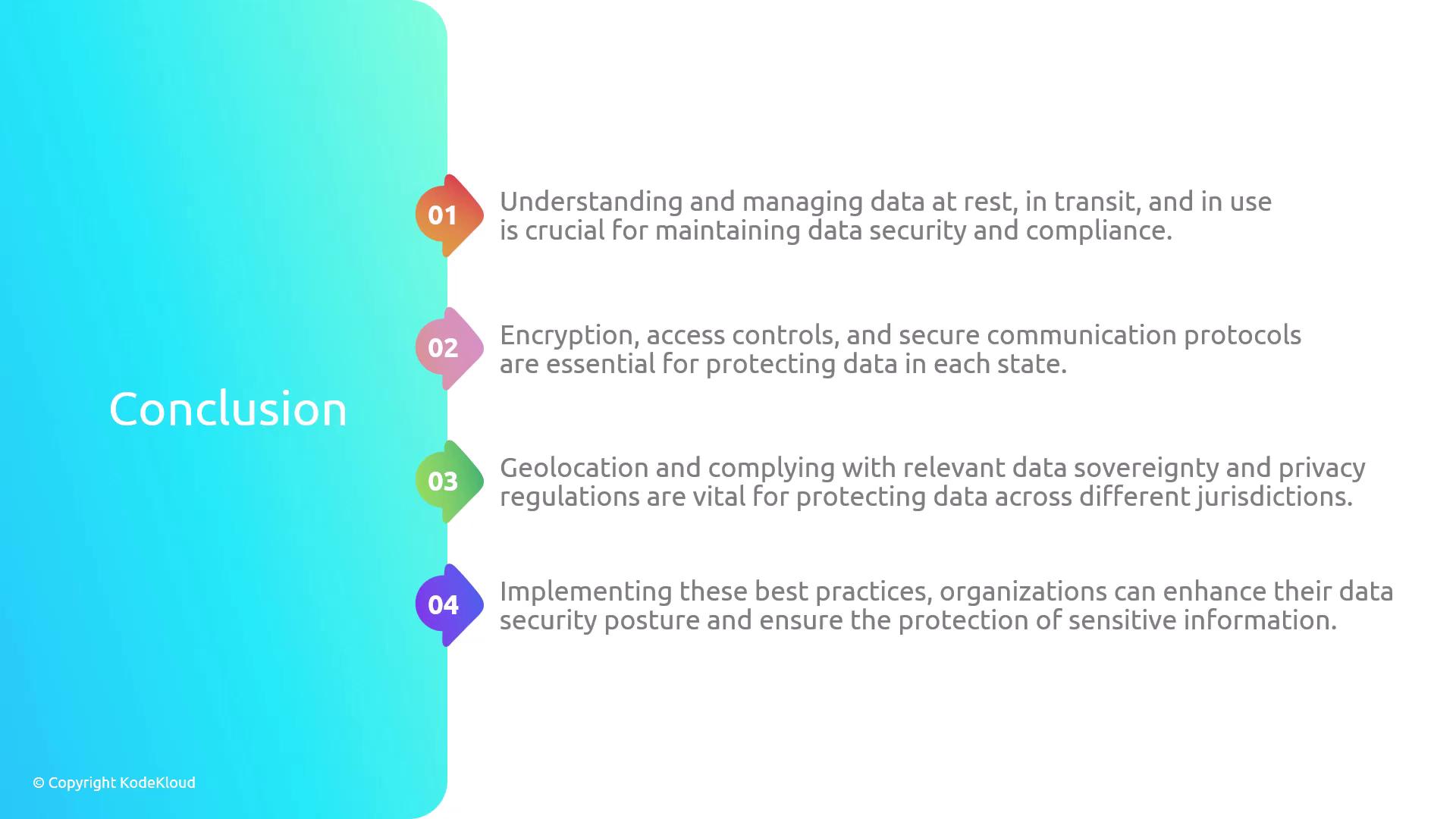
Data at Rest
Data at rest refers to information stored on physical or virtual media that is not actively moving through networks or being processed. This includes databases, data warehouses, archives, or backups that reside on hard drives or other storage devices. Even though this information is inactive, it remains susceptible to unauthorized access if not properly secured. Key security measures include:- Encrypting stored data to protect it against unauthorized access.
- Enforcing strict access controls to minimize potential exposure.
- Performing regular security audits to ensure protection mechanisms remain effective.
Always ensure that data at rest is secured with modern encryption methods and regularly updated access controls to mitigate emerging threats.
Data in Transit
Data in transit is the information actively moving between locations, whether across the internet or within private networks. Protecting this data is critical since it is often exposed to interception during transfer. Essential measures for securing data in transit include:- Encrypting data during transmission to prevent interception.
- Using secure protocols such as TLS or IPSec to maintain data integrity and confidentiality.
- Securing both the sender and receiver endpoints to ensure a trusted communication channel.
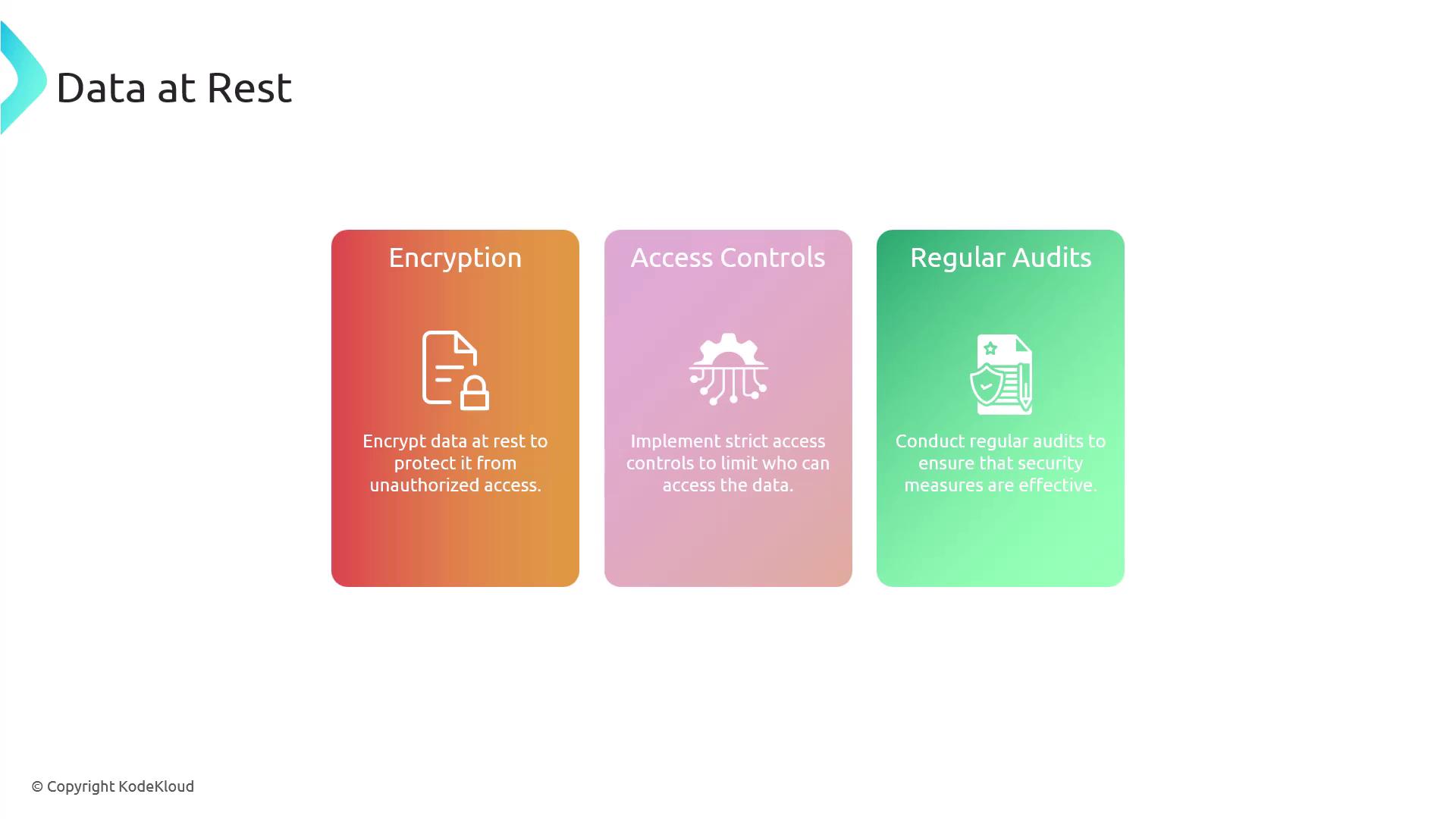
Data in Use
Data in use denotes information that is actively processed by applications, accessed by users, or temporarily held in memory (volatile storage). Since the data is operational, maintaining its security is imperative. Key practices for protecting data in use include:- Ensuring that only authorized users and processes can access the data.
- Hardening applications and systems to prevent unauthorized access and potential data breaches.
- Leveraging memory protection technologies such as secure enclaves and hardware security modules (HSMs).
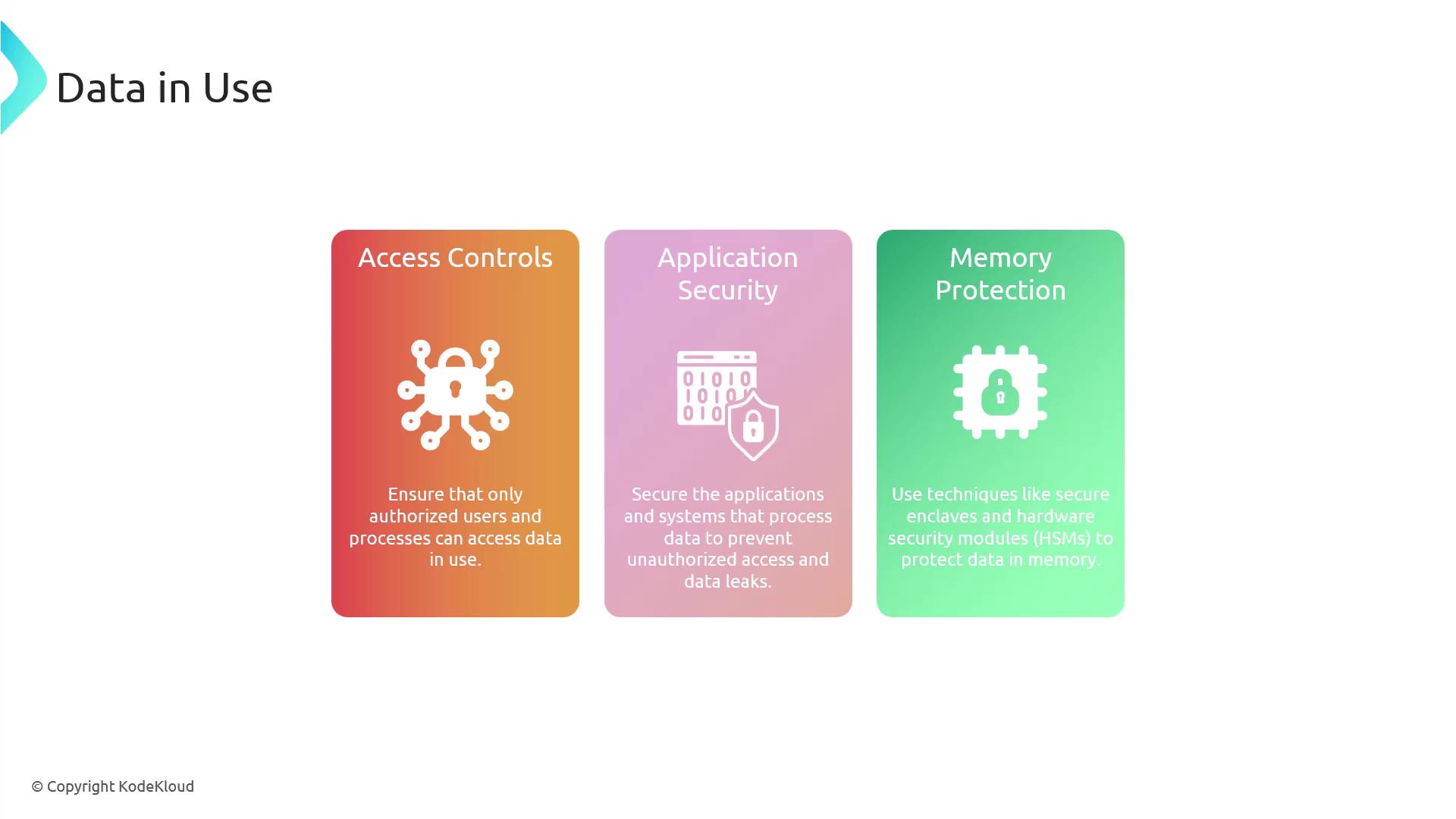
Geolocation and Its Impact
Geolocation involves determining the physical location of a device, data, or user. Its role in data security is increasingly significant due to the following considerations:- Data Sovereignty: Regulatory requirements that mandate data storage and processing within specific geographical regions.
- Data Privacy Regulations: Legal frameworks such as GDPR, CCPA, and HIPAA which impose data protection requirements based on the user’s location.
- Access Controls: The use of geolocation-based restrictions to ensure that data is accessed only from pre-authorized locations.
Non-compliance with regional data protection and privacy laws can result in severe financial penalties and damage to organizational reputation.
Conclusion
In summary, managing data security effectively requires understanding the unique challenges presented by data in its various states—at rest, in transit, and in use. Employing robust encryption, stringent access controls, and secure communication protocols are essential components for protecting data. Moreover, acknowledging the influence of geolocation on data security and regulatory compliance is crucial. By enforcing geolocation-based access restrictions and adhering to relevant data protection laws, organizations can enhance their security posture and safeguard sensitive information.