
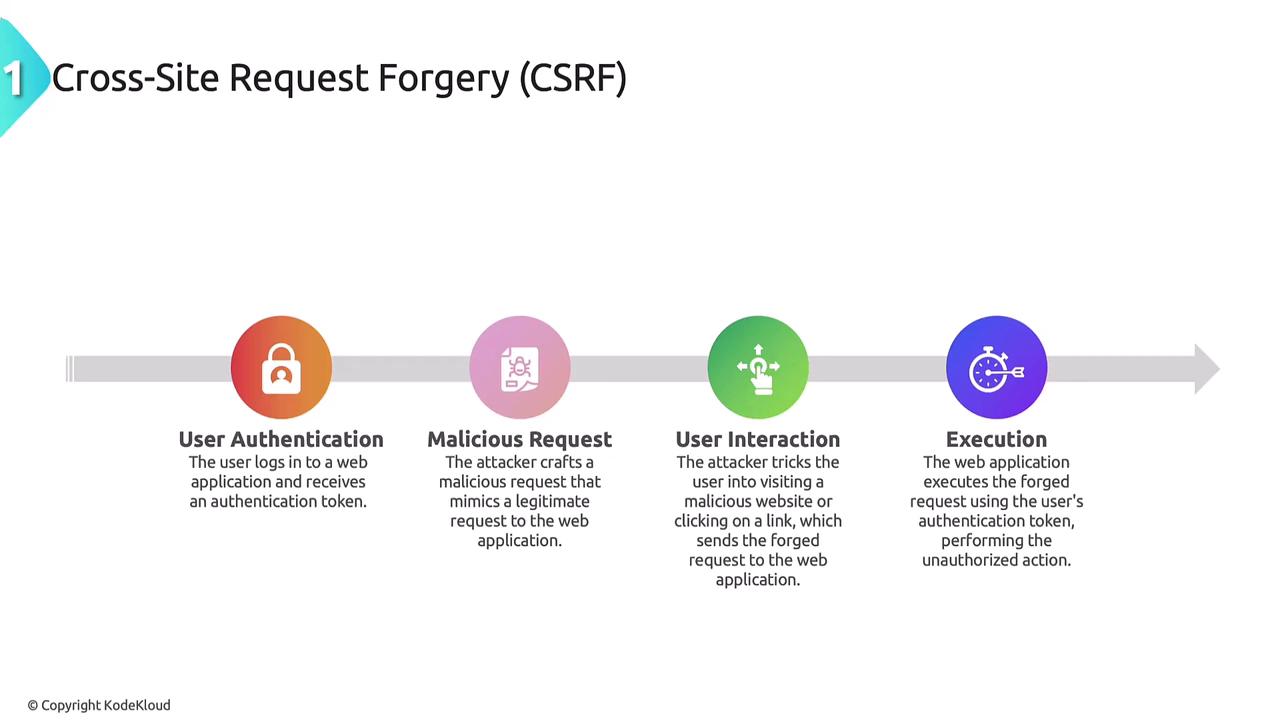
Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) tricks a user into performing actions on a web application without their consent. Typically, the process involves the user authenticating on a website, after which the attacker leverages the active session to send unauthorized requests.
- The user logs into a web application and receives an authentication token or session cookie.
- The attacker crafts a malicious request that mimics a legitimate one.
- The attacker tricks the user into visiting a malicious website or clicking on a deceptive link.
- The web application executes the forged request using the user’s active authentication token, resulting in unauthorized actions.
Ensure that web applications implement anti-CSRF tokens and verify the origin of HTTP requests to mitigate CSRF attacks.
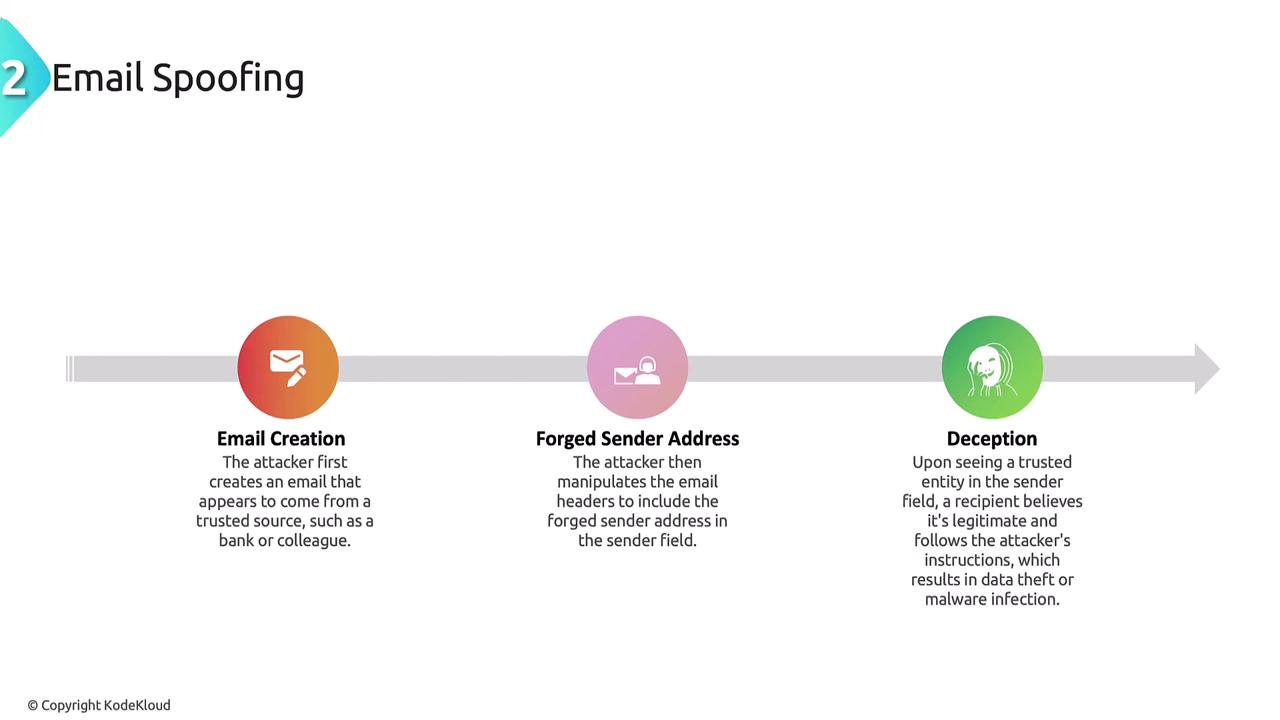
Email Spoofing
Email spoofing involves forging email messages by using a fabricated sender address to deceive recipients. In this attack, the attacker impersonates a trusted entity to manipulate the recipient into taking harmful actions, such as revealing sensitive information or installing malware. The email spoofing process typically includes:- Crafting an email that appears to be sent from a trusted source, such as a bank or colleague.
- Manipulating the email headers to include a forged sender address.
- Deceiving the recipient into believing the email is genuine, prompting them to follow instructions that may lead to data theft or malware infection.
Always exercise caution when receiving unexpected emails, especially those requesting sensitive information or urging immediate action. Verify the sender’s authenticity via trusted channels before complying.
Conclusion
Forgery application attacks, including CSRF and email spoofing, represent significant security risks. By comprehending these attack methods, organizations and individuals can implement stronger safeguards to protect sensitive data and prevent unauthorized actions.