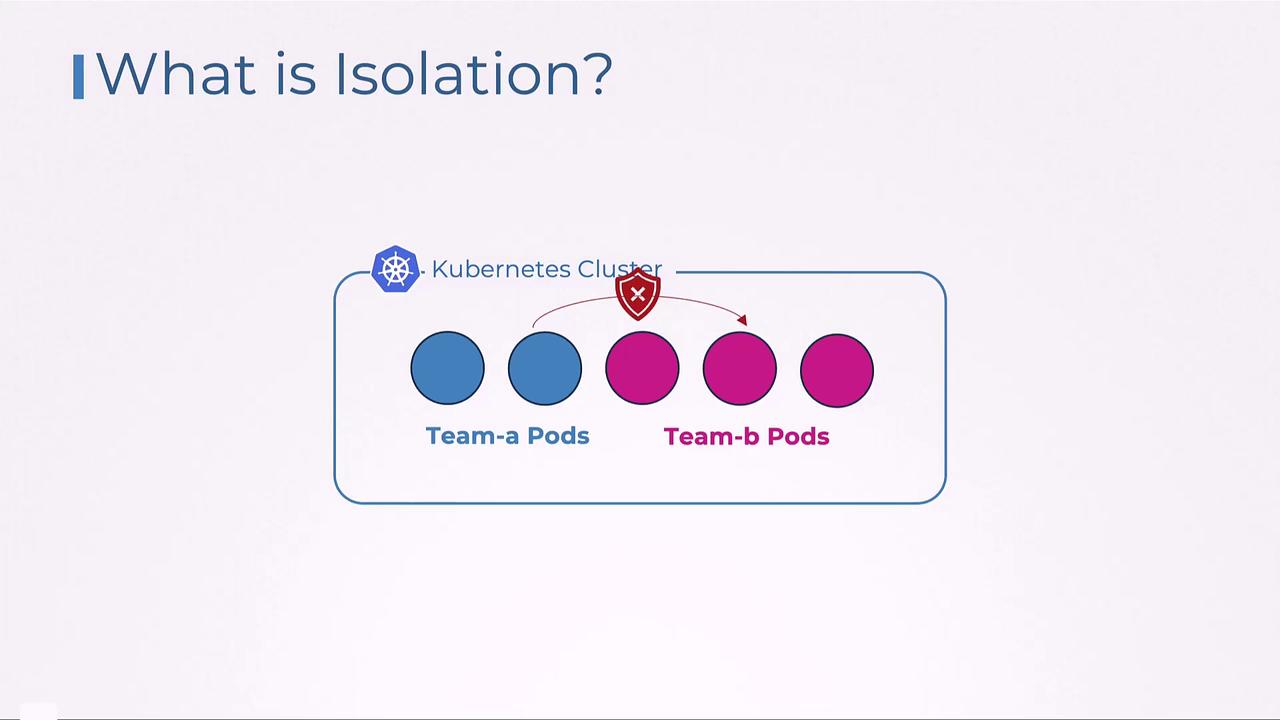
- Control Plane Isolation: Implemented using namespaces and access control mechanisms such as Role-Based Access Control (RBAC).
- Data Plane Isolation: Managed via network policies, storage isolation, and node isolation.
Namespaces divide a Kubernetes cluster into logical sections, ensuring that each team or project can manage its resources independently.
Namespace Isolation
Think of namespaces as different office spaces within a large building. Each team, department, or customer is allocated its own office with dedicated resources, but they still share common infrastructure like electricity and water. In Kubernetes, namespaces allow each team to have isolated resources without affecting other teams.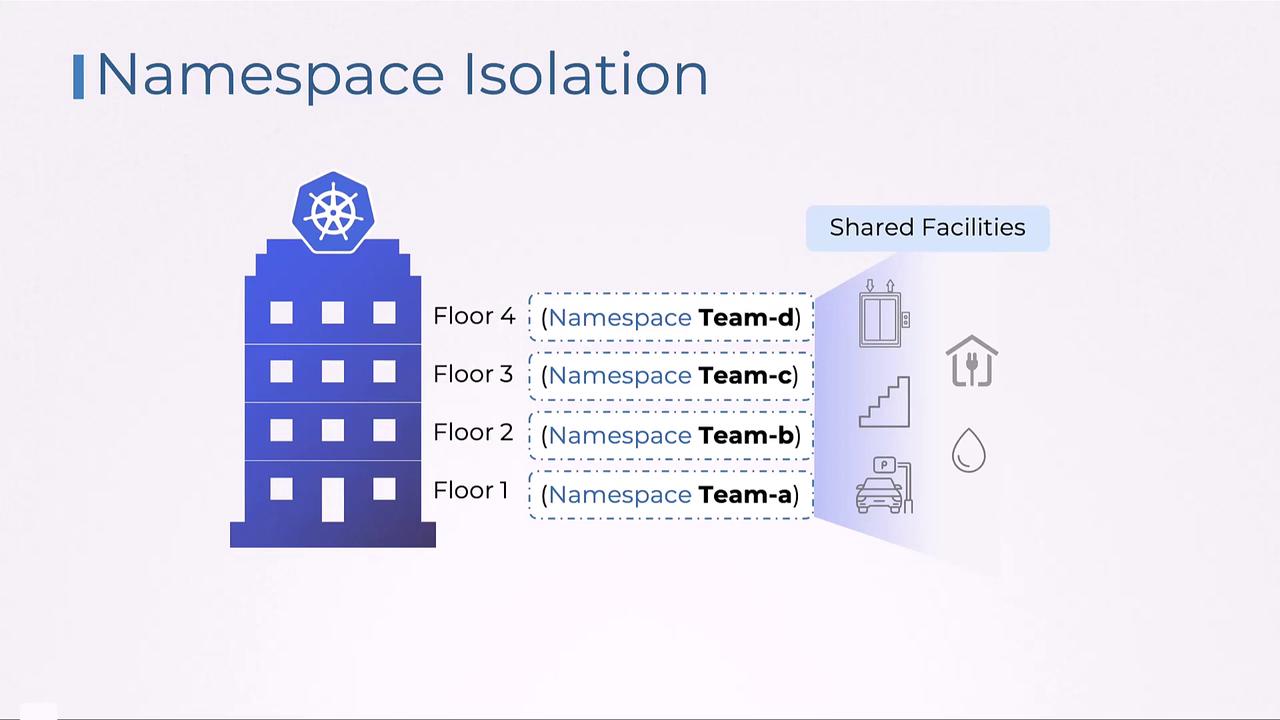
Pod Isolation
Within each namespace, pods serve as individual workspaces. A pod is a set of one or more containers that closely share resources, similar to employees sharing a desk workspace. Although containers within a pod collaborate, different pods remain isolated to securely allocate resources and limit interference.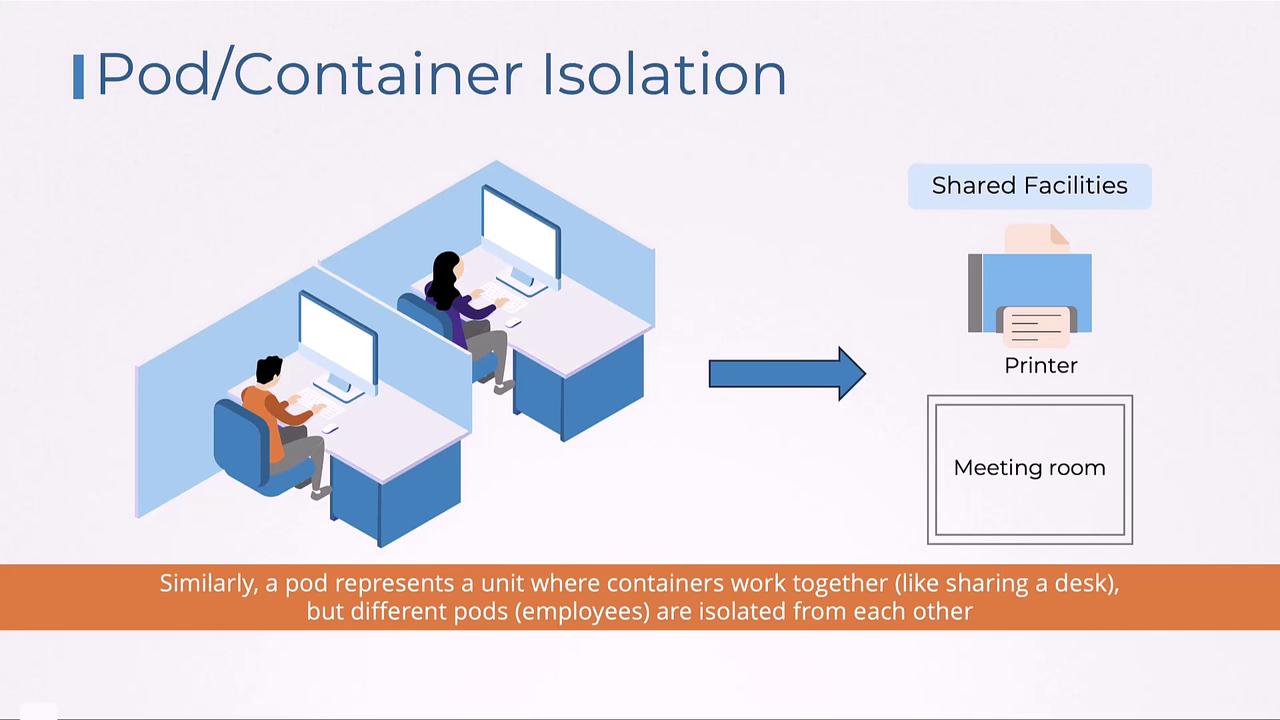
Network Isolation
Just as an office building might have exclusive meeting rooms or secure network segments, Kubernetes employs network policies to restrict communication between pods. These rules ensure that only allowed pods interact, maintaining security within the internal network.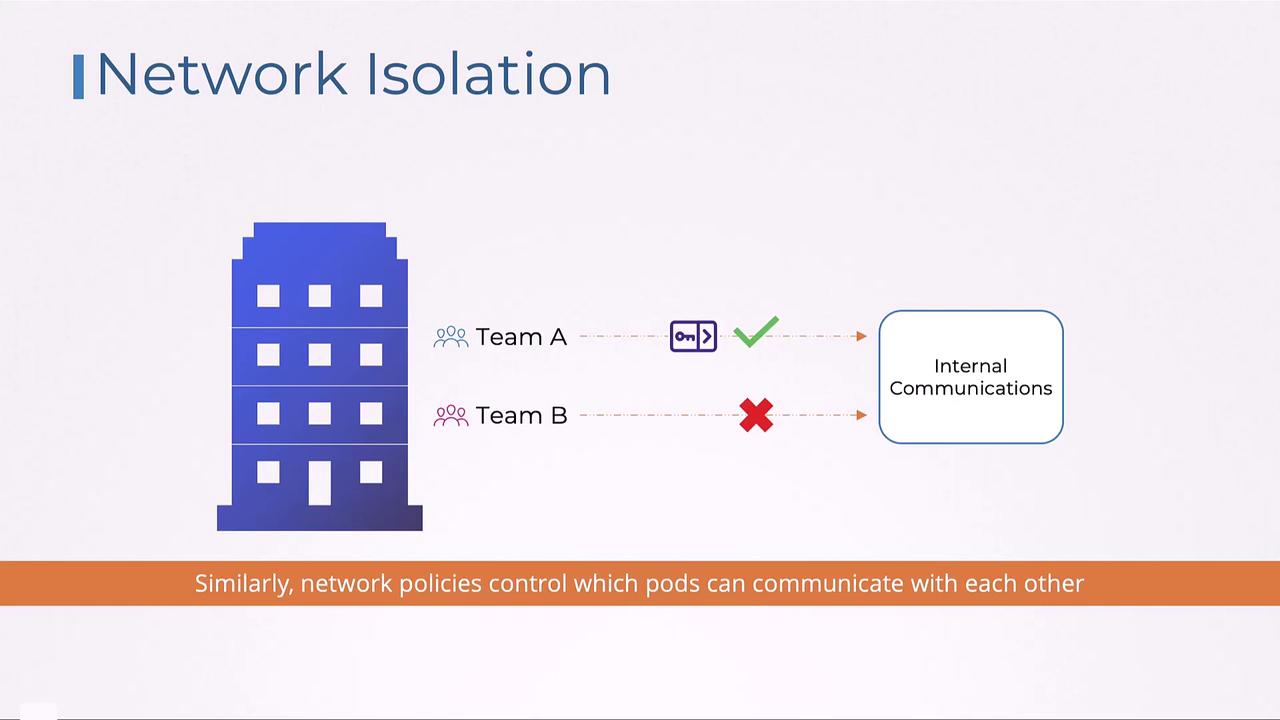
Node Isolation
Nodes in a Kubernetes cluster can be compared to floors in a building. Each floor (node) can host multiple teams under strict access policies or, in some cases, be dedicated entirely to a single team. This approach further enforces isolation at the infrastructure level.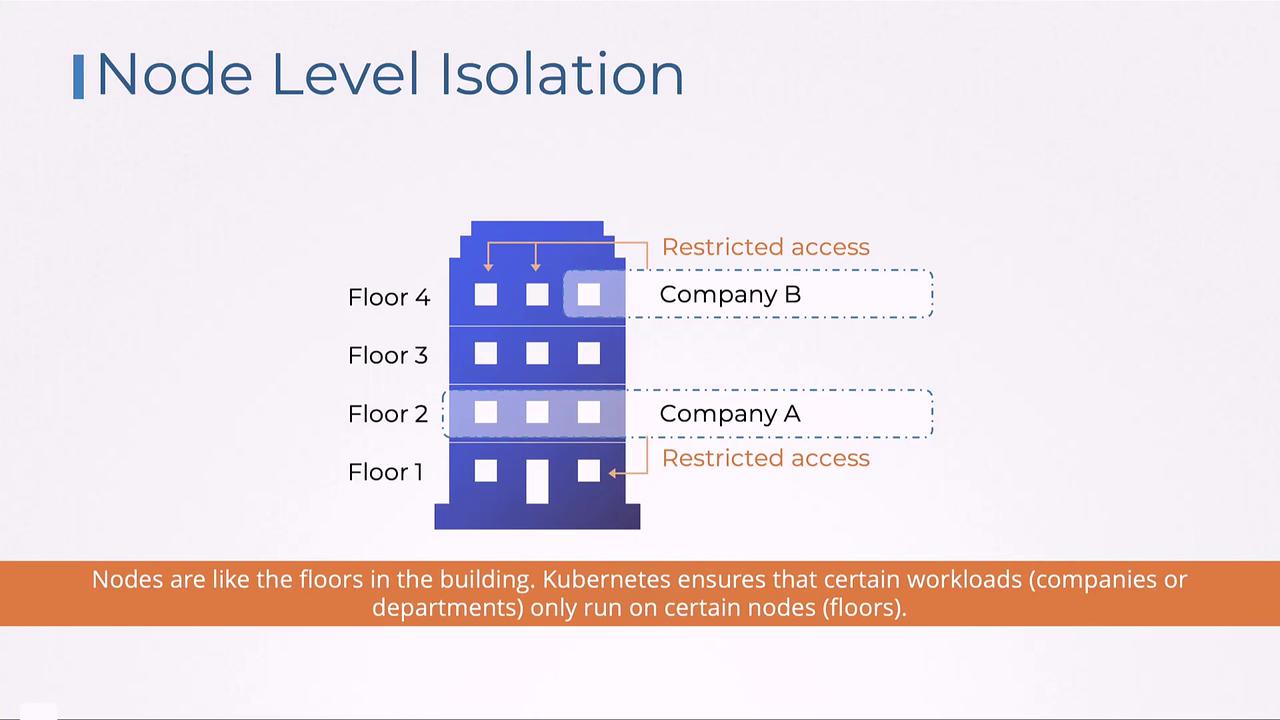
Hard Isolation vs. Soft Isolation
Kubernetes supports two primary models of tenant isolation:Hard Isolation
Hard isolation involves dedicating physical or virtual infrastructure to each tenant so that compute, storage, and networking resources are not shared. This model guarantees complete segregation of workloads.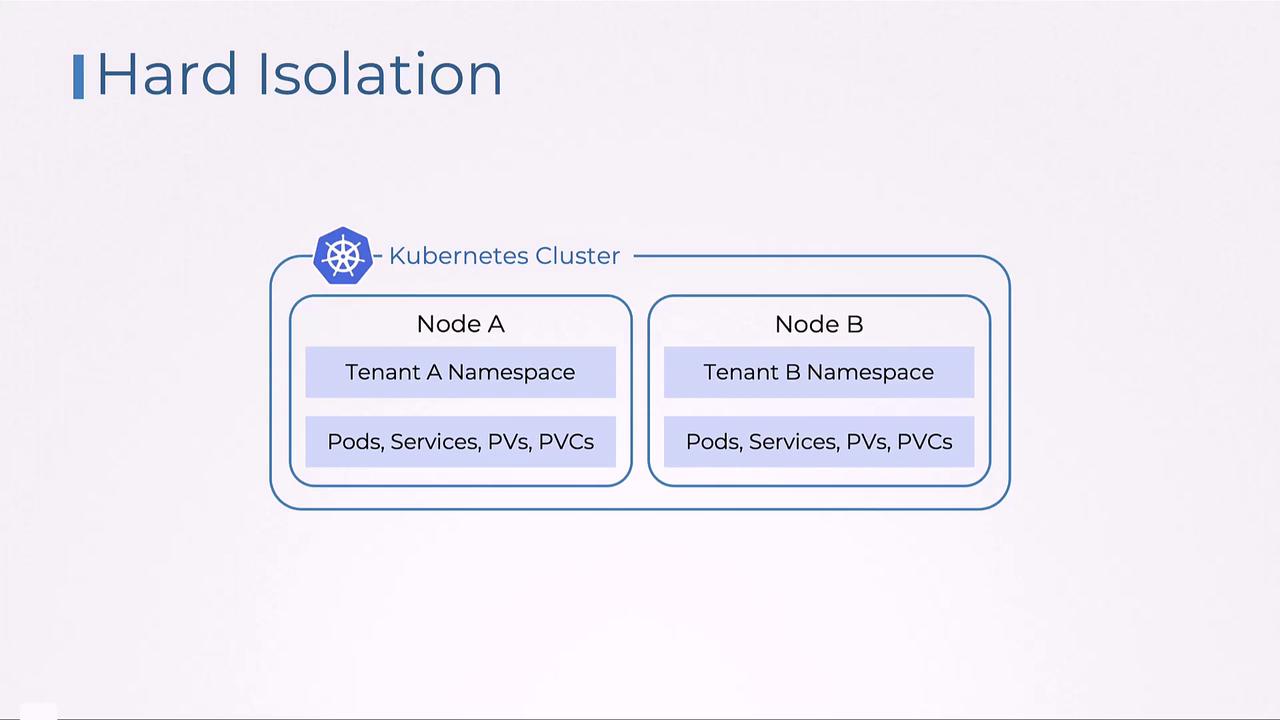
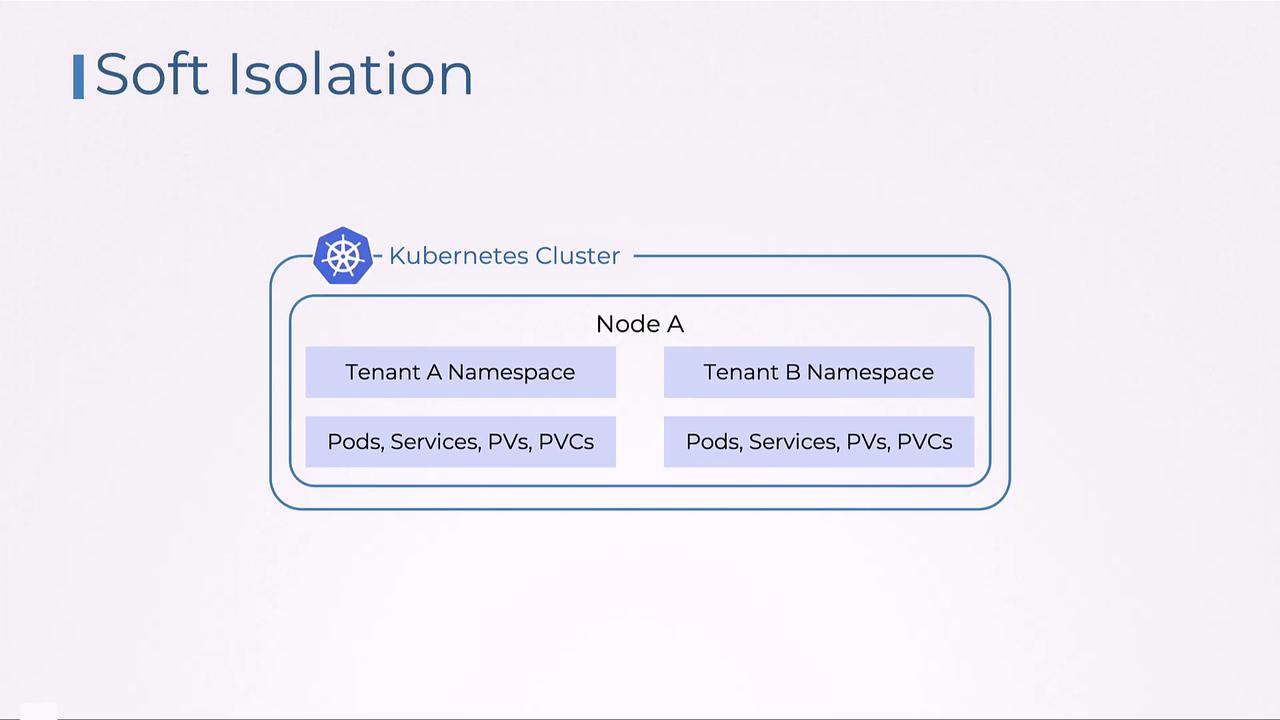
Soft Isolation
Soft isolation, on the other hand, allows tenants to share the underlying infrastructure while enforcing logical separations using namespaces. Resource quotas and limits prevent any single tenant from consuming too much of the cluster’s resources, and network policies continue to define clear communication boundaries.