Secure Communication and Identity Verification
When a service starts, it must authenticate itself to the mesh control plane before it can begin serving traffic securely. The following steps outline the process:- The Istio agent creates a private key and generates a Certificate Signing Request (CSR).
- The CSR, along with the agent’s credentials, is transmitted to the Istio control plane (istiod).
- The built-in certificate authority (CA) within istiod validates the credentials included in the CSR.
- Upon successful validation, the CA signs the CSR and issues a certificate.
- The Istio agent forwards the signed certificate and its private key to Envoy.
- The agent continuously monitors the workload certificate to track its expiration.
- The process is periodically repeated to enable smooth certificate and key rotation.
For enhanced security in production-grade clusters, consider integrating a production-ready Certificate Authority (CA) such as HashiCorp Certified: Vault Associate Certification. This setup allows you to manage certificates securely on an offline machine.
Certificate Management Workflow Diagram
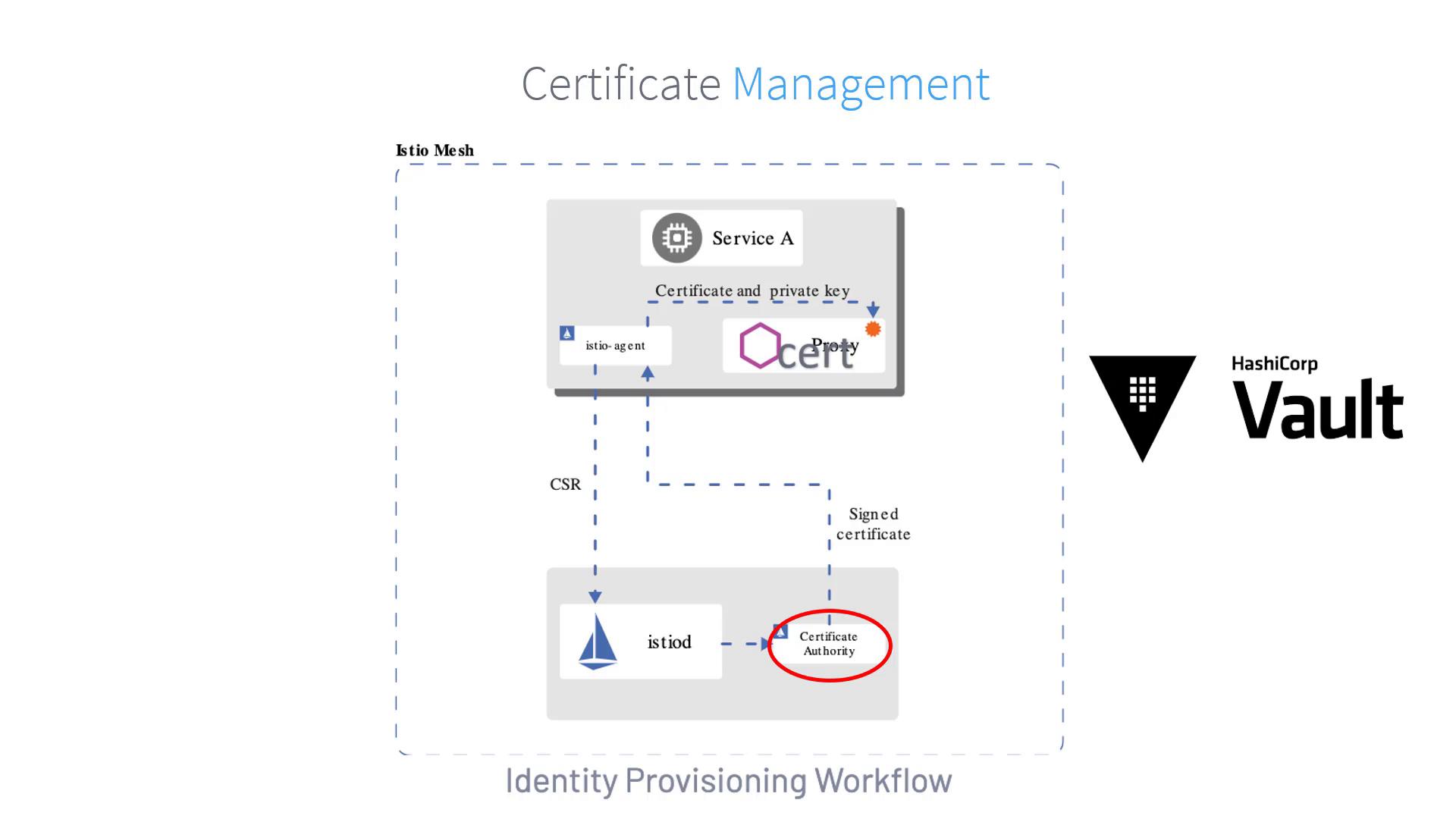
- The istio-agent generates and sends the CSR.
- The istiod validates and signs the certificate.
- The signed certificate and private key are then supplied to Envoy.
- Continuous certificate monitoring and periodic rotation ensure ongoing security.