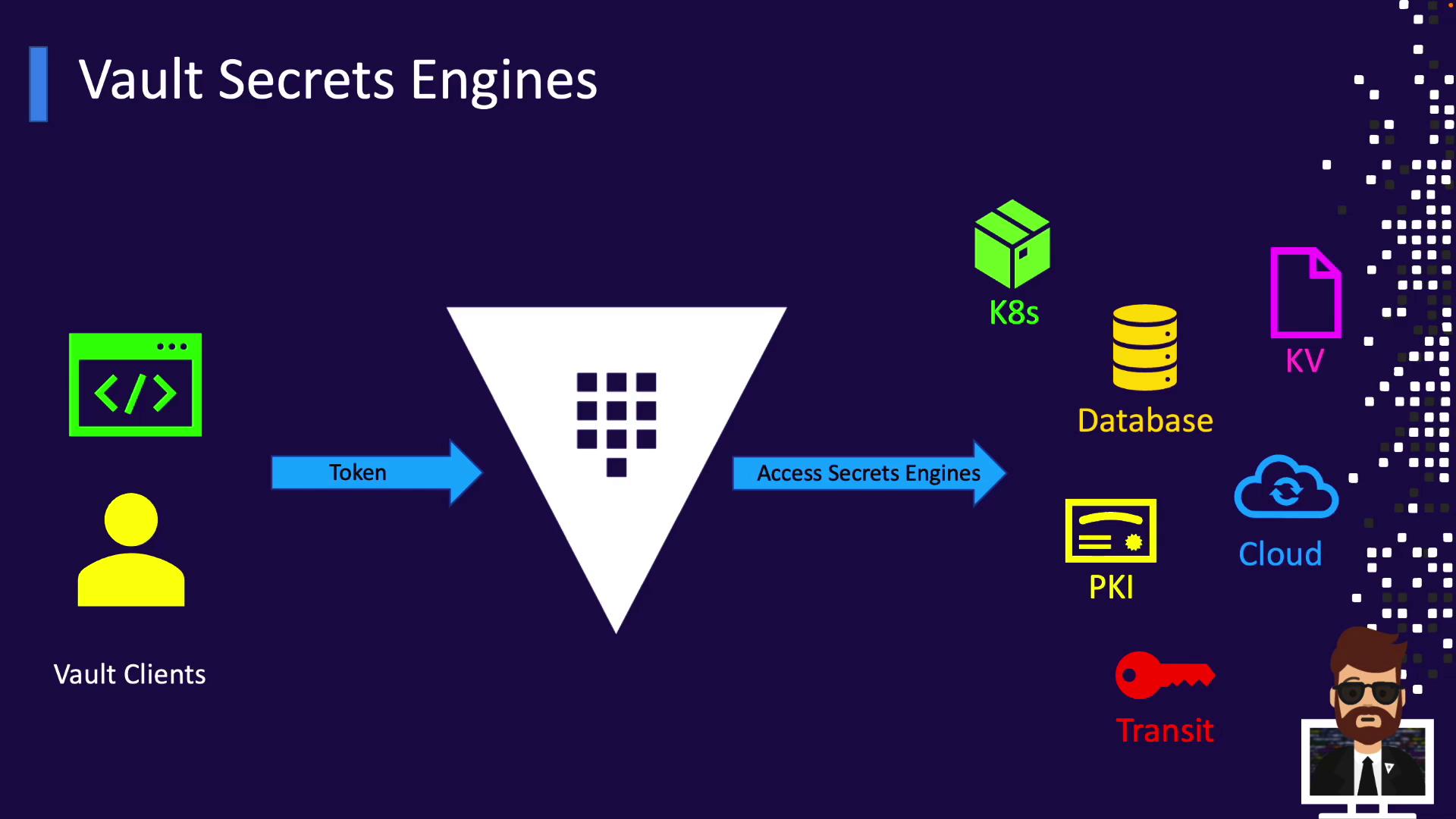
Secrets Engines are the primary reason to deploy Vault. They deliver on Vault’s promise: centralized, dynamic, and secure management of sensitive information.
What Are Secrets Engines?
A Secrets Engine is a plugin-style component in Vault that you enable at a specific mount path. Each engine can:- Store static key/value data
- Generate dynamic credentials on demand
- Encrypt/Decrypt data (via the Transit engine)
- Issue certificates (via the PKI engine)

Defining a Secret
A secret is any piece of data your organization considers sensitive:- Usernames and passwords
- API keys, tokens, or SSH credentials
- TLS certificates and private keys
- Database credentials
- Application configuration files

- Dynamic Credentials: Unique, short-lived credentials reduce blast radius.
- Automatic Revocation: Secrets expire at the end of their lease.
- Audit Trails: Full visibility into who accessed what and when.
Scenario: A fleet of web servers requests dynamic database credentials from Vault. If one server is compromised, only its credentials are affected. You can pinpoint and revoke its credentials without impacting others.
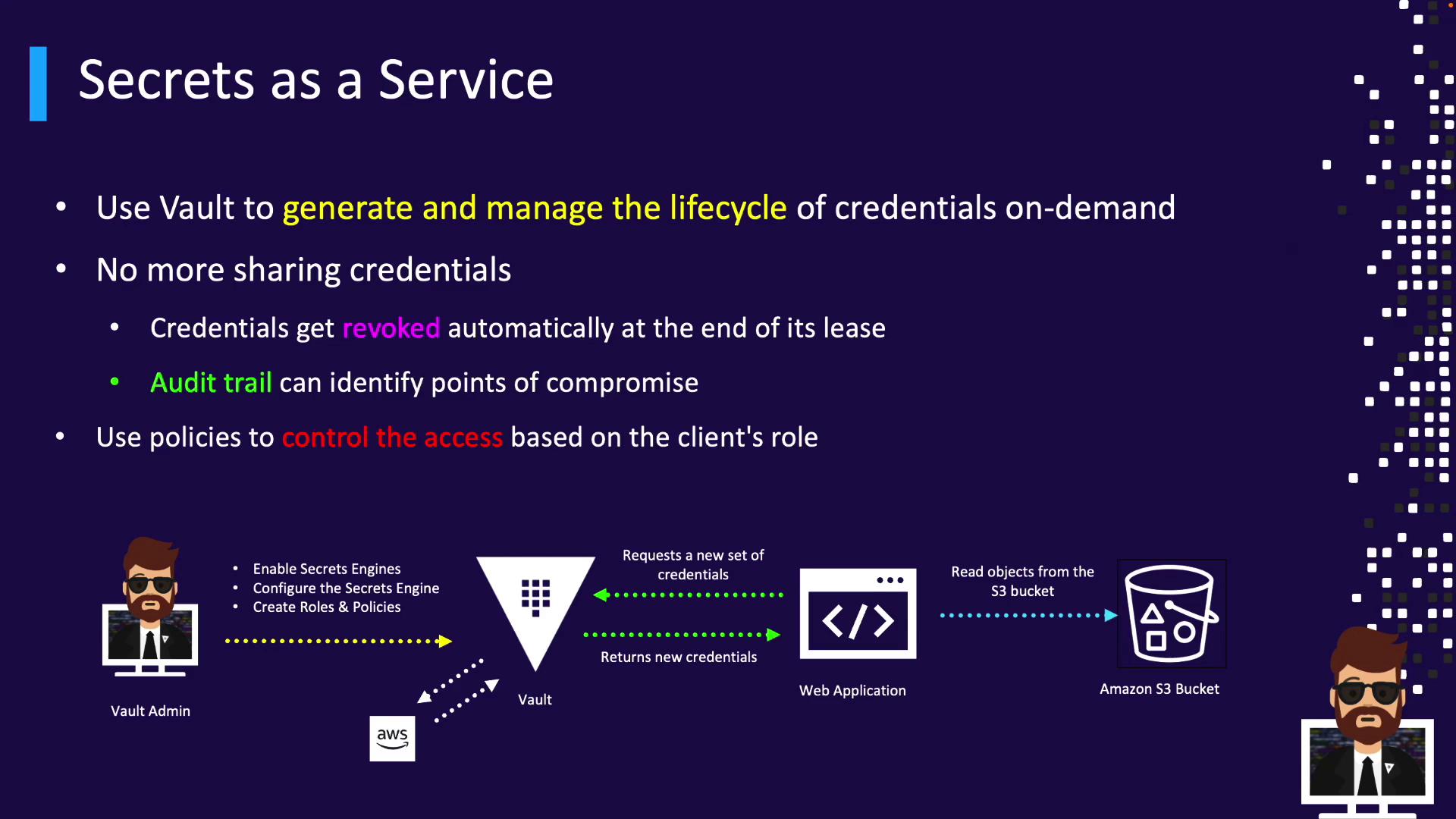
Dynamic Credentials Workflow
- Application Request
The web app requests AWS credentials from Vault’s AWS Secrets Engine. - Credential Generation
Vault dynamically creates IAM credentials tied to a lease. - Use of Credentials
The application uses these to access AWS services (e.g., S3). - Automatic Revocation
Credentials expire and are revoked at the end of their lease.
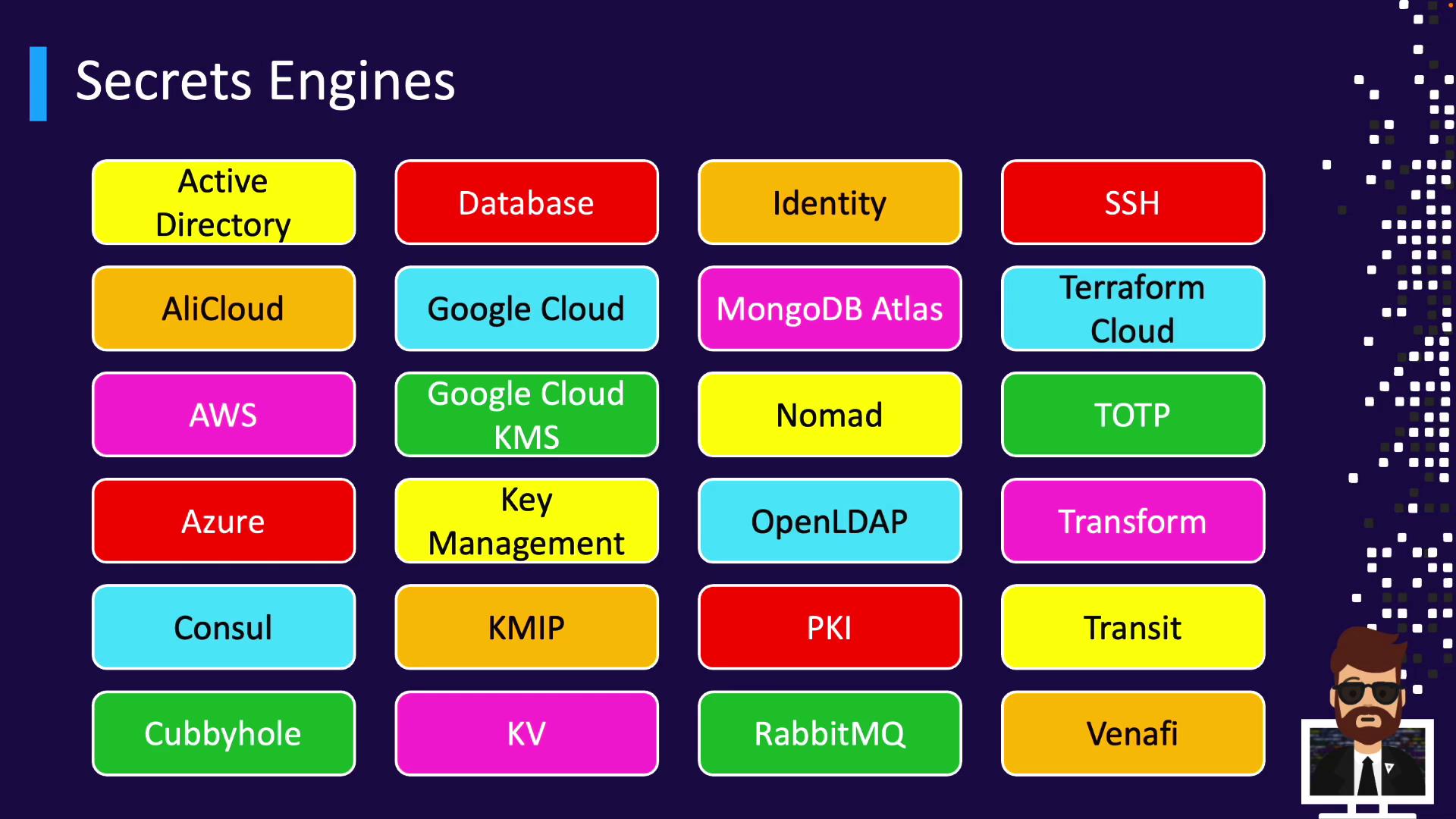
Built-In Secrets Engines
Vault includes a broad set of engines by default. Select and enable the ones you need:| Category | Examples |
|---|---|
| Cloud Platforms | AWS, Azure, Google Cloud, Alibaba Cloud |
| Databases | MySQL, PostgreSQL, MongoDB, Oracle, Cassandra, Snowflake |
| Identity & Access | Active Directory, Consul, OpenLDAP, Cubbyhole |
| Key Management | AWS KMS, Azure Key Vault, GCP KMS, (Enterprise Only) KMIP |
| Encryption & Certificates | Transit, Transform (Enterprise Only), PKI, Venafi |
| Utilities | SSH, TOTP, Terraform Cloud |
Key/Value (KV) Secrets Engine
Use the KV engine to store static data.- KV v1: Overwrites on write; no history.
- KV v2: Versioned store; supports history and rollback.
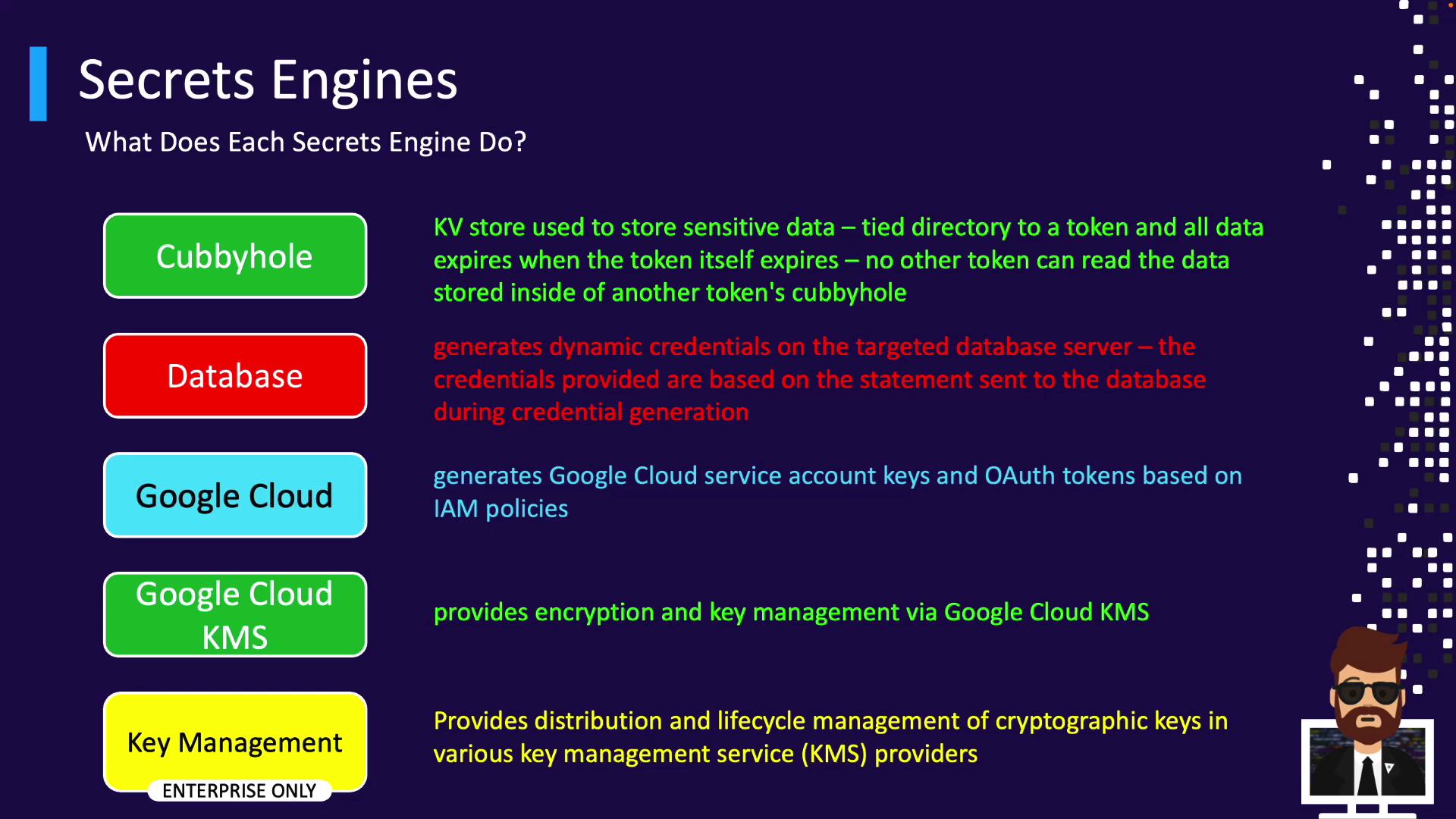
Database Secrets Engine
Dynamically generate database credentials for many backends:- Cassandra, Couchbase, Elasticsearch, HANA DB, InfluxDB
- MongoDB, Microsoft SQL Server, MySQL/MariaDB (Aurora, RDS)
- Oracle, PostgreSQL, Redshift, Snowflake
- Custom database plugins

Key Management and Transform engines are Enterprise Only. Ensure your Vault license includes these features before enabling.
Grouping Secrets Engines by Function
- Cloud Platforms: AWS, Azure, GCP, Alibaba
- Databases: SQL/NoSQL backends
- Identity/Access: Active Directory, Consul, OpenLDAP, Cubbyhole
- Security & Encryption: KMIP, PKI, Transit, Transform, Venafi
- Storage: KV v1 & v2
Overview of Built-In Engines

- Active Directory
Rotate service account passwords; Vault requires a service account for rotation. - Cloud (AWS/Azure/GCP)
Dynamic cloud credentials for resource access. - Consul
Issue ACL tokens programmatically. - Cubbyhole
Token-scoped private storage space. - Database
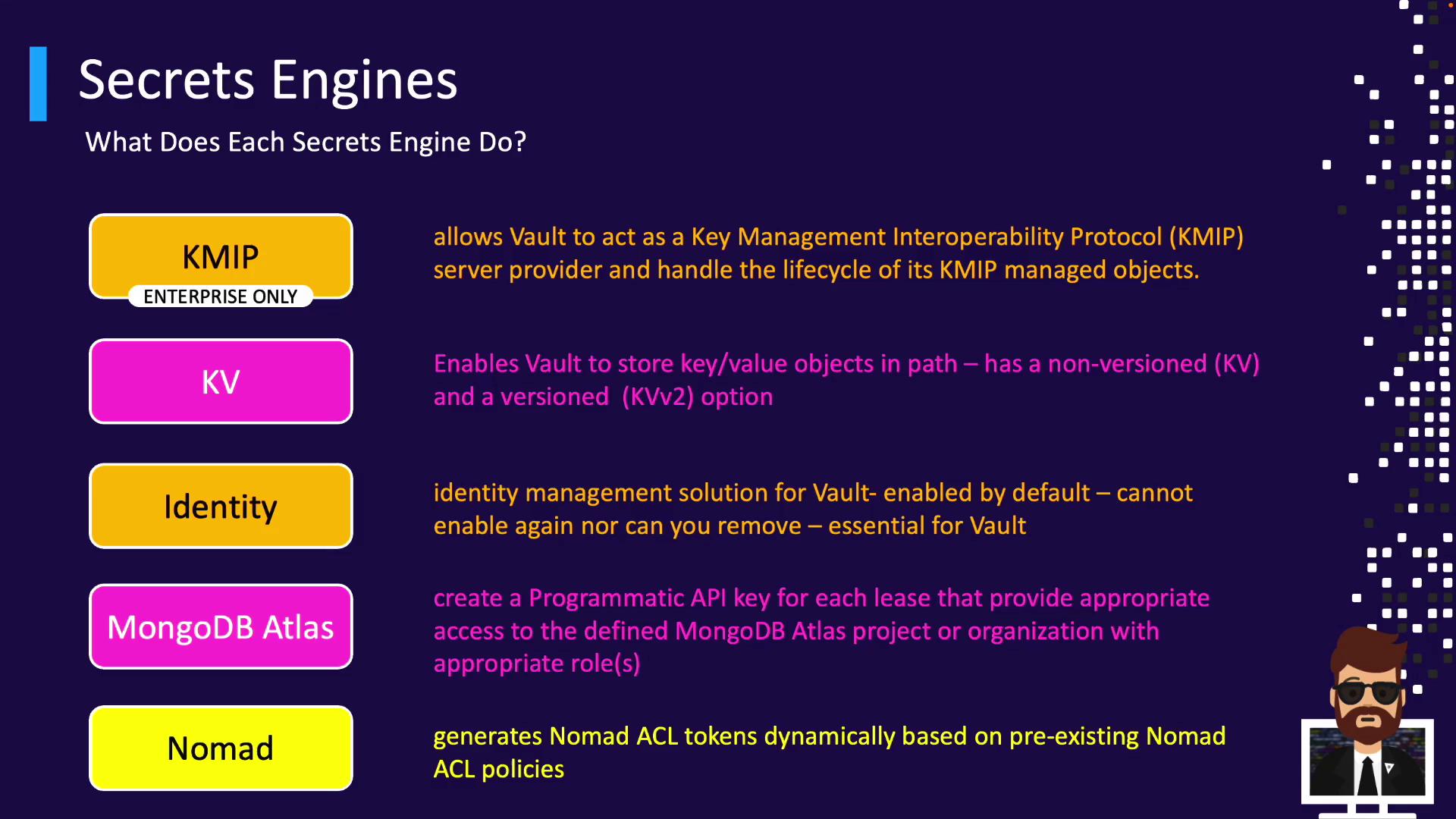
On-demand DB credentials. - KMIP (Enterprise)
Vault acts as a KMIP server for storage encryption. - KV (v1/v2)
Simple vs. versioned key/value storage. - Identity
Built-in identity and group management. - MongoDB Atlas, Nomad, OpenLDAP
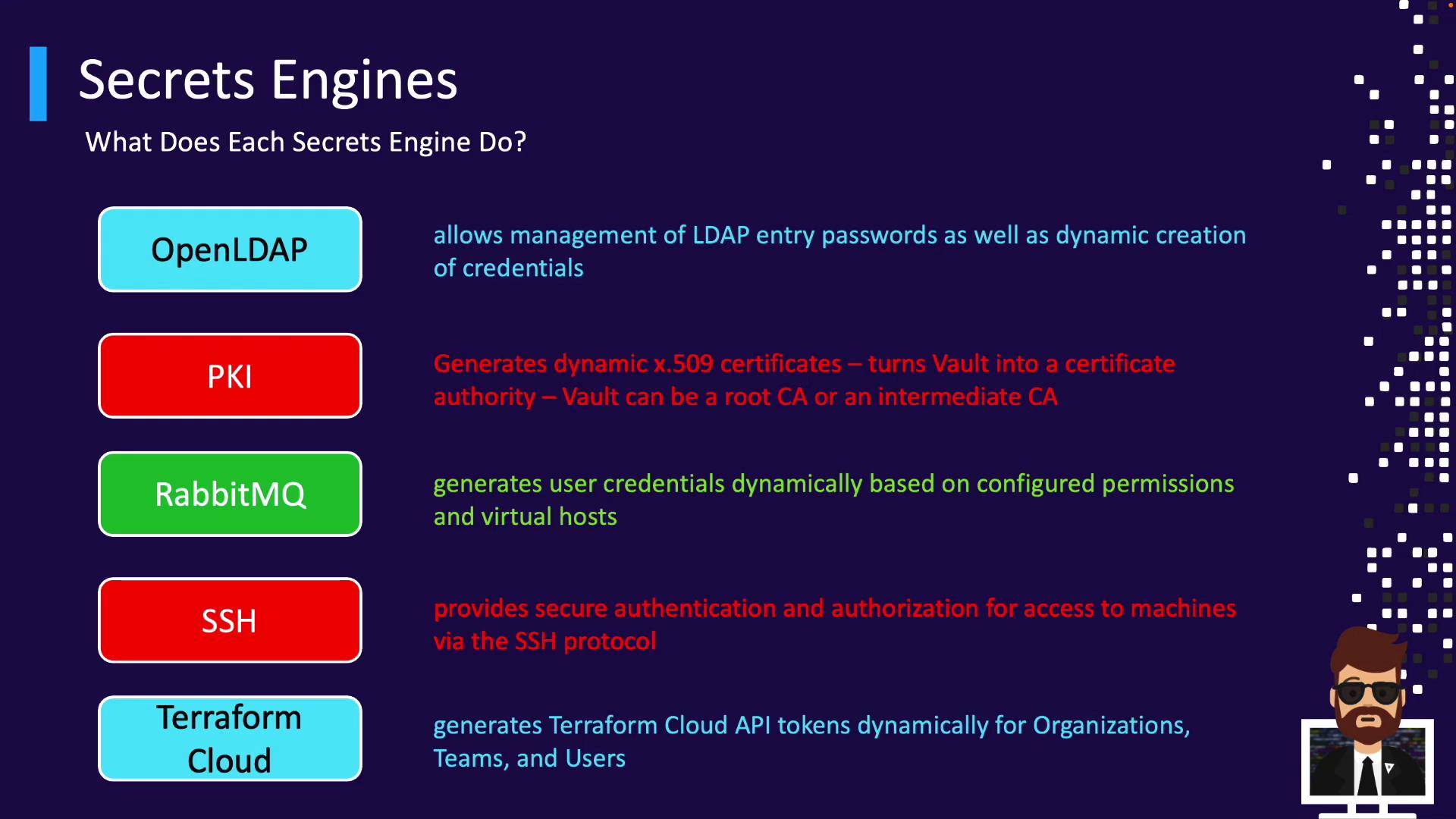
Platform-specific credential generators. - PKI
Vault as a Certificate Authority for TLS/mTLS. - RabbitMQ, SSH, TOTP, Terraform Cloud
Short-lived credentials and tokens. - Transit
Encryption-as-a-service; stateless crypto API. - Transform (Enterprise)
Data tokenization and masking. - Venafi
Certificate issuance via Venafi integration.