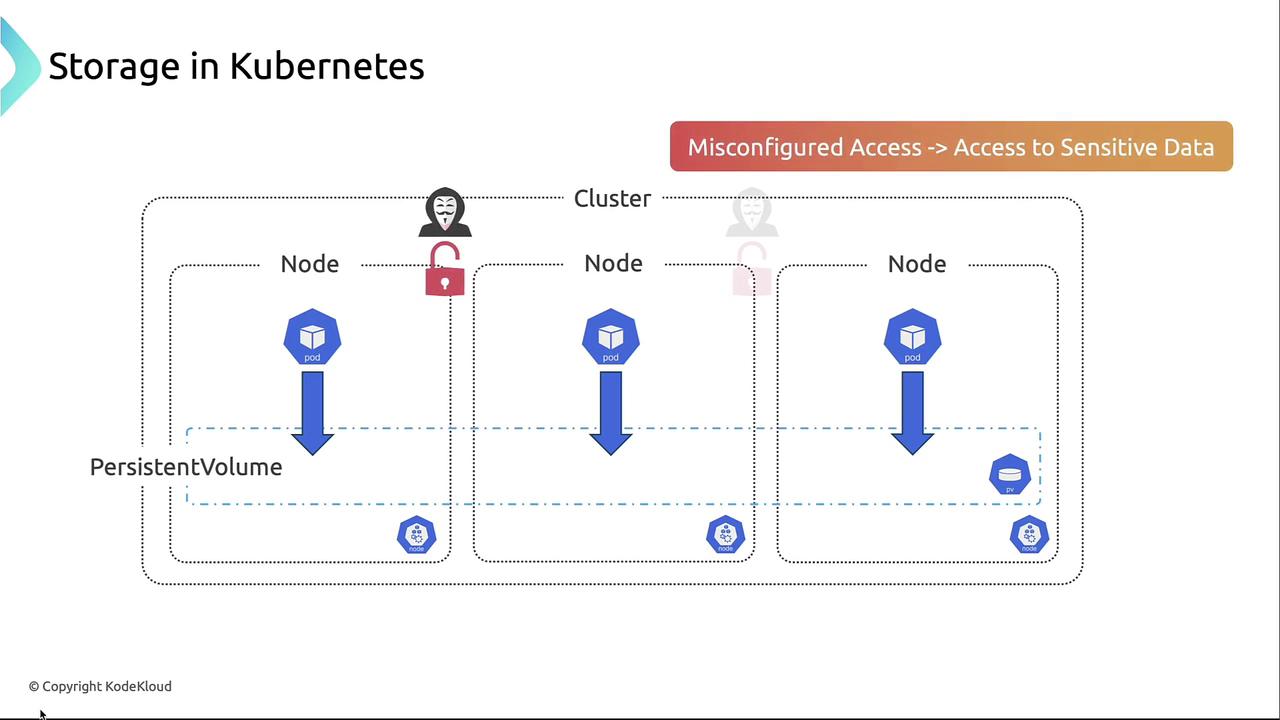
Unencrypted or improperly scoped storage access can allow attackers to read, modify, or destroy sensitive data. Always review your storage configurations and access policies.
Encrypting Data at Rest and in Transit
Encrypting both disk data and network traffic prevents unauthorized access and eavesdropping. Kubernetes natively supports etcd encryption, and most cloud providers offer disk-level encryption:| Provider | Encryption Feature | Reference |
|---|---|---|
| AWS EBS | Customer-managed keys for EBS volumes | https://aws.amazon.com/ebs |
| Azure Disk Storage | Server-side encryption with platform or customer-managed keys | https://azure.microsoft.com/services/managed-disks/ |
| Google Cloud Persistent Disk | CMEK/Customer-supplied encryption keys | https://cloud.google.com/persistent-disk |
Ensure your cloud IAM policies grant permissions to use the specified encryption keys.
Role-Based Access Control (RBAC) for Storage
Restrict access to StorageClasses, PVs, and PVCs using Kubernetes RBAC. Define granular roles and bind them to users or service accounts.get, list, create, delete), you minimize the blast radius of compromised credentials.
StorageClasses and Policy Enforcement
StorageClasses let you standardize storage parameters—such as encryption, IOPS, and backup policies—across your cluster.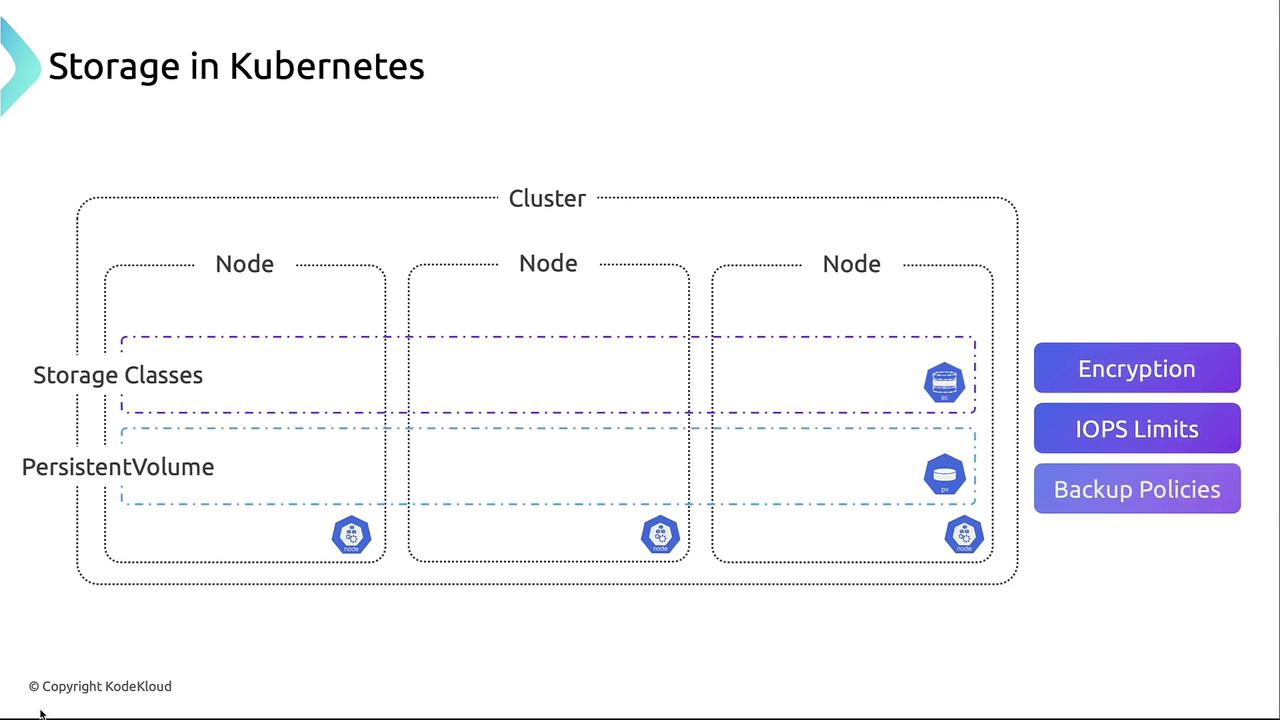
- Decouple storage parameters from application manifests
- Enforce organizational policies (encryption, throughput, retention)
- Simplify provisioning for developers
Backup and Disaster Recovery
Implement automated backups and cross-cluster replication to guard against data loss, corruption, and ransomware.
| Tool | Description | Link |
|---|---|---|
| Velero | Open source backup, restore, and disaster recovery | https://velero.io |
| Portworx | Enterprise-grade storage management and DR | https://portworx.com |
| OpenEBS | Containerized storage with snapshot and clone features | https://openebs.io |
| Kasten | Policy-driven backup and mobility for Kubernetes volumes | https://www.kasten.io |
Monitoring Storage Health and Security
Track storage metrics and access patterns to detect anomalies early. Use Prometheus for data collection and Grafana for visualization.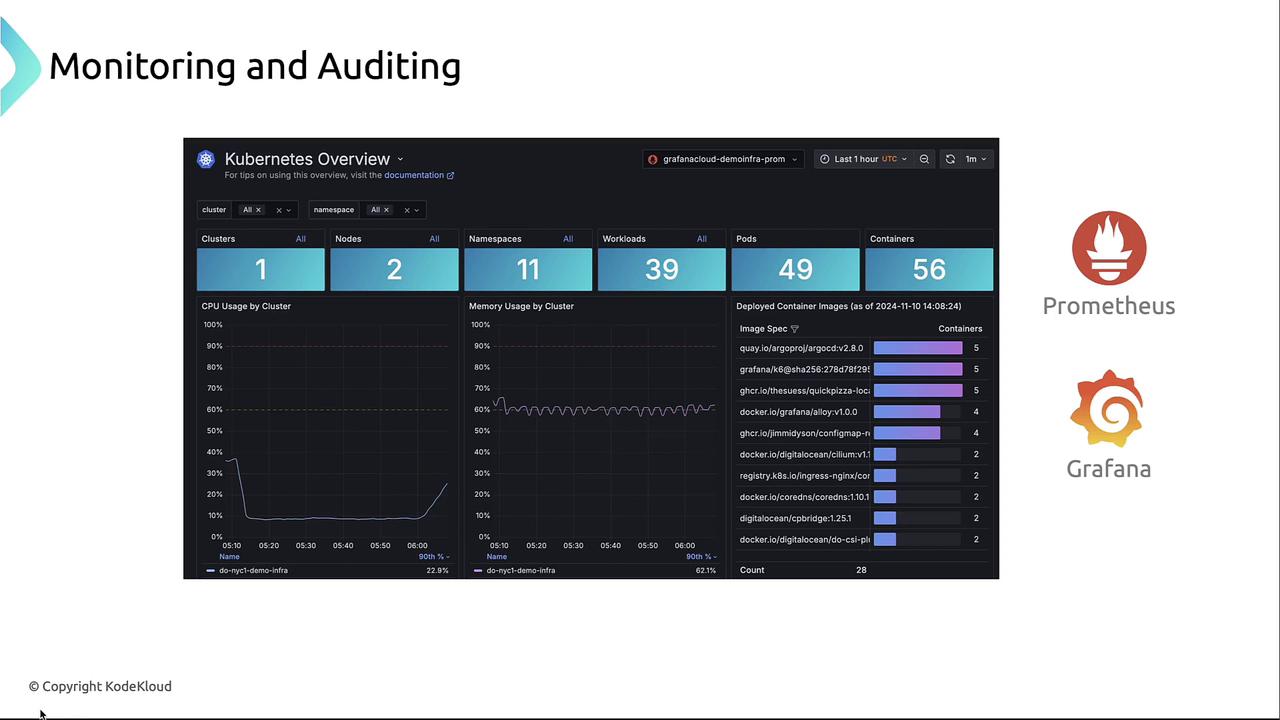
- Volume latency and throughput
- PVC capacity versus usage
- I/O error rates
- Unauthorized mount or delete attempts
Summary

- Encrypt data at rest and in transit
- Enforce RBAC for storage resources
- Standardize storage parameters with StorageClasses
- Automate backups and disaster recovery
- Monitor storage metrics and access patterns