Understanding Logging
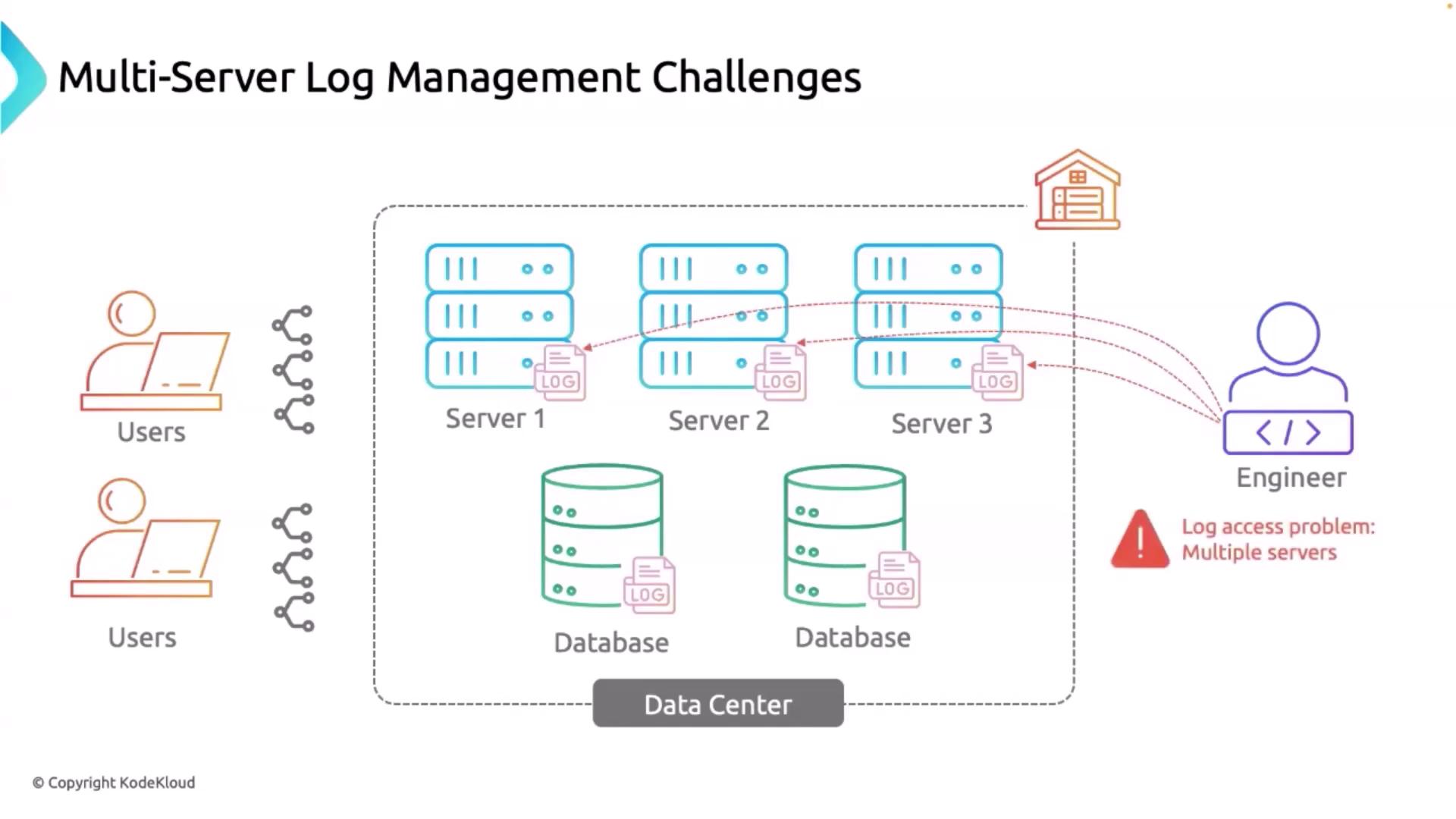
Logging involves the systematic recording of system events, user activities, and application behavior. These logs provide critical insights into system operations, enabling IT teams to diagnose issues faster and secure operations against potential threats. Consider a scenario where users interact with an application hosted across a data center comprising multiple servers and databases. In such environments:- Each interaction generates log data.
- Logs from servers, databases, and applications are inherently different—containing both infrastructure-level and application-specific details.
- The distributed nature of these logs makes it a challenging task for engineers to gather, correlate, and analyze the relevant data efficiently.
The Impact of Modern Architectures on Logging
With the adoption of microservices and containerization technologies such as Docker, the complexity of log management increases. Each microservice, running in its own container, produces its own set of logs—making the aggregation and management of this data a non-trivial task.
Centralizing logging is a best practice in modern IT environments, as it simplifies the process of analyzing logs and enhances the overall security posture of the organization.
The Advantage of Centralized Logging
To overcome the challenges posed by distributed logging, many organizations implement centralized logging systems. By aggregating logs from various sources into a single repository, engineers can:- Easily access and analyze logs,
- Rapidly identify and resolve issues,
- Improve overall system security and operational efficiency.
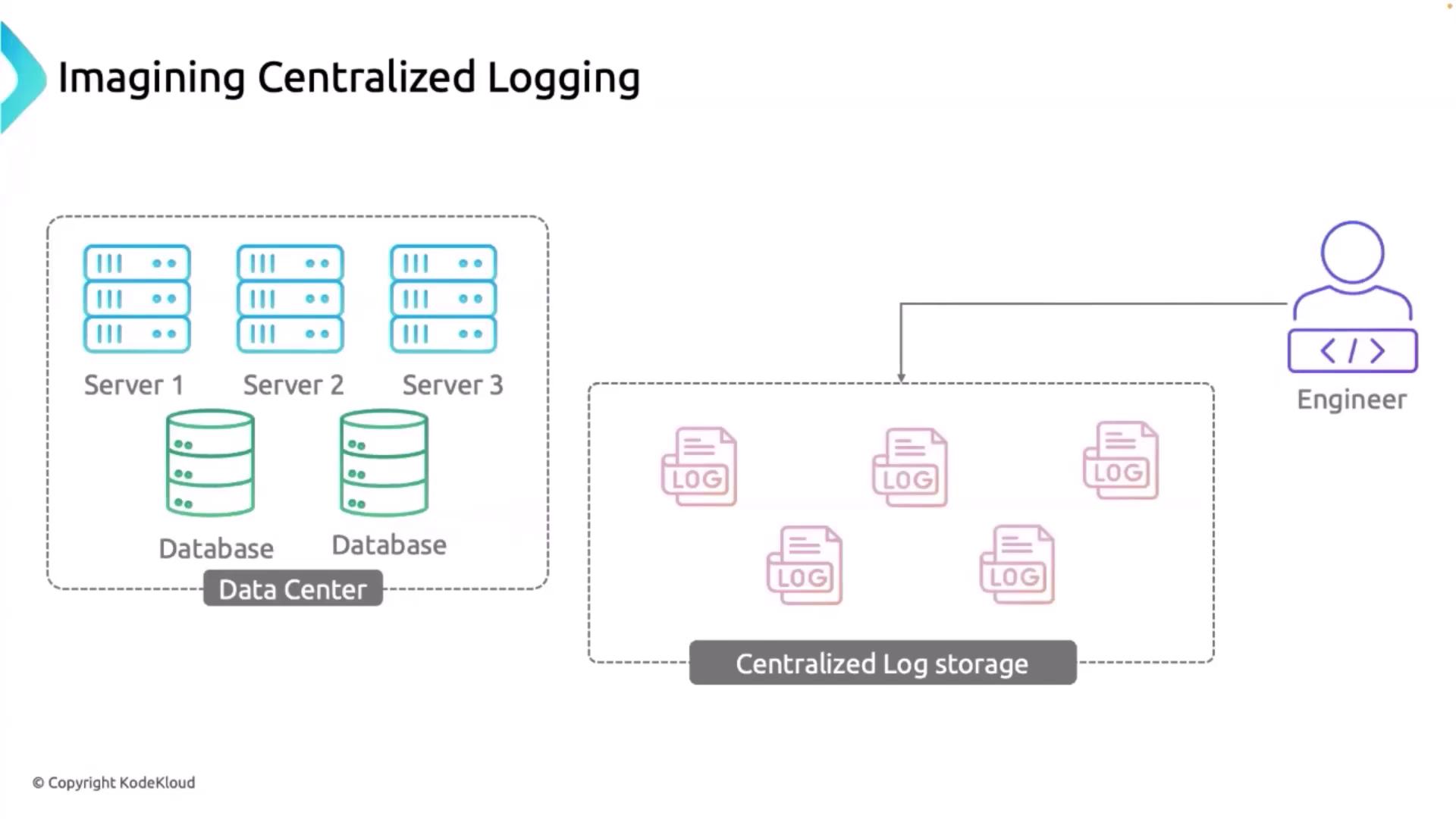
Ensure that your centralized logging system is secured and properly configured to handle the volume of log data generated by diverse sources across your infrastructure.
Key Takeaways
Centralized logging is essential for:| Feature | Benefits | Example Application |
|---|---|---|
| Multi-source Log Aggregation | Simplifies the process of data analysis | Collecting logs from web servers, databases, and microservices |
| Enhanced Troubleshooting | Improves rapid detection and resolution of issues | Correlating events across disparate systems |
| Improved Security Monitoring | Enables proactive threat detection | Real-time monitoring and alerting systems |