Prerequisites
- A running Kubernetes cluster with Falco installed via Helm
- A Slack workspace with permission to create channels and apps
helmandkubectlCLI tools configured for your cluster
1. Create a Slack Channel
Create a dedicated channel (for example,#falco) to receive Falco alerts.
2. Configure an Incoming Webhook
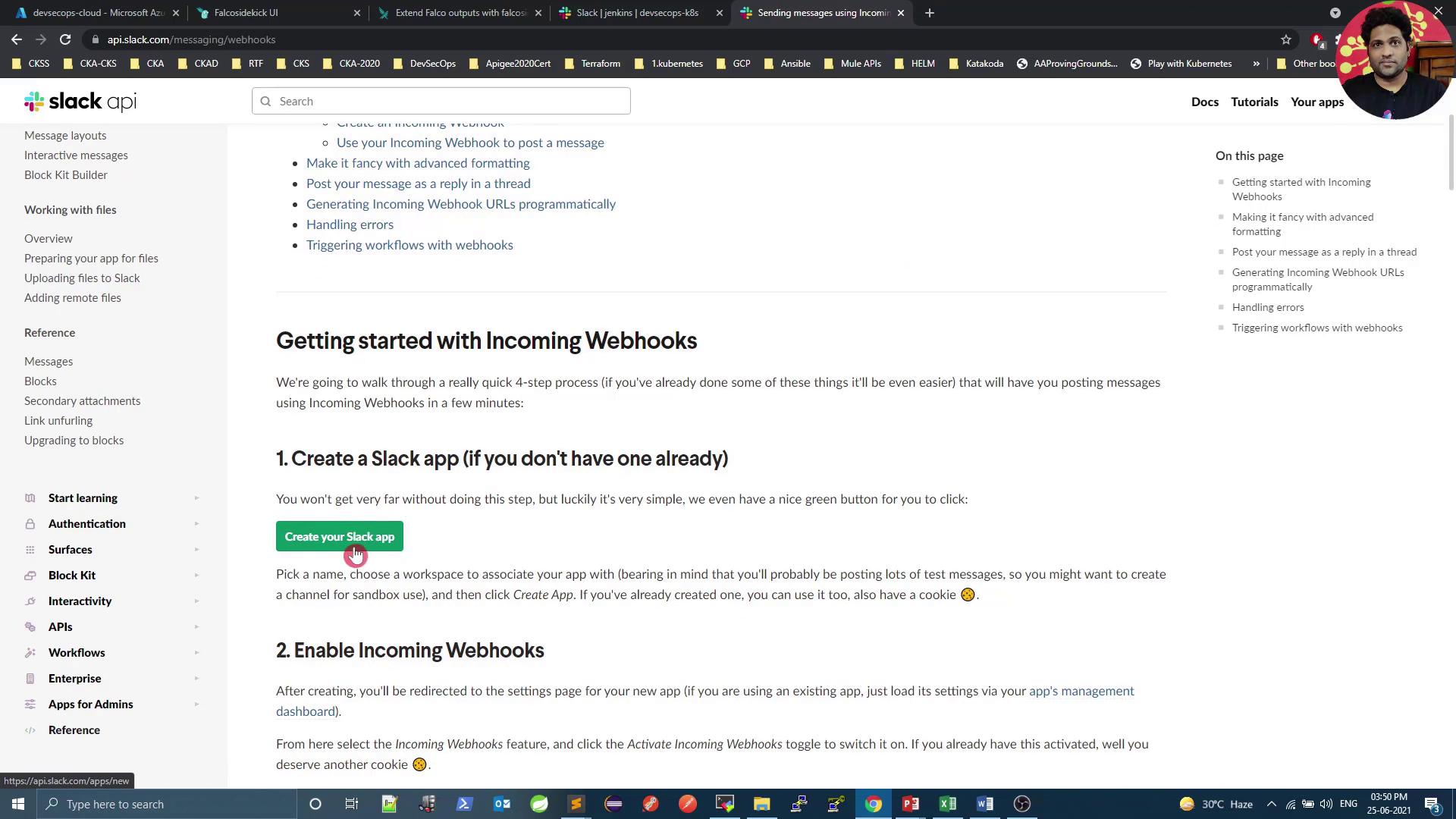
Follow these steps to set up an incoming webhook in Slack.- Open the Slack Incoming Webhooks documentation.
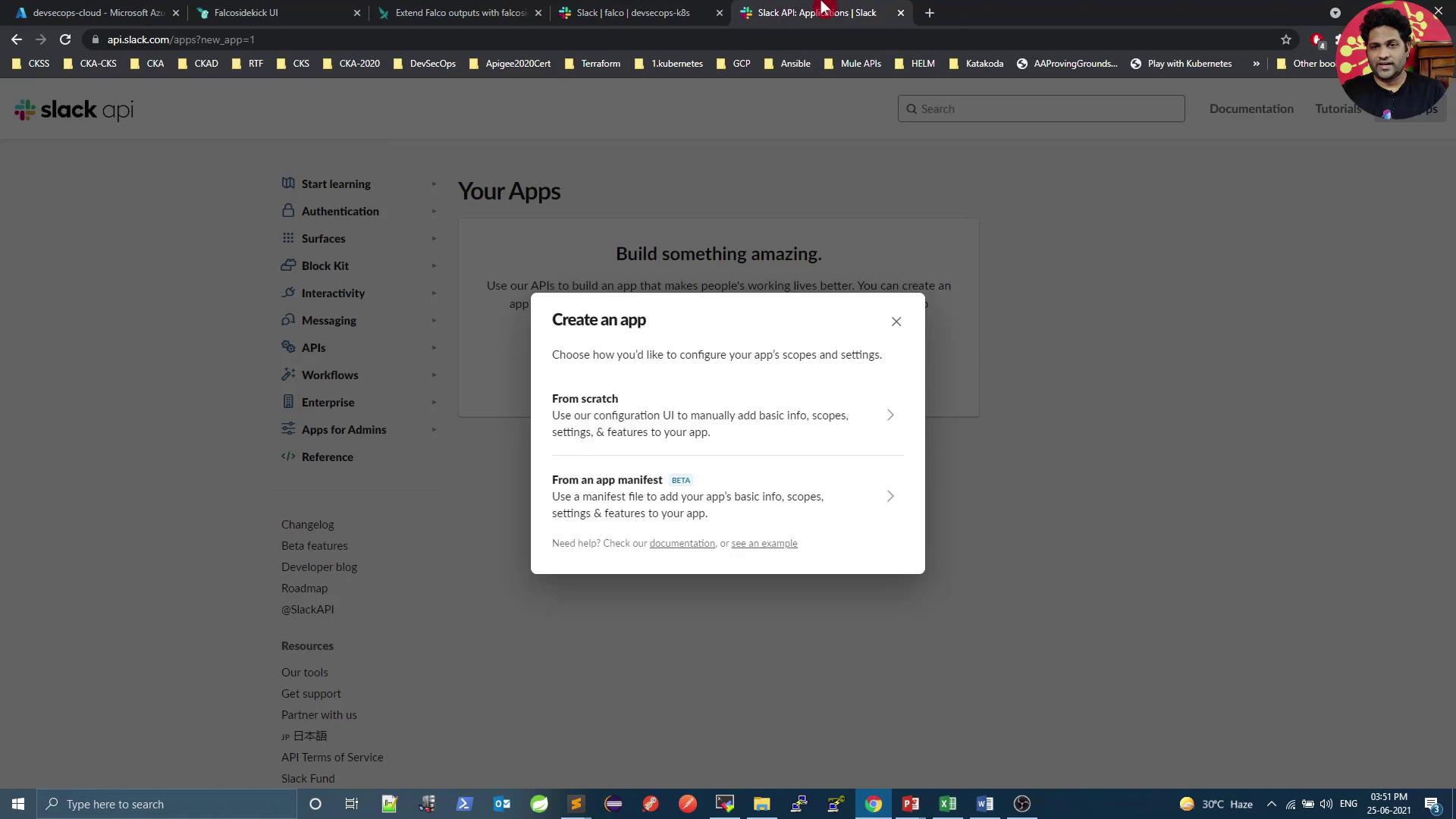
- Click Create an app, choose From scratch, and pick your workspace.
- Under Features, enable Incoming Webhooks.
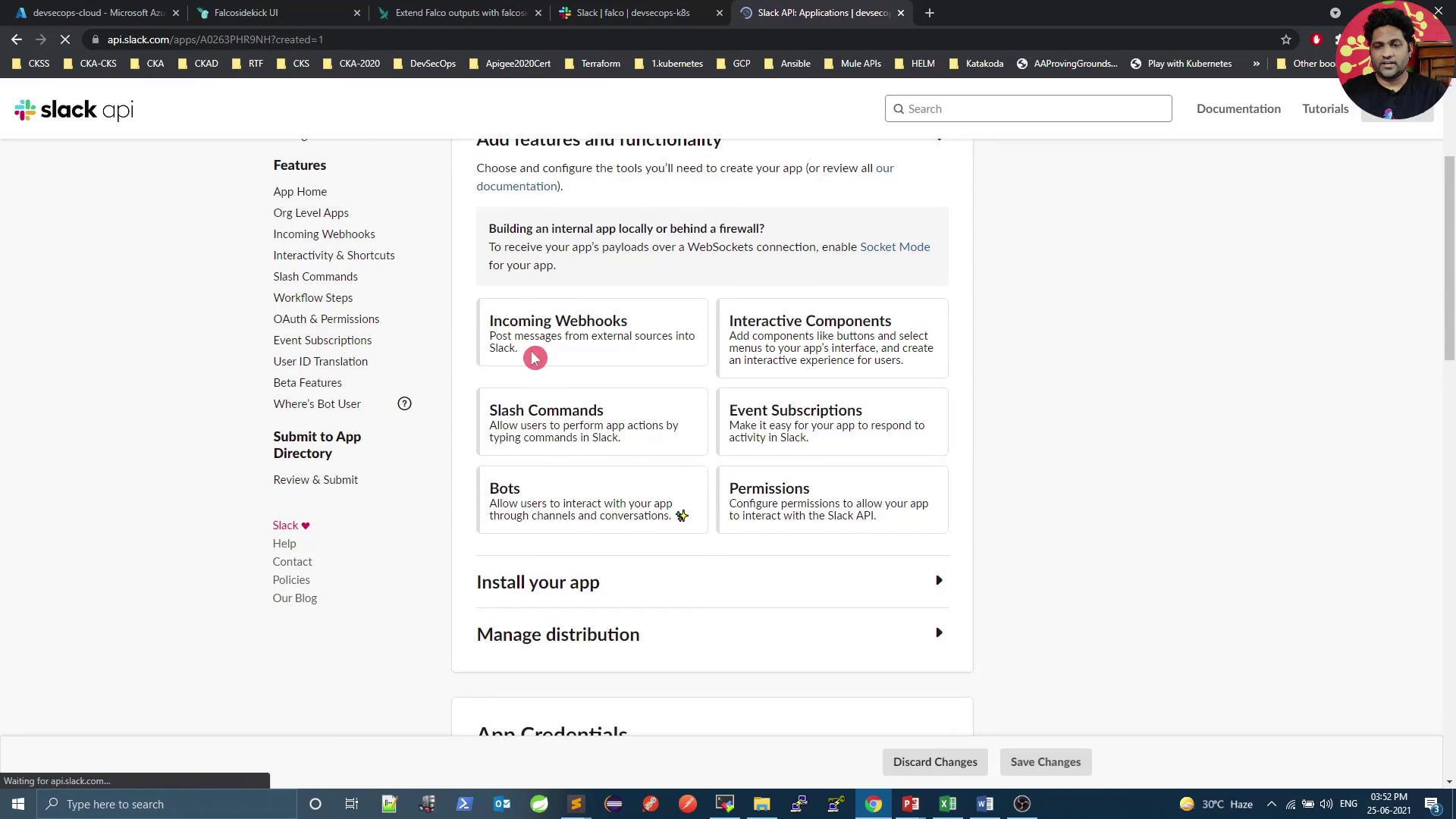
-
Click Add New Webhook to Workspace, select
#falco, and authorize. Copy the generated URL:
Treat your webhook URL like a password. Do not expose it in public repositories.
-
Verify the webhook with
curl:
#falco channel.
3. Install Falco Sidekick with Slack Integration
Use Helm to enable Falco Sidekick and configure Slack:| Configuration Key | Description | Example |
|---|---|---|
| falcosidekick.enabled | Enable Falco Sidekick component | true |
| falcosidekick.webui.enabled | Sidekick Web UI | true |
| falcosidekick.config.slack.webhookurl | Slack incoming webhook URL | "https://hooks.slack.com/services/…" |
| falcosidekick.config.customfields | Custom metadata fields | "environment:production,datacenter:paris" |
4. Trigger a Test Alert
Spawn a shell in a container to generate a Falco alert. Replacen1 with your Pod name:
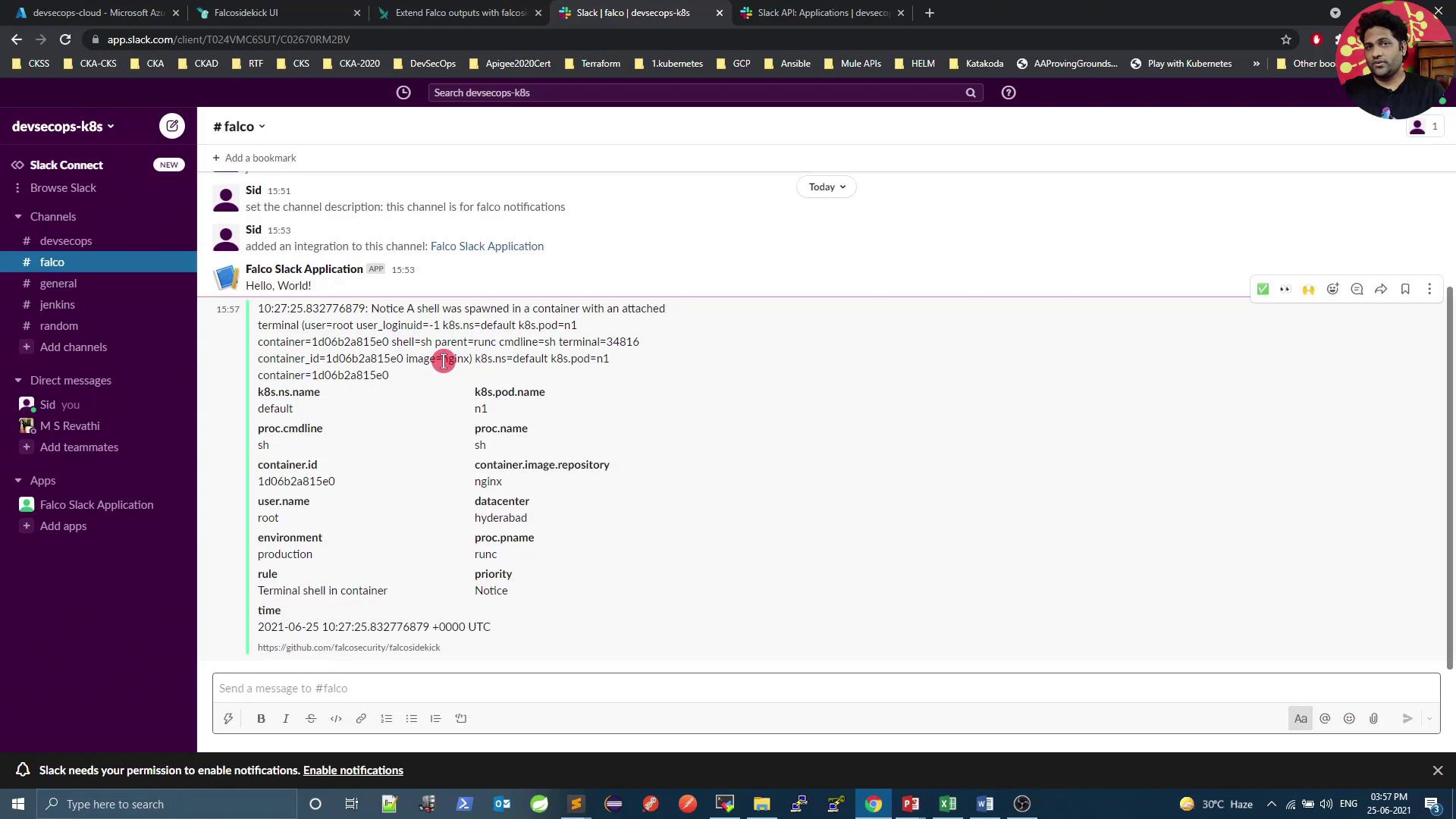
Conclusion
You’ve successfully integrated Falco with Slack for real-time monitoring. To extend this setup—sending alerts to Microsoft Teams, Discord, Elasticsearch, Datadog, and more—update thefalcosidekick.config in your Helm command.