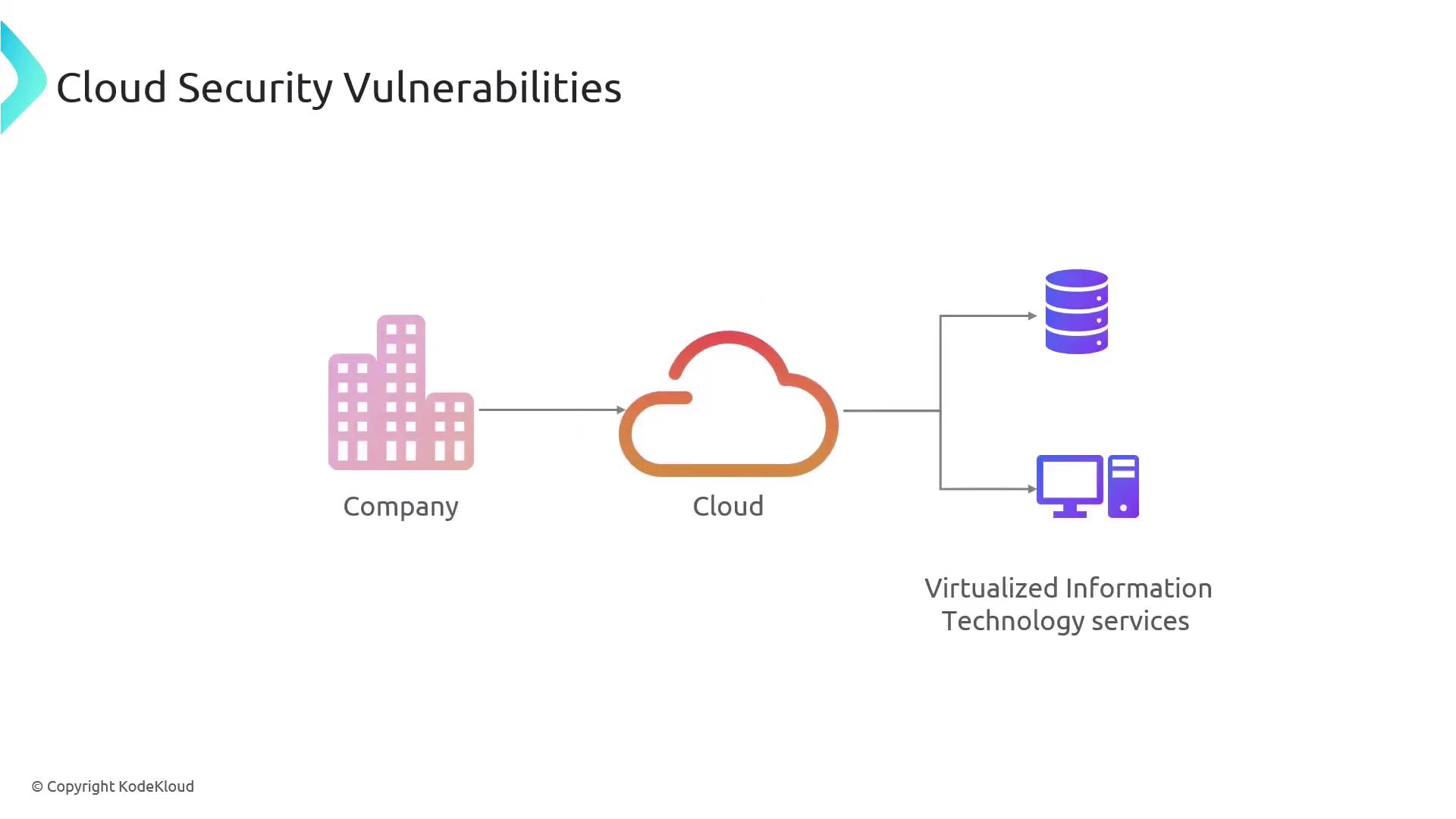
Cloud Service Models
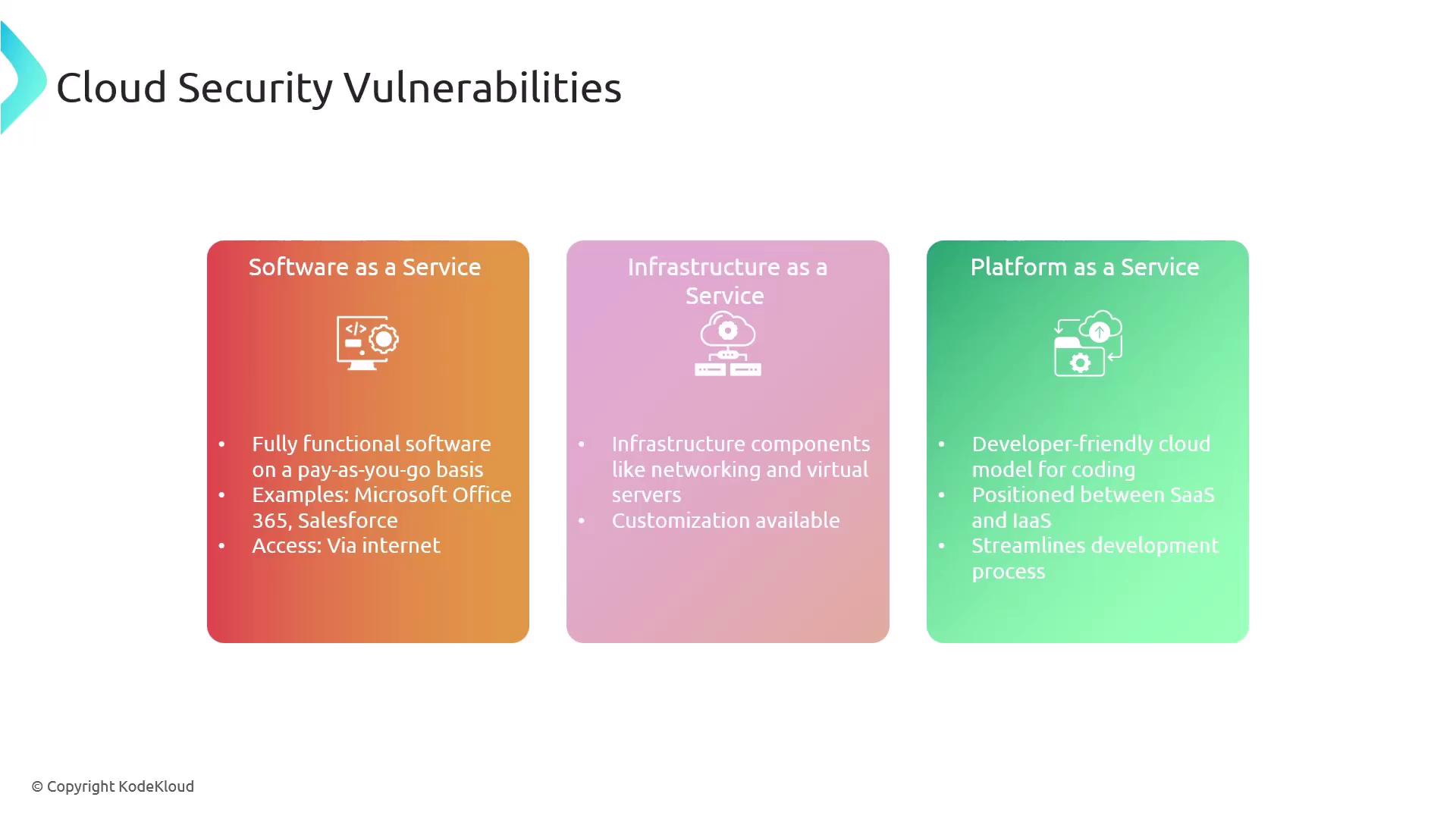
Cloud services typically follow one of these models:| Service Model | Description | Examples |
|---|---|---|
| Software as a Service (SaaS) | Provides fully functional software on a pay-as-you-go basis. Users access applications directly over the Internet without local installation. | Microsoft Office 365, Salesforce |
| Infrastructure as a Service (IaaS) | Offers virtualized IT components such as networks, servers, and storage. Allows organizations to configure and manage their own infrastructure. | Amazon EC2, Microsoft Azure VM |
| Platform as a Service (PaaS) | Provides a developer-friendly environment for building and deploying applications in the cloud without managing the underlying infrastructure. | Heroku, AWS Elastic Beanstalk |
Supply Chain Dependencies
Many organizations depend on external suppliers, vendors, and business partners to support manufacturing and distribution processes. These relationships often require external entities to have connectivity to your systems, expanding your security perimeter.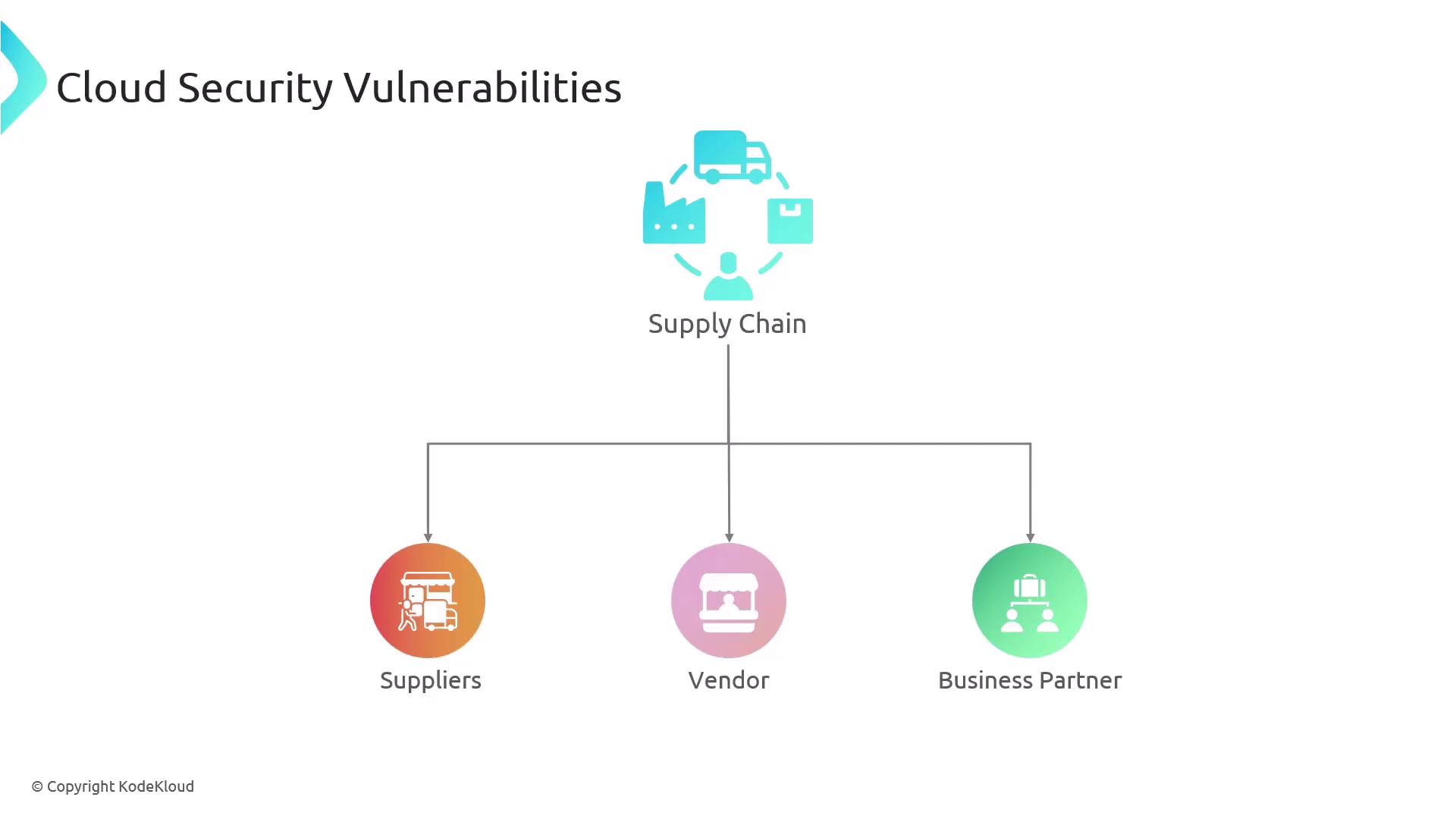
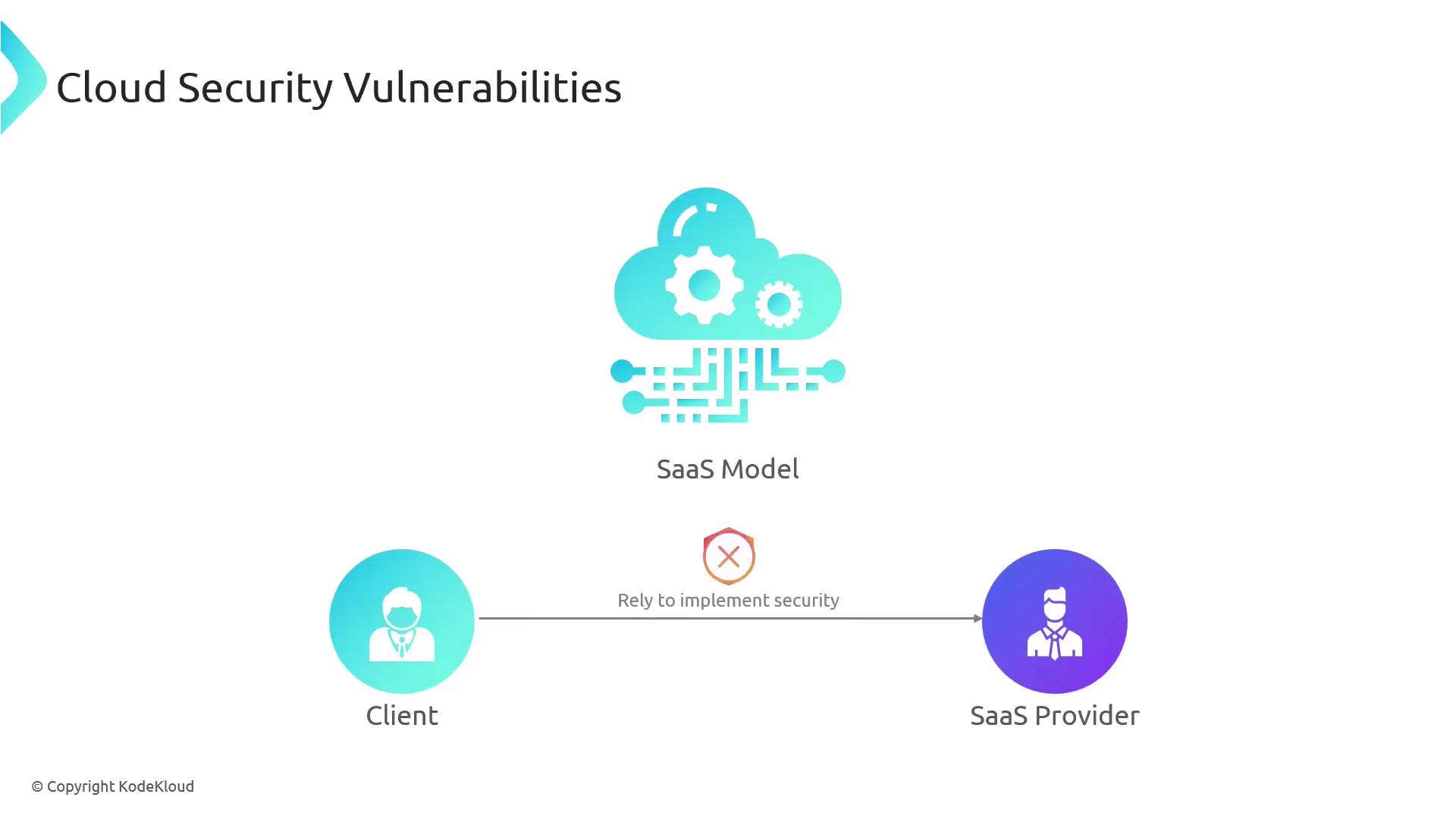
In a SaaS model, your security is tied to the provider’s practices. If they fail to adhere to the Confidentiality, Integrity, and Availability (CIA) principles or employ weak security measures, both your organization and the provider may be at increased risk.