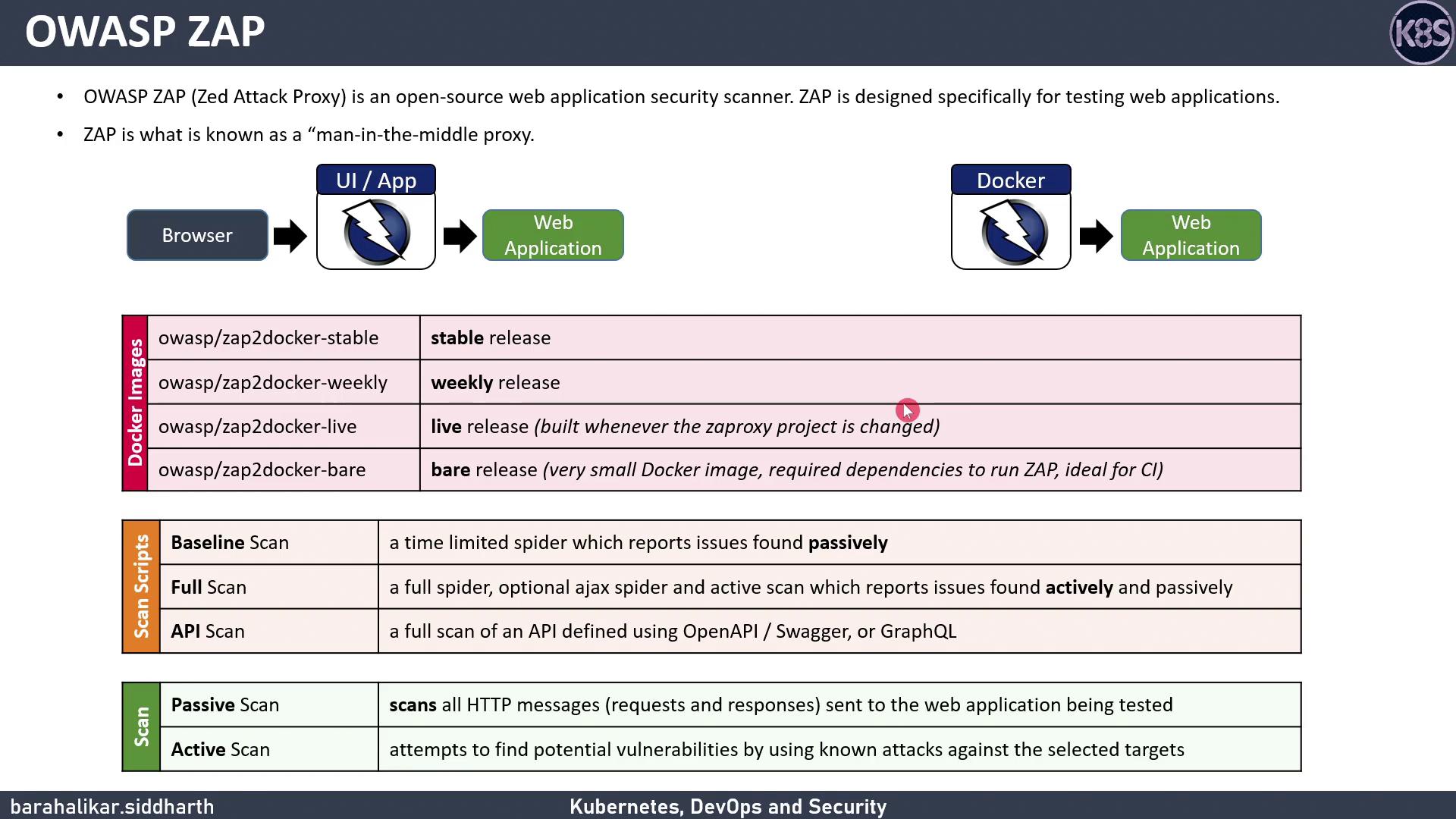
What Is OWASP ZAP?
OWASP ZAP is an open-source web application security scanner that sits between your client and target application as a “man-in-the-middle proxy.” It can:- Intercept and modify HTTP(S) requests and responses
- Perform passive scans to detect vulnerabilities without modifying traffic
- Launch active scans to probe for common attack vectors
- Import API definitions (OpenAPI, Swagger, SOAP, GraphQL) for targeted testing
- Standalone GUI or CLI
- Docker image on Docker Hub
ZAP Scan Types
| Scan Type | Description | Use Case |
|---|---|---|
| Baseline | Time-limited spidering + passive analysis | Smoke test before deployment |
| Full | Ajax spidering + both passive and active scans | Comprehensive web application test |
| API | Imports API definitions + active scan tuned for APIs (skips irrelevant tests like XSS) | REST/GraphQL/SOAP API testing |
API scans skip UI-related tests (e.g., XSS) and focus on HTTP error codes or unusual content types.
Running the API Scan with Docker
Since our Spring Boot service exposes only REST endpoints, we’ll use the API scan. This example mounts your working directory to collect reports and any custom rules.$HOST_URLand$PORTshould point to your running Spring Boot application.-c custom_rules.confis optional; omit if you don’t need overrides.
Ensure the API definition is reachable (no authentication required) when running scans. Firewall or incorrect URLs can cause false failures.
Sample Scan Output
Docker Command Arguments
| Flag | Description | Example |
|---|---|---|
| -v | Mount current directory for reports and custom configs | -v $(pwd):/zap/wrk/:rw |
| -t | Target API definition URL (include protocol) | -t http://localhost:8080/v3/api-docs |
| -f | Format of API definition: openapi, soap, or graphql | -f openapi |
| -c | Custom rules configuration file | -c custom_rules.conf |
| -r | Output report format: report.html, report.md, report.xml, report.json | -r zap-report.html |